| Patch Tuesday – 1/14/25 |
The 2nd Tuesday of every month is Patch Tuesday! Every Patch Tuesday, Microsoft addresses security vulnerabilities in their products via a large deployment of software updates. This month’s Patch Tuesday addressed 159 security vulnerabilities. The full list can be seen here.
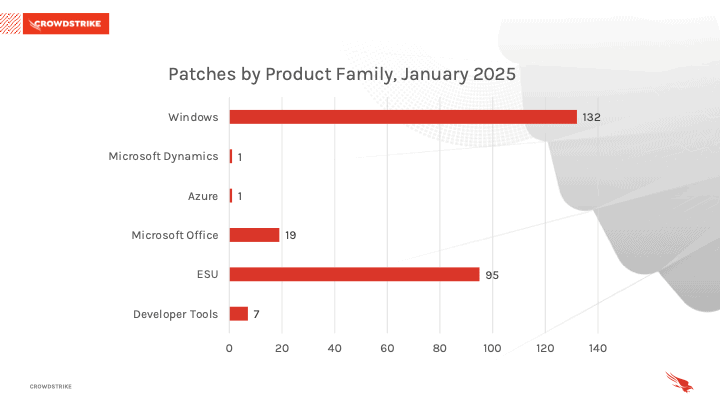
Windows products received the most patches this month with 132, followed by Extended Security Updates (ESU) with 95 and Microsoft Office with 19.
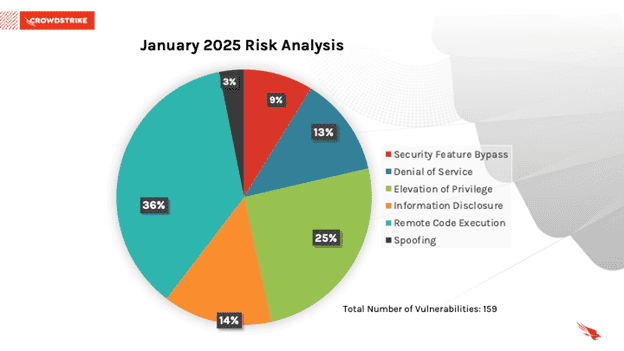
This month’s leading risk type is Remote Code Execution (36%) followed by Elevation Of Privilege (25%) and information disclosure (14%).
Threat Grading Overview
Microsoft assesses threats based on the theoretical worst possible outcome were a vulnerability to be exploited. The assessment factors in how easily a vulnerability can be exploited, and what damage could be done.
These patches included remediation for 8 “Zero-Day” vulnerabilities, meaning no patch was previously available. Three of these vulnerabilities have been reported as exploited in the wild.
CVE-2025-21333, CVE-2025-21334, CVE-2025-21335– Windows Hyper-V NT Kernel Integration VSP Elevation of Privilege Vulnerability
Microsoft has fixed three elevation of privilege vulnerability in Windows Hyper-V that were exploited in attacks to gain SYSTEM privileges on Windows devices.
No information has been released as to how these flaws were exploited in attacks, and they all show that they were disclosed anonymously.
As the CVEs for these three vulnerabilities are sequential and for the same feature, they were all likely found used or discovered through the same attacks.
The following zero-day vulnerabilities have not yet been reported exploited in the wild:
CVE-2025-21275 – Windows App Package Installer Elevation of Privilege Vulnerability
Microsoft fixed an elevation of privileges flaw in the Windows App Package Installer that could lead to SYSTEM privileges, the highest level of privilege on a given device.
“An attacker who successfully exploited this vulnerability could gain SYSTEM privileges,” explains Microsoft’s advisory.
Microsoft has indicated that the weakness is due to improper authorization but has not shared details of the vulnerability or source of disclosure.
CVE-2025-21308 – Windows Themes Spoofing Vulnerability
Microsoft fixed a Windows Theme vulnerability that could be exploited simply by displaying a specially crafted Theme file in Windows Explorer.
“An attacker would have to convince the user to load a malicious file onto a vulnerable system, typically by way of an enticement in an Email or Instant Messenger message, and then convince the user to manipulate the specially crafted file, but not necessarily click or open the malicious file.,” explains Microsoft’s advisory.
The flaw was discovered by Blaz Satler with 0patch by ACROS Security, which is a bypass of a previous flaw tracked as CVE-2024-38030. 0patch previously released micropatches for this flaw in October, while waiting for Microsoft to fix it.
