December 2023
- Patch Tuesday – 12/12
- Windows Server 2012 Officially End Of Support
- Apple’s Busy Year Continues
- 23andMe Changes Terms of Service Following Massive Breach, Leading to Lawsuits
- Package Delivery Scams Flourish During Holiday Season
- Social Media Stirs Fears of Amazon Compromise
- 2023’s Hottest Holiday Scam-Brushing
Advanced would to wish you and yours a very Happy and Safe Holiday Season
As always, Advanced is proud to be here for all your security needs. Reach out now ([email protected]) to determine how you can improve your security posture and keep your business running!
– The Advanced Security Task Force
| Patch Tuesday – 12/12 |
The 2nd Tuesday of every month is Patch Tuesday! Every Patch Tuesday, Microsoft addresses security vulnerabilities in their products via a large deployment of software updates. This month’s Patch Tuesday addressed 37 security vulnerabilities. The full list can be seen here. This round of updates addressed (1) “Zero-Day Vulnerability”. Zero-Day Vulnerabilities are publicly disclosed vulnerabilities that had no prior fix available.
Of the 34 vulnerabilities addressed, four were regarded as critical. The critical updates can be seen below:
- CVE-2023-36019: Microsoft Power Platform Connector Spoofing Vulnerability
- CVE-2023-35630: Internet Connection Sharing (ICS) Remote Code Execution Vulnerability
- CVE-2023-35641: Internet Connection Sharing (ICS) Remote Code Execution Vulnerability
- CVE-2023-35628: Windows MSHTML Platform Remote Code Execution Vulnerability
The zero-day vulnerability addressed can also be seen below:
- CVE-2023-20588: AMD: CVE-2023-20588 AMD Speculative Leaks Security Notice
Advanced deploys patches to all environments as a priority following a testing phase. The criticality of security updates is determined by several factors, primarily the ease of exploitability by threat actors and if the vulnerability has been seen exploited in the wild.
| Windows Server 2012 Officially End Of Support |
- On October 10th, Windows Server 2012 and Windows Server 2012 R2 officially reached end of support. This means the operating system will no longer receive critical security patches.
- Windows Server 2012 is considered one of the most popular server operating systems in the world. The retirement is expected to usher in a new wave of threat actors looking to take advantage of deprecated security features.
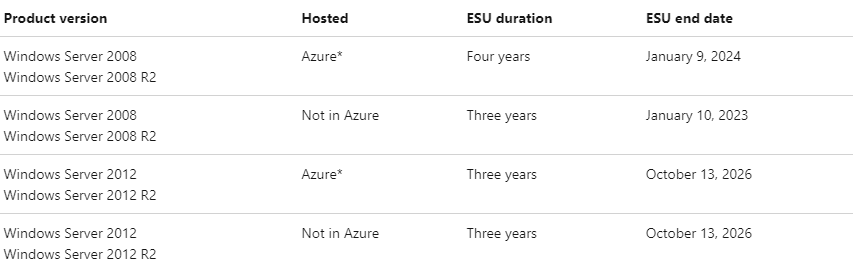
- Those looking to extend coverage to receive critical patches can subscribe to Extended Security Updates (ESUs). ESUs provide up to 3 years of additional coverage for patches deemed ‘Critical’ and ‘Important’ by Microsoft.
- Servers hosted in Azure are eligible for free ESUs until October 13th, 2026. Servers not hosted in Azure are eligible for ESUs until October 13th, 2026 through purchase of an ESU subscription.
- Advanced recommends clients take immediate action on any out-of-date operating systems. For more information on how these changes can affect your environment, reach out to [email protected].
| Apple’s Busy Year Continues |
Apple has released a new round of security updates for various products. Advisories on each product can be seen below:
- Safari 7.2 (Web Browser)
- iOS 17.2 and iPadOS 17.2 (iPhone and iPad Operating Systems)
- iOS 16.7.3 and iPadOS 16.7.3 (iPhone and iPad Operating Systems)
- MacOS Sonoma 14.2 (Mac Operating System)
- MacOS Ventura 13.6.3 (Mac Operating System)
- MacOS Monterey 12.7.2 (Mac Operating System)
- WatchOS 10.2 (Apple Watch Operating System)
- TvOS 17.2 (Apple TV Operating System)
These patches are considered critical and were pushed to devices manually based on impact. Devices with automatic updates enabled installed these patches immediately.
- Analysis of these vulnerabilities (identified as CVE-2023-42916 and CVE-2023-42917) showed a threat actor could run arbitrary code on end user devices through malicious webpages. The end user would only need to visit the webpage to compromise their device. In accordance with Apple’s security policies, additional details on this vulnerability have not been disclosed to protect consumers.
