February 2024
- Patch Tuesday -2/13
- Threat Grading Overview
- Deep Dive: SmartScreen Zero Days and Water Hydra-
- Vendor Patch Advisories
- Windows Server 2012 Officially End of Support
- Industry Data: Crowdstrike’s 2024 Global Threat Report
- Emerging Threat: Connectwise’s ScreenConnect Software
- Latest News: Mother of All Breaches
As always, Advanced is proud to be here for all your security needs. Reach out now ([email protected]) to determine how you can improve your security posture and keep your business running!
– The Advanced Security Task Force
| Patch Tuesday – 2/13 |
The 2nd Tuesday of every month is Patch Tuesday! Every Patch Tuesday, Microsoft addresses security vulnerabilities in their products via a large deployment of software updates. This month’s Patch Tuesday addressed 73 security vulnerabilities. The full list can be seen here.
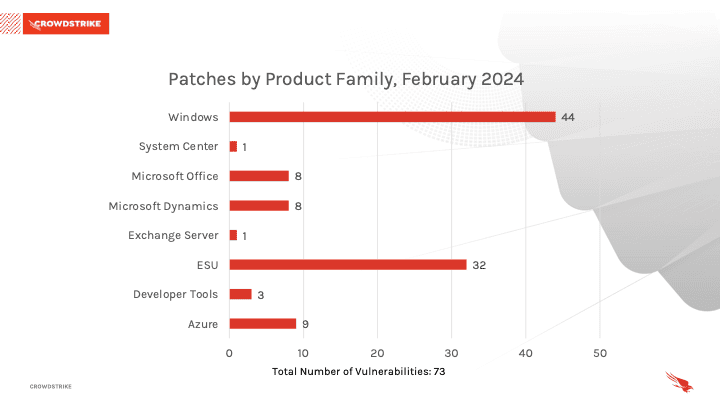
Windows products received the most patches this month with 44, followed by Extended Security Updates (ESU) with 32 and Azure with 9.
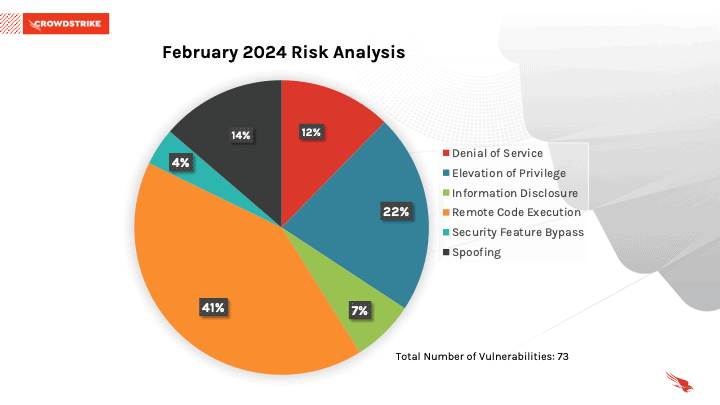
Of the 73 vulnerabilities addressed, 41% addressed Remote Code Execution vulnerabilities. 22% addressed Elevation of Privilege Vulnerabilities, followed by 14% for Spoofing vulnerabilities.
| Threat Grading Overview |
- Microsoft assesses threats based on the theoretical worst possible outcome were a vulnerability to be exploited. The assessment factors in how easily a vulnerability can be exploited, and what damage could be done.

Microsoft also references the Common Vulnerability Scoring System (CVSS), which assesses the severity of a vulnerability on a scale of 0 (Non-Issue) to 10 (Severe Issue) based on 5 key factors:
- Attack Vector: Describes how an attacker can exploit the vulnerability (e.g., local, adjacent network, or network).
- Attack Complexity: Reflects how difficult it is to exploit the vulnerability (e.g., low, medium, or high).
- Privileges Required: Indicates the level of privileges an attacker needs to exploit the vulnerability (e.g., none, low, or high).
- User Interaction: Specifies whether user interaction is required to exploit the vulnerability (e.g., none, required).
- Scope: Determines whether exploitation of the vulnerability impacts components beyond the vulnerable component.