When a Theme file is viewed in Windows Explorer and utilizes BrandImage and Wallpaper options that specify a network file path, Windows automatically sends authentication requests to the remote host, including the logged-in user’s NTLM credentials.
-These NTLM hashes can then be cracked to get the plain-text password or used in pass-the-hash attacks.
CVE-2025-21186, CVE-2025-21366, CVE-2025-21395 – Microsoft Access Remote Code Execution Vulnerability
Microsoft fixed three remote code execution vulnerabilities in Microsoft Access that are exploited when opening specially crafted Microsoft Access documents.
Microsoft has mitigated this issue by blocking access to the following Microsoft Access documents if they were sent via email:
- accdb
- accde
- accdw
- accdt
- accda
- accdr
- accdu
What makes this interesting is that Unpatched.ai, an AI-assisted vulnerability discovery platform, has discovered all three flaws.
| Vendor Patch Advisories |
Various companies have recommended critical patches for common software this month. Some of the most notable can be seen below:
- Adobe released security updates for Photoshop, Substance3D Stager and Designer, Adobe Illustrator for iPad, and Adobe Animate.
- Cisco released security updates for multiple products, including Cisco ThousandEyes Endpoint Agent and Cisco Crosswork Network Controller.
- Ivanti released security updates for a Connect Secure flaw zero-day exploited in attacks to deploy custom malware on devices.
- Fortinet released a security update for an authentication bypass zero-day vulnerability in FortiOS and FortiProxy that was exploited in attacks since November.
- GitHub released security updates for two Git vulnerabilities.
- Moxa released security updates for high-severity and a critical vulnerabilities in its industrial networking and communications networking devices.
- ProjectDiscovery released security updates in September for a Nuclei flaw that allows malicious templates to bypass signature verification.
- SAP releases security updates for multiple products, including fixes for two critical (9.9/10) vulnerabilities in SAP NetWeaver.
- SonicWall releases patches for an authentication bypass vulnerability in SSL VPN and SSH management that is “susceptible to actual exploitation.”
- Zyxel has released security updates to fix an improper privilege management vulnerability in the web management interface.
Advanced deploys patches to all environments as a priority following a testing phase. The criticality of security updates is determined by several factors, primarily the ease of exploitability by threat actors and if the vulnerability has been exploited in the wild. Please reach out to [email protected] with any questions, comments or concerns on your patch management.
| Apple Updates |
- The latest version of iOS and iPadOS is 18.2.1. Learn how to update the software on your iPhone, iPad, or iPod touch.
- The latest version of macOS is 15.2. Learn how to update the software on your Mac and how to allow important background updates.
- The latest version of tvOS is 18.2.1. Learn how to update the software on your Apple TV.
- The latest version of watchOS is 11.2. Learn how to update the software on your Apple Watch.
- The latest version of visionOS is 2.2. Learn how to update the software on your Apple Vision Pro.
| Case Study: NTLanManager (NTLM), and a Critical Vulnerability On The World’s Most Used Legacy Software |
NTLM (NT LAN Manager) is an authentication protocol developed by Microsoft in the early 1990s. It has been widely used in Windows environments for securing access to network resources and verifying users’ identities. NTLM operates as a ‘challenge-response’ protocol, ensuring that passwords are never sent over the network in plain text.
How NTLM Works
At a high level, NTLM authentication involves the following steps:
- User Authentication Request:
- When you try to access a resource, the client (e.g., your computer) sends your username to the server. The server knows what your username and password are, and will now ‘challenge’ you to prove your identity.
- Challenge Issued:
- The server responds with a random number (called a “challenge”).
- Password Hash Response:
- Your computer uses the challenge and your password to generate a ‘value’ (or a ‘hash’, via a cryptographic function) and sends this response to the server. This value is derived from performing a function of your password and the challenge value sent by the server. The server (which knows your password) will also perform the same function of your password and the challenge value.
- Verification:
- The server will compare the client’s response with its own calculation. If the values match, authentication succeeds.

This is a critical means of communication and authentication between devices, because the client’s password is never sent directly to or from the server. This eliminates the risk of an intruder listening ‘on the wire’ to intercept passwords.
Despite being an older protocol, NTLM remains in use today for several reasons:
- Backward Compatibility: Many legacy systems and applications still rely on NTLM for authentication.