- Due to the severity of these vulnerabilities, the Cybersecurity Infrastructure And Security Agency (CISA) has mandated all Federal Civilian Executive Branch (FCEB) agencies to update their devices as soon as possible.
- This is the 19th and 20th critical zero-day patch of the year for Apple. ACT advises all end users with Apple devices to enable Rapid Security Response updates to receive the latest security patches as soon as possible. To enable Rapid Security Responses on your device, navigate to Settings > General > Software Update > Automatic Updates, then make sure that “Security Responses & System Files” is turned on.

Rapid Security Responses can keep you up to date as soon as patches are available. To enable Rapid Security Responses on your device, navigate to:
- Settings >
- General >
- Software Update >
- Automatic Updates, then make sure that “Security Responses & System Files” is turned on.
- Software Update >
- General >
| 23andMe Changes Terms Of Service Following Massive Breach, leading to lawsuits |
- 23andMe, a genetic testing company that offers services in tracing distant relatives, suffered a data breach in October that was originally estimated to have exposed the personal data of roughly 14,000 individuals (.1% of the customer base).
- An additional investigation has confirmed the scope of the breach to be much larger than originally anticipated, with some figures estimating 6.9 million affected individuals in total. The stolen data included the person’s name, birth year, relationship labels, the percentage of DNA shared with relatives, ancestry reports and self-reported location. This estimate shows that roughly half of 23andMe’s 14 million users were affected.
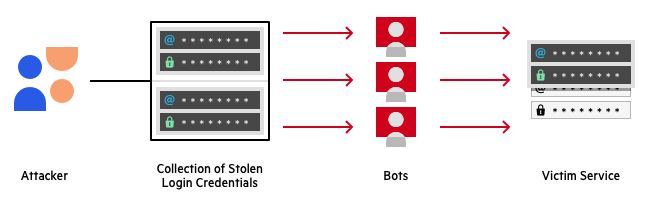
- 23andMe’s internal investigation found that the most likely cause of the breach to be ‘credential stuffing’. Credential stuffing is a common attack in which a threat actor uses a collection of stolen login credentials to attempt to login to various websites. This process is always automated and leverages the likeliness of an end user to repeat usernames and passwords across multiple sites. An overview of this process can be seen below:
- Step 1: A threat actor acquires a list of compromised user accounts and passwords. These are usually captured during data leaks and sold on the dark web or in hacker forums.
- Step 2: A threat actor configures a bot to automatically log into multiple user accounts across various websites.
- Step 3: The threat actor runs an automated process to check if stolen credentials grant access to any web accounts.
- Step 4: The threat actor monitors for successful logins and steals any valuable information.
- Several lawsuits are already in effect against the company, alleging 23andMe changed their terms of service to limit legal exposure following the breach. These changes include a mandatory binding arbitration, which could force users to waive rights to appeal a decision or join a class action lawsuit.
- It is important to note that 23andMe did not have a compromise of any internal systems. The user accounts were accessed legitimately through continued logon attempts. This calls into question if a company is responsible for end users reusing passwords to make accounts easily accessible.
How can we stay safe?
You can prevent suffering an account compromise even if your password is leaked through the following methods:
- Use Multi-Factor Authentication: Multi-Factor Authentication (MFA) uses various sign on methods to verify identity. This requires a combination of something you know (like a password) with something you have (like your phone) or something you are (a biometric factor, like your face or a fingerprint).
- Use a Password Manager: Password managers keep all your passwords stored in one place and protects access to that place through MFA. This prevents end users from re-using passwords and ensures passwords are not easily guessable.
- Use Security Questions: Where applicable, you can configure security questions whenever a logon is detected from an unfamiliar device. Make sure your security questions do not contain easily accessible information (such as the high school you attended or your birthday), but instead focus on personal information (like your favorite food or the place of your first date).
| Package Delivery Scams Flourish During Holiday Season |
- The USPS has advised shoppers to be on the lookout for suspicious text messages this holiday season. A rise has been observed in scams through ‘Smishing’ (Also known as SMS Phishing, or Text Message Phishing).
- Robokiller estimates more than 26% of all text-based scams are regarding package delivery. Often these texts will mention vague information about a package being delayed or requiring further information to continue. Examples of some of these messages can be seen below:
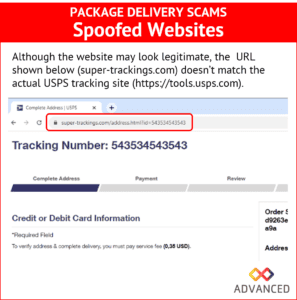
- These links will often lead to spoofed websites, engineered to capture billing information. Below you can see a sample of such a website. Note the URL (super-trackings.com) doesn’t match the actual USPS tracking site (https://tools.usps.com/)
- Once billing information is entered, threat actors will attempt a small fee, typically less than $0.50. This ensures that the credit card information is correct. Once confirmed, the threat actor will move as much as money as possible from the victim’s account.