Of these 73 Vulnerabilities, 5 are considered Critical. Details on these can be seen below:
- CVE-2024-21380: Microsoft Dynamics Business Central/NAV Information Disclosure Vulnerability – CVSS Score: 8.0
- CVE-2024-21410: Microsoft Exchange Server Elevation of Privilege Vulnerability – CVSS Score: 9.8
- CVE-2024-21413: Microsoft Outlook Remote Code Execution Vulnerability – CVSS Score: 9.8
- CVE-2024-20684: Windows Hyper-V Denial of Service Vulnerability – CVSS Score: 6.5
- CVE-2024-21357: Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability – CVSS Score: 7.5
| Deep Dive: SmartScreen Zero Days and Water Hydra- |
This round of updates also addressed two Zero-Day Vulnerabilities. Zero-Day Vulnerabilities are publicly disclosed vulnerabilities that had no prior fix available. Microsoft has advised that these vulnerabilities have been actively exploited in the wild.
- CVE-2024-21351: Windows SmartScreen Security Feature Bypass Vulnerability
- Microsoft has fixed an actively exploited Windows SmartScreen vulnerability that allows attackers to bypass SmartScreen security checks.
- Microsoft Defender SmartScreen protects against phishing or malware websites and applications, and the downloading of potentially malicious files. More details can be seen here.
- CVE-2024-21412: Internet Shortcut Files Security Feature Bypass Vulnerability
- The Trend Micro Zero Day Initiative uncovered a vulnerability, CVE-2024-21412, exploited by the Water Hydra (aka DarkCasino) Advanced Persistent Threat group (or APT)
- Water Hydra, active since 2021, primarily targets the financial industry, including banks, cryptocurrency platforms, forex and stock trading platforms, gambling sites, and casinos.
- Water Hydra’s attack chain involved spearphishing campaigns on forex and stock trading forums, employing various lures such as internet shortcuts, PDF files, and JPEG images. An example of a malicious post can be seen below:
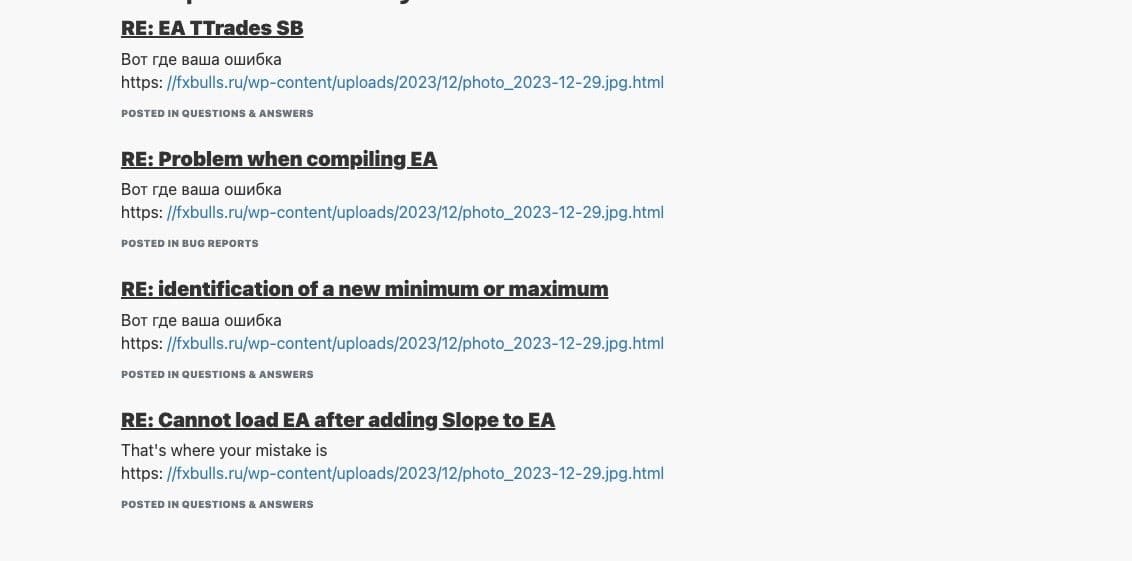
- Clicking on one of these links these would direct the victim to an HTML landing page hosted on a compromised Russian language forex, stock, and cryptocurrency news site hosted on WordPress. This site will then try to open Windows Explorer to maintain persistence on a victim’s PC.