- Fallback Mechanism: NTLM often acts as a fallback when Kerberos (a more secure protocol) isn’t available.
- Ease of Use: In small or isolated networks, NTLM may be simpler to configure.
While NTLM was effective in its time, modern attackers have developed many ways to exploit its weaknesses. The most common of which is called an NTLM Relay Attack.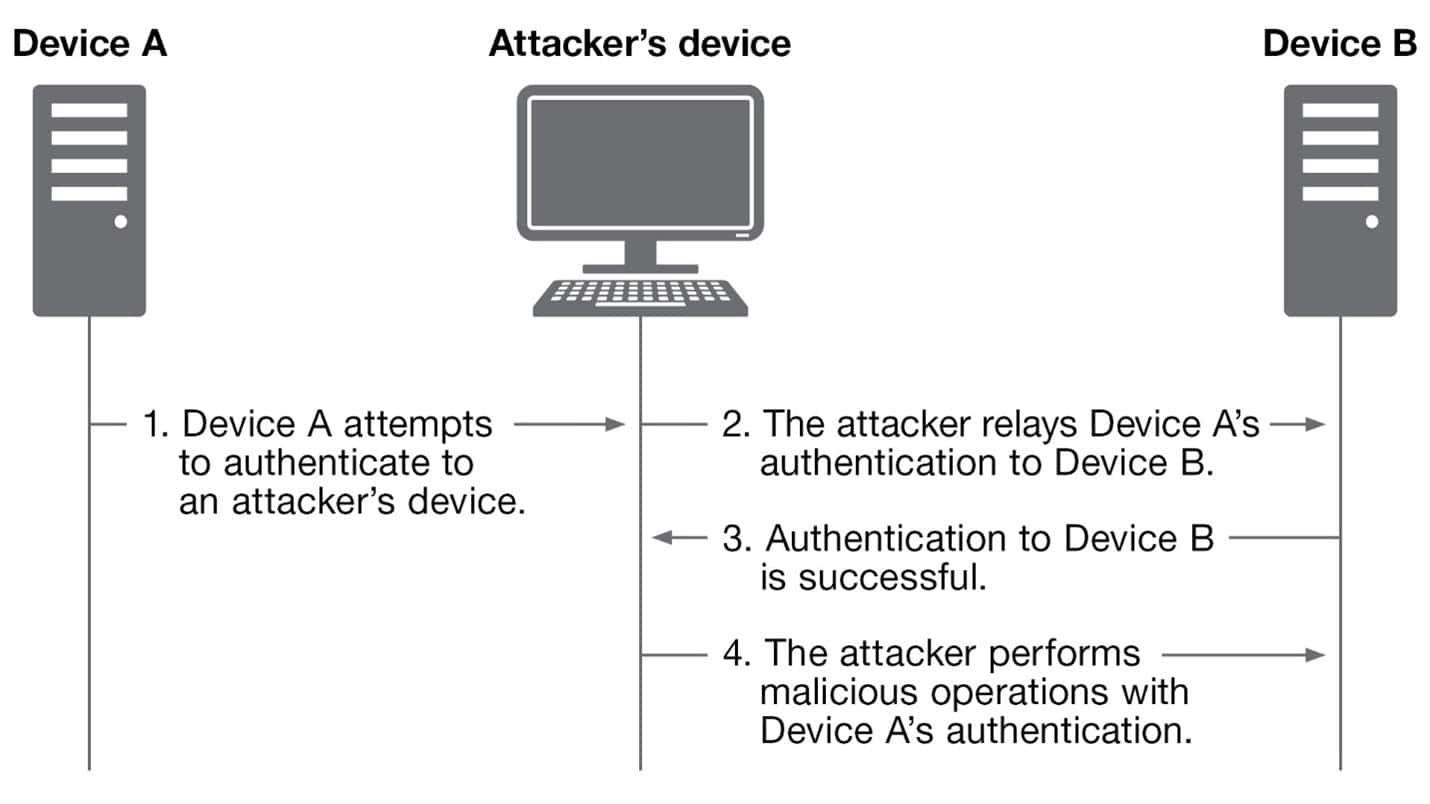
The purpose of relay attacks is to redirect authentication from one source to another. An attacker can trick a system (Device A) into authenticating to an attacker-owned machine. Thus, the attacker can relay that authentication to a target system (Device B) and harness (or ‘pass’) the valid credentials to use them on an unintended system.