- USPS will not send customers text messages or e-mails without a customer first requesting the service with a tracking number. Customers can register for text tracking here. Legitimate USPS texts will never contain a link.
- FedEx will never request any personal information via unsolicited mail, email, or text messages. For real time tracking, FedEx offers FedEx Delivery Manager – a secure portal to manage all pending deliveries. You can enroll for this service here.
- Amazon has a feature that allows drivers to interact directly with customers if there is an issue delivering a package. This text message will look like the one shown below:
| Social Media Stirs Fears Of Amazon Compromise |
- A viral post in early December caused a panic for Amazon customers after claiming the company was hacked.
- The post details fraudulent pickup addresses seen on Amazon user accounts. The post theorizes that criminals accessed end user accounts and added these pickup locations to retrieve items ordered under the victim’s Amazon account. An example can be seen below:
- Amazon users quickly checked their pickup locations and noted addresses with which they were not familiar. Customers brought their concern to Amazon and continued to circulate the post.
- Amazon investigated these claims and confirmed that no security breach has been observed. Customers were advised to double check addresses for pickup locations, as most of these were legitimate addresses for Amazon Locker, Amazon Hub Locker, Amazon Fresh and Amazon Counter.
- In an update on December 8th, an Amazon spokesperson noted that a small number of user accounts had seen secure pickup locations added in error, but that no unauthorized orders had been placed. Amazon is currently working to fix the issue. Their notice can be seen below:
| 2023’s Hottest Holiday Scam: Brushing |
- 2023 has seen a massive rise in Amazon review scams. The most common of which is known as ‘Brushing’.
- Brushing is a scam conducted by resellers to accumulate verified positive item reviews to drive legitimate sales. Here’s a step-by-step breakdown of the process:
- Step 1: Scammers, working on behalf of sellers on Amazon, create a one-time use Amazon account. These scammers are called “Brushers”. Their primary goal is to provide positive, verified reviews of a product. Verified reviews require a tracking number and appear at the top of the product page.
- Step 2: Scammers will then place a “This Is A Gift” order for the product they are endorsing (‘Product A’). This will be sent to a legitimate address in the United States. Sending the item as a gift removes the “Return To Sender” Address and makes the package untraceable for the recipient.
- Step 3: Instead of the actual product being endorsed, the seller will then send a random, lightweight product to the victim. This could be any item, as the most important part of the scam is that the seller receives a legitimate tracking number.
- Step 4: The Brusher, with this valid tracking number, can now place a verified product review on product A. This drives up the engagement of Product A and tricks potential buyers into purchasing a lower quality product.
- Amazon estimates that between 40-45% of verified reviews are illegitimate. Amazon recently partnered with Fakespot to confirm legitimacy of products and keep consumers as informed as possible.
- If you have received random products that do not match orders on your Amazon account, customers are encouraged to report the incident here.-Why report these incidents?-While receiving these fraudulent packages for reviews doesn’t indicate a compromise of your Amazon account, it does indicate that malicious threat actors have your address and name. This could be concerning, as this information is already in the hands of an untrustworthy party.
- These fake reviews, which are also done using the victim’s name, can artificially increase the prices of poor-quality goods, as Amazon has been known to change the price of products rapidly depending on demand.
- Can I keep the packages?
- The Federal Trade Commission has confirmed victims are allowed to keep these packages and the seller cannot charge you for the items.
- December 2023 Security Updates
- Windows Server 2012 / R2 Reaches End of Support
- Apple Security Releases
- 23andMe changes terms of service amid legal fallout from data breach
- Smishing: Package Tracking Text Scams
- FedEx: How to rec0gnize and help prevent fraud
- What does this mean: An Amazon driver may contact you by text message or call you for help on the day of delivery
- 2023 Spam Text Statistics: Are Spam Texts on the Rise?
- Malicious ad for USPS fishes for banking credentials
- Brushing Scam: Is This Free Amazon Package Legit?
- Brushing Scams: How they work and how to identify them
Recent Posts


Windows 10 End of Life: Key Considerations
The countdown is almost over-Windows 10 support officially ends on October 14, 2025. If you’re still running Windows 10, now is the time to act.

Cybersecurity Essentials for Healthcare Providers
In today’s increasingly digital healthcare landscape, cybersecurity is no longer optional, it’s essential. With over 184 million patient records compromised in 2024 alone, the stakes