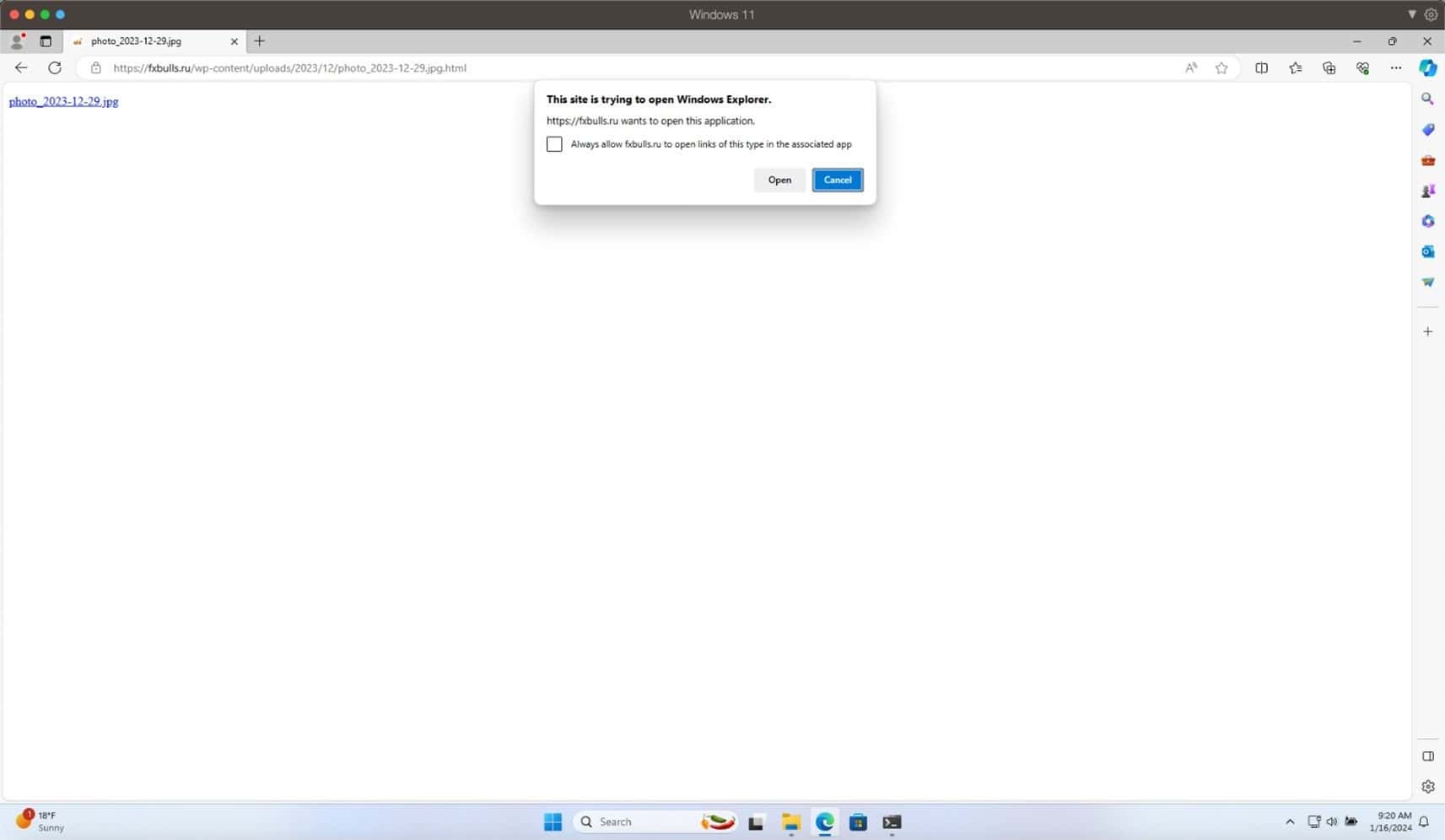
- This .JPEG contains malicious code linking back to a public drive (through WebDAV) that installs malware.
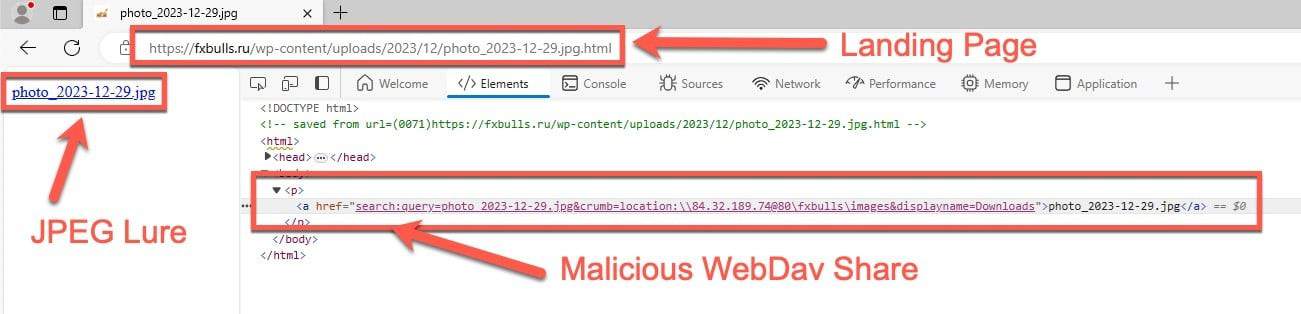
- Access to these WebDAV shares, and the files downloaded, would not warn the end user of impending threats through SmartScreen-a prompt that prevents potentially dangerous files from executing. Once the exploitation is complete, the compromised workstation will connect to a Command And Control (C&C) Server and download a legitimate .JPEG file, which has the same name as the fraudulent .JPEG file used to install malware. This tricks the end user into believing nothing irregular has occurred.