Though NTLM has undergone upgrades since its LAN Manager origins through NTLMv1 and NTLMv2, these upgrades primarily focused on increased challenge length and tougher hashing algorithms. Inherent design flaws of the challenge-response mechanism are still exploitable with a sophisticated attacker.
In this month’s Patch Tuesday, Microsoft revealed details about a critical vulnerability affecting NTLMv1. CVE-2025-21311 has a CVSS Score of 9.8 out of a possible 10. Most notably, the Attack Vector for this vulnerability is ‘Network’ (meaning the attack can be executed over the internet) the Attack Complexity is ‘Low’ (meaning an attacker does not require significant prior knowledge of the system), and the Privileges required is ‘None’ (meaning the attacker does not need an account associated with the targeted environment).
In the interest of protecting end users, Microsoft has not disclosed details on the exploitation process for this vulnerability. Microsoft has also reported this exploitation has not yet been seen in the wild.
Addressing Inherent Flaws With Kerberos
Kerberos is an authentication protocol developed to address concerns with NTLM. Named after Cerberus, the three-headed dog that guards the entrance to the underworld, Kerberos boasts several new features to secure authentication between local devices.
How Does Kerberos Work?
Logging In (Authentication Request)
- When you log into your computer, your credentials (username and password) are sent to the Authentication Server (AS), which checks if you’re in the Kerberos database.
Receiving a Ticket-Granting Ticket (TGT)
- If your credentials are valid, the AS generates a Ticket-Granting Ticket (TGT) and a temporary encryption key (called a session key).
- The TGT proves your identity and is encrypted, so it’s secure even if intercepted.
Storing the TGT Locally
- Your computer stores the TGT, so you don’t need to keep entering your password when accessing resources.
Requesting Access to a Resource
- When you need to access a network resource (e.g., a shared file or application), your system sends the TGT and a request to the Ticket Granting Server (TGS).
Receiving a Service Ticket
- The TGS validates your TGT, checks your permissions for the requested resource, and issues a Service Ticket.
- The Service Ticket is encrypted and specific to the resource you’re trying to access.
Accessing the Resource
- Your computer sends the Service Ticket to the resource (e.g., a server).
- The server decrypts the ticket, verifies it, and grants access if everything is correct.

Kerberos includes several key advantages over NTLM, including:
Single Sign-On (SSO): Once you log in, you don’t need to re-enter your credentials for each resource.
Encryption: All communication, including tickets, is encrypted to prevent unauthorized access.
Mutual Authentication: Both the user and the server validate each other, reducing the risk of fake servers (man-in-the-middle attacks).
Time Sensitivity: Tickets are time-limited to prevent replay attacks (reusing old tickets to gain unauthorized access).
However, these benefits do not come without key drawbacks:
Management: Configuring and managing a Kerberos environment can be challenging. It requires a dedicated Key Distribution Center (KDC) and careful planning of user and service principals.
Time Synchronization: Kerberos relies on all systems being synchronized within a small time window (typically 5 minutes by default). This is critical to prevent replay attacks, but can break all authentication trust with slight time inconsistencies.
Single Point Of Failure: The Key Distribution Center (KDC) is critical to Kerberos’ operation. If the KDC becomes unavailable, authentication across the entire network can stop functioning.
The journey from NTLM to Kerberos highlights a broader trend in technology: the continuous evolution of protocols to meet growing security, scalability, and usability demands. While NTLM served its purpose in simpler network environments, its limitations became increasingly evident as threats evolved and networks expanded. Kerberos stepped in as a more secure, efficient, and scalable solution, addressing many of NTLM’s shortcomings.
The phasing out of older protocols is not just a story of obsolescence but of progress—an ongoing effort to stay one step ahead in an ever-evolving cybersecurity landscape.
| 2024 In Review – The Year Hackers Set Their Sights on Healthcare |
703 separate healthcare breaches were reported to the US Department of Health and Human Services (HHS OCR) in 2024, impacting approximately 180 million private health records. Breached information included names, contact details, Social Security numbers, insurance info, medical records, and financial details.
The majority of incidents were hacking/IT-related (including ransomware attacks), with unauthorized access/disclosure as the second most common cause.