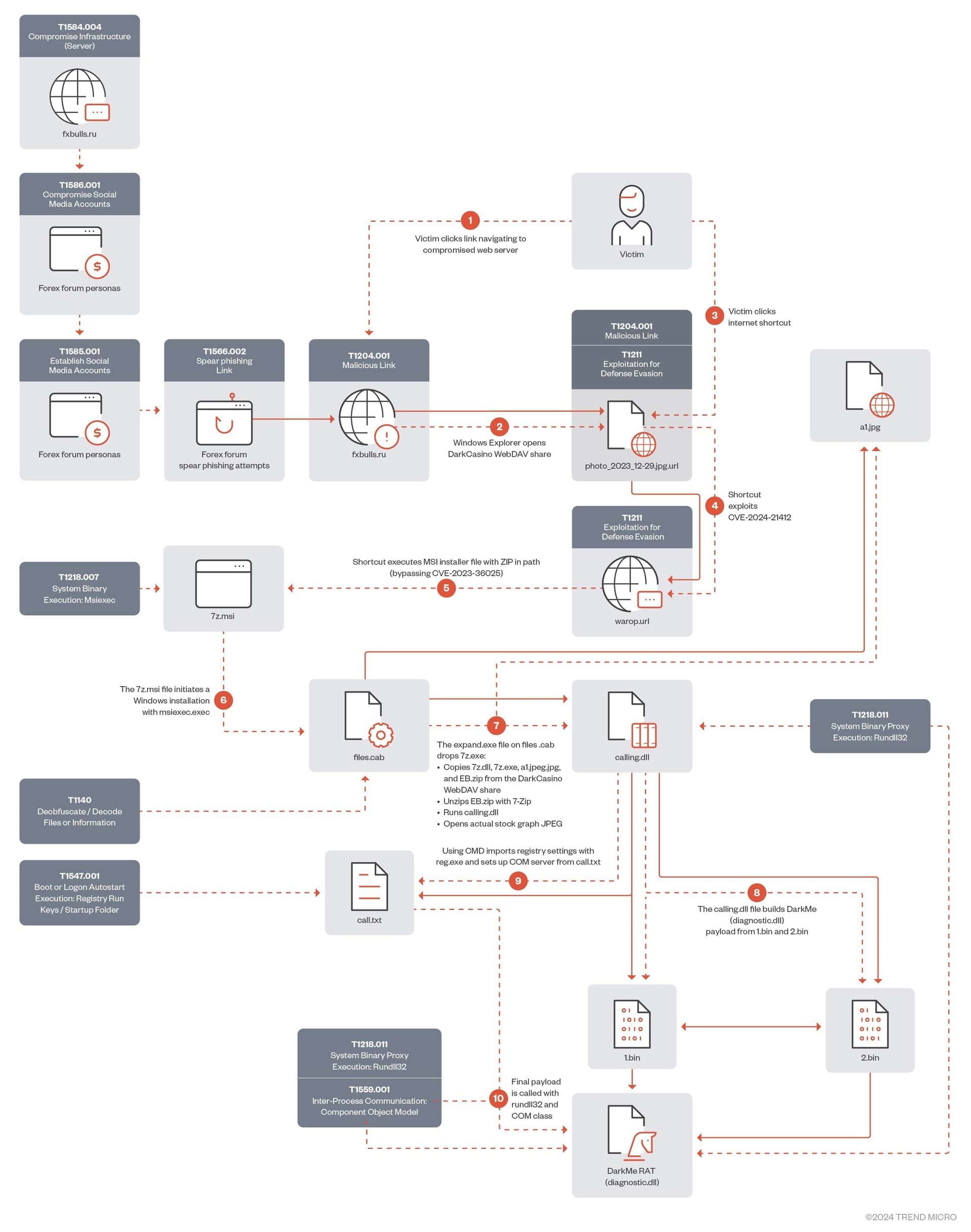
- This persistent access to the C&C Server effectively allows a threat actor full control of the compromised device, without any administrative interaction or end user warning. The full attack chain sequence can be seen below:
As always, end users are advised to practice caution when navigating public forums. If you would like to bolster your security posture through end user training, reach out to [email protected].
| Vendor Patch Advisories |
- Adobe has released security updates for Commerce, Substance 3D Painter, Acrobat and Reader, and more.
- Cisco released security updates for multiple products.
- Fortinet released security updates for a new FortiOS SSL VPN Remote Code Execution, which has been exploited in the wild.
- Google released Android February 2024 security updates
- Ivanti released security updates for a new Connect Secure authentication bypass flaw.
- SAP has released its February 2024 Patch Day updates.
Advanced deploys patches to all environments as a priority following a testing phase. The criticality of security updates is determined by several factors, primarily the ease of exploitability by threat actors and if the vulnerability has been exploited in the wild.
| Windows Server 2012 Officially End Of Support |
- On October 10th, Windows Server 2012 and Windows Server 2012 R2 officially reached end of support. This means the operating system will no longer receive critical security patches.
- Windows Server 2012 is considered one of the most popular server operating systems in the world. The retirement is expected to usher in a new wave of threat actors looking to take advantage of deprecated security features.
- Those looking to extend coverage to receive critical patches can subscribe to Extended Security Updates (ESUs). ESUs provide up to 3 years of additional coverage for patches deemed ‘Critical’ and ‘Important’ by Microsoft.
- Servers hosted in Azure are eligible for free ESUs until October 13th, 2026. Servers not hosted in Azure are eligible for ESUs until October 13th, 2026 through purchase of an ESU subscription.
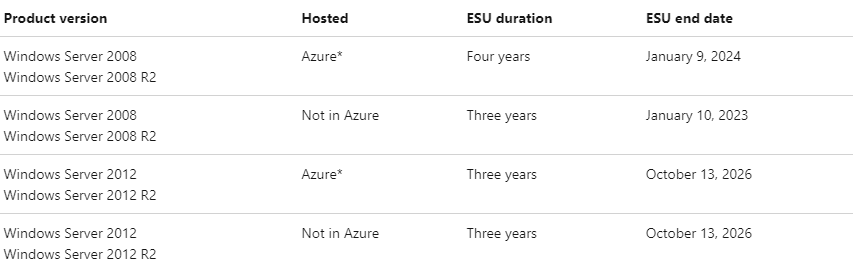
Advanced recommends clients take immediate action on any out-of-date operating systems. For more information on how these changes can affect your environment, reach out to [email protected].
| Industry Data: Crowdstrike’s 2024 Global Threat Report |
- CrowdStrike has released its 2024 Global Threat Report, highlighting a surge in adversaries leveraging stolen identity credentials to exploit cloud environment gaps.
- Attack velocity has dramatically increased year over year. Breakout Time is an industry term to measure the time between the compromise of one device and the compromise of an entire network. 2024’s report indicates this time is roughly 62 Minutes (down from 84 minutes in 2023)
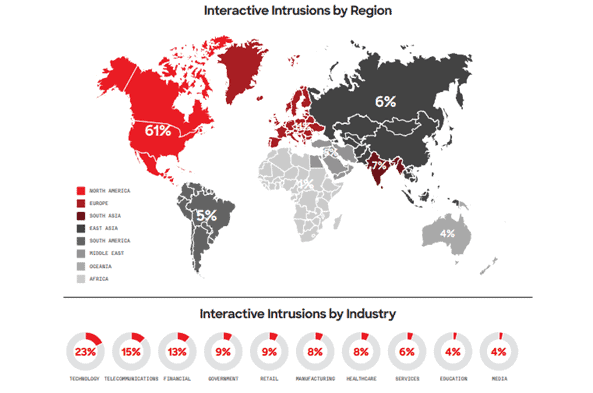
- Stealthy attacks spiked as adversaries compromise credentials, leading to a 60% increase in interactive intrusions (or ‘hands-on-keyboard’ activity) as opposed to brute-force bot logon attempts. The chart below shows a breakdown by region.
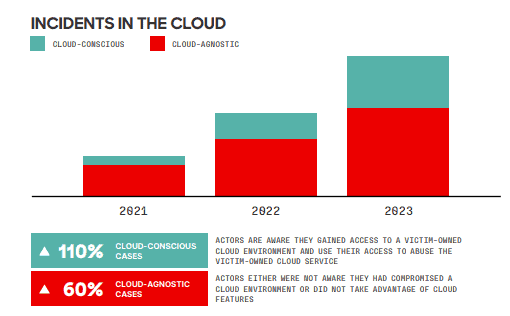
- Adversaries are targeting the cloud using valid credentials, posing challenges for defenders to distinguish normal from malicious behavior. The report shows cloud intrusions increased by 75% overall with cloud-conscious cases amplifying by 110% Year-over-Year.