440 breaches impacted healthcare providers, nearly 100 affected healthcare business associates, and nearly 60 involved health plans.
Top states with breaches were Texas (56), California (43), New York (34), Illinois (33), Florida (28).
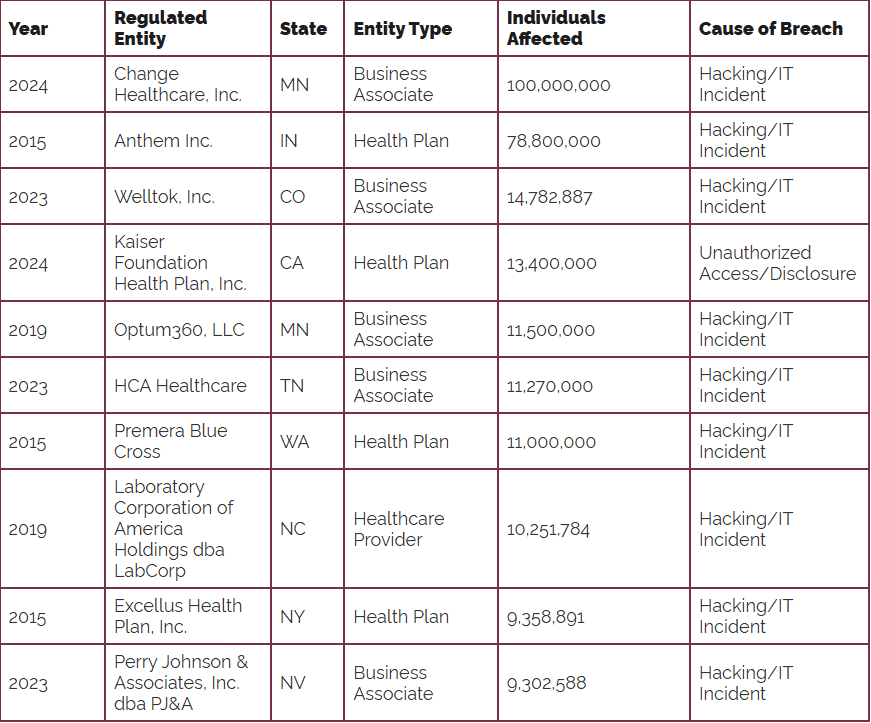
Biggest breach: Change Healthcare ransomware attack, compromising 100 million records.
Other major breaches included Kaiser Permanente (13.4 million), Ascension Health (5.5 million), and HealthEquity (4.3 million).