- This emphasizes a modern trend in the industry: End users have become the primary targets for threat actors.
- The exploitation of generative AI by nation-state actors and hacktivists is on the horizon, expected to democratize attacks and lower entry barriers for sophisticated operations.
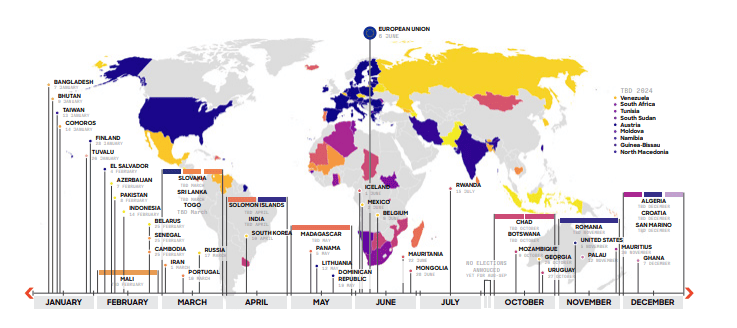
- With over 40 democratic elections scheduled in 2024, adversaries are likely to disrupt the electoral process or influence voter opinion through misinformation and disinformation campaigns. The chart below indicates countries holding presidential, parliamentary or general elections in 2024.
The full threat report can be seen here.
| Emerging Threat: Connectwise’s ScreenConnect Software |
- Connectwise has published a critical patch advisory for ScreenConnect, their lightweight remote access tool with millions of deployments worldwide.
- The vulnerability has been given a score of 10.0, the highest possible severity. System owners are advised to patch to the latest build, 23.9.8 immediately.
- The vulnerability takes advantage of a coding error in SetupModule.cs. The program contains an HTTP Request Filter with two responsibilities: If the application hasn’t been setup, redirect all requests to SetupWizard.aspx. If the application has been setup, deny any requests to SetupWizard.aspx or redirect to Administration.aspx. The code in question can be seen below:
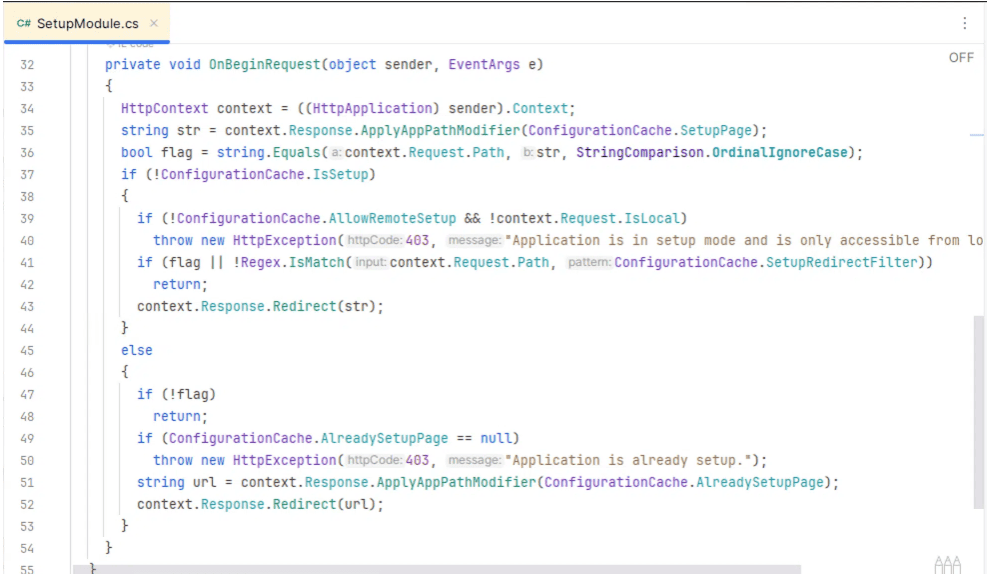
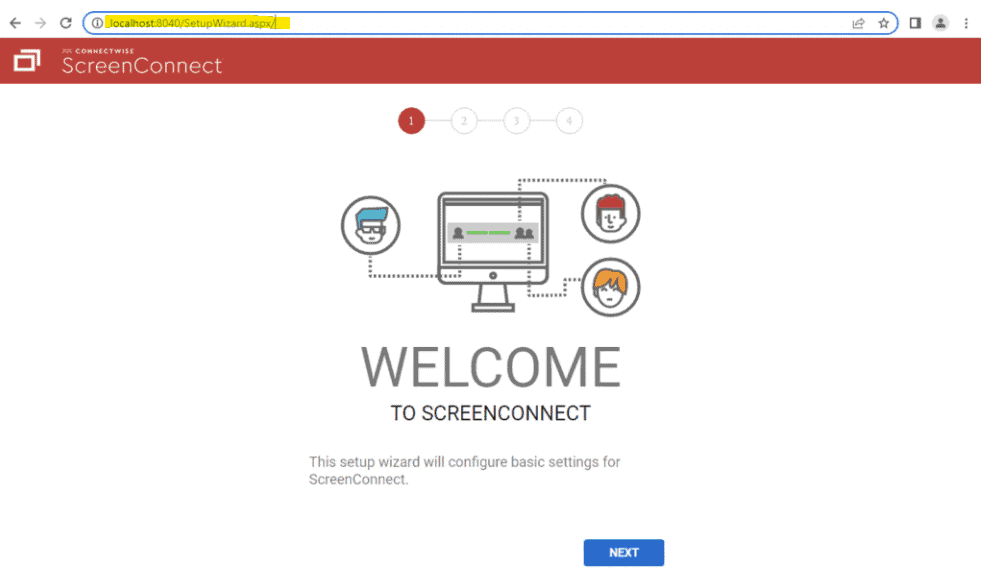
- The issue is how this code checks if the request URL is SetupPage.aspx. The use of ‘string.Equals’ checks for exact equality, so a URL like ‘<app_url>/SetupWizard.aspx’ will match. However, there are other URLs that resolve to SetupWizard.aspx that don’t match. If a threat actor were to add a forward slash to the end of the URL (<app_url>/SetupWizard.aspx/) they could access to the setup wizard, even after the application is already setup.
- This allows a threat actor connecting to a public ScreenConnect server to create an administrative account and assume full control of all connected devices within minutes.
- The attack method of adding a slash has led to the vulnerability colloquially being called “SlashAndGrab”.
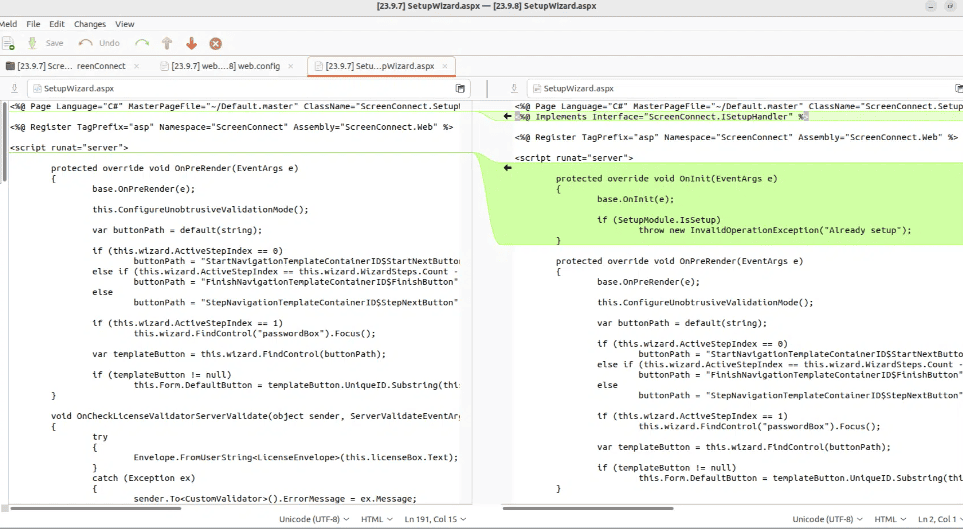
- The fix for this was a slight code modification in our initial snippet for SetupModule.cs. A check is now performed to make sure that the initial application setup has not been completed. The original code can be seen below on the left, while the patched code can be seen on the right:
Advanced customers had this patch addressed on all ScreenConnect instances. Please reach out to [email protected] with any questions, comments or concerns.
| Latest News: Mother Of All Breaches |
What happened?
- On January 24th, a private cloud storage instance containing roughly 12 Terabytes of leaked information was found open to the internet by the security research team at Cybernews.
- This leak contains an estimated 28 billion total records. Records are considered any individual, complete piece of data, such as a username, a password, or a birthday. While only some, not all, of these records were usernames and passwords, researchers have confirmed all the data is sensitive. This means the leaked information could be associated with an individual’s name, address, or other identifiable factors.
- Researchers believe that the dataset is primarily composed of information from other data breaches. This is often referred to as a Compilation Of Multiple Breaches, or COMB for short. The following companies, and the number of records believed to be exposed, can be seen below:
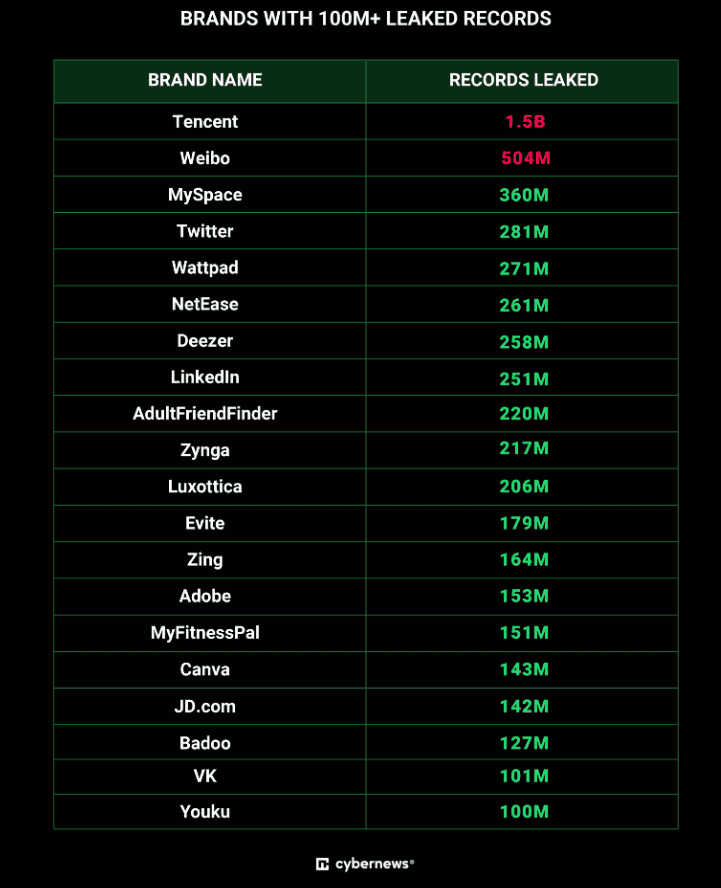
- The records were broken into datasets, each pertaining to a single data breach. Of the 4145 unique datasets, 1448 folders had more than 100,000 records, and 601 folders had more than 1,000,000.
How will I know if I have been exposed?
- Cybernews has published a web-based tool to check for data leaks at cybernews.com/personal-data-leak-check. Customers and end users alike are advised to check this list and take necessary actions for protecting their data.
What can I do if my information has been leaked?
- Change your passwords and use a password manager (Tips for Evaluating a Password Manager)
- Routinely rotating your passwords is necessary for cyber safety. Strong and unique passwords are best, which means never reusing your passwords across different sites and platforms. Using a password manager will help you keep on top of it all, while also storing your passwords securely. Moreover, changing your passwords regularly might make a stolen password worthless because it’s out of date.
- Enable two-factor authentication (learn more about two-factor authentication)
- While a strong and unique password is a good first line of defense, enabling two-factor authentication across your accounts will help your cause by providing an added layer of security. If your accounts support two-factor authentication, enable it.
- Consider Identity Monitoring Solutions
- Identity monitoring solutions can notify you in the event of your personal information being exposed. Harvested personal information is often gathered and sold in bulk on public forums. Customers with Advanced DarkWeb Monitoring are advised immediately if their personal information is found in a large breach.
- Change your passwords and use a password manager (Tips for Evaluating a Password Manager)
As always, Advanced is proud to be here for all your security needs. Reach out now to determine how you can improve your security posture and keep your business running!
Sources:
- Microsoft February 2024 Patch Tuesday fixes 2 zero-days, 73 flaws
- February 2024 Risk Analysis
- CVE-2024-21412: Water Hydra Targets Traders With Microsoft Defender SmartScreen Zero-Day
- Microsoft Defender SmartScreen
- ConnectWise ScreenConnect: Authentication Bypass Deep Dive
- CVE-2024-21410, CVE-2024-21413, and CVE-2024-21401 Lead the list of Critical & Actively Exploited Vulnerabilities in Microsoft’s February 2024 Patch Tuesday