While 703 breaches shows a 5.9% decrease from the 747 breaches reported in 2023, 2024 saw the highest number of breached records ever, with 184,111,469 records compromised, a 9.4% increase from the previous year, impacting 53% of the U.S. population.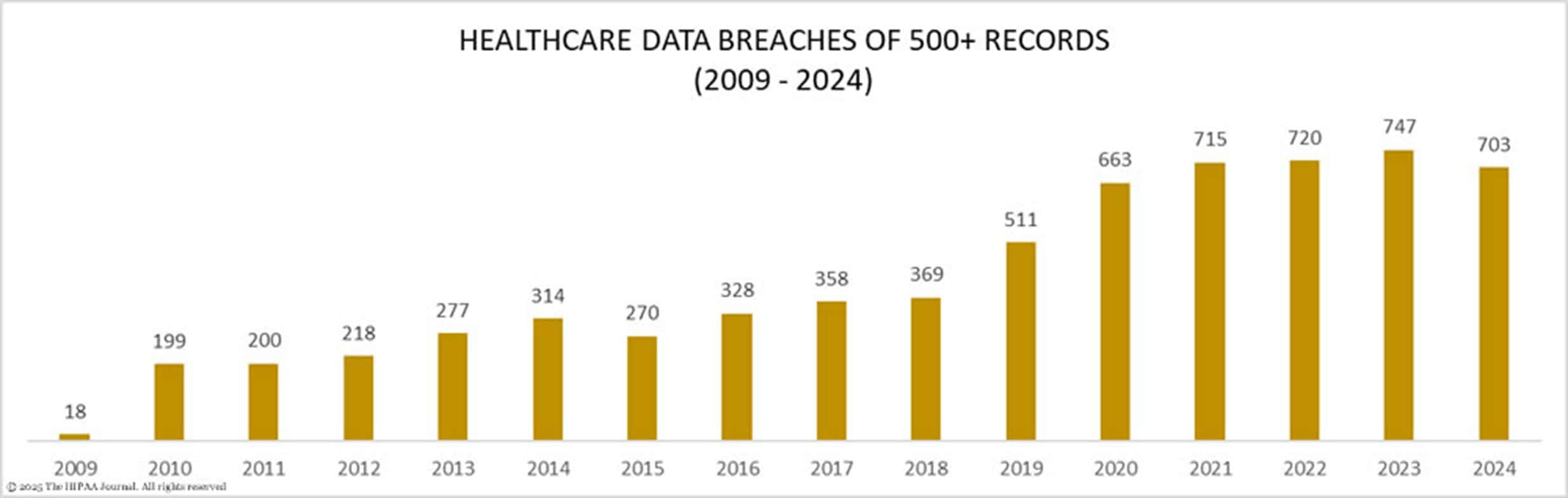
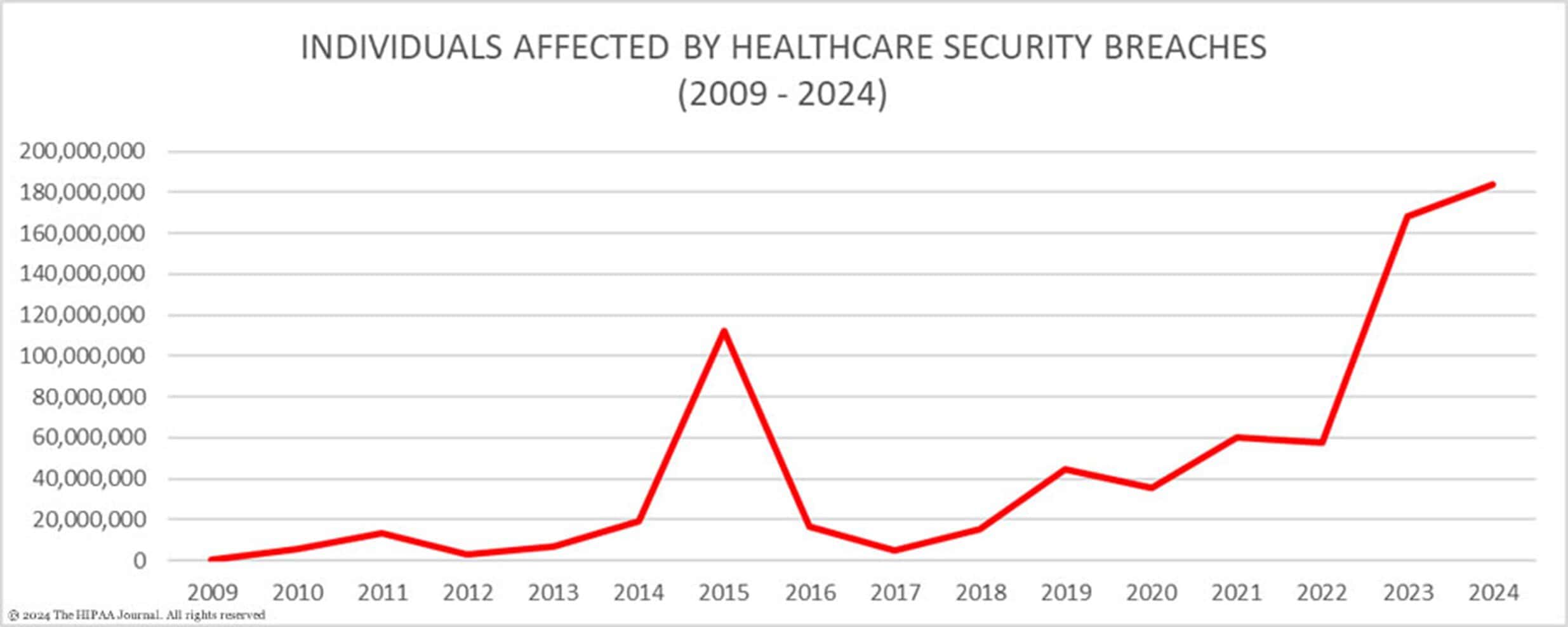
In fact, two of the 4 biggest Healthcare Data Breaches of all time happened in just 2024: Change Healthcare (#1) and Kaiser Permanente (#4)
In early 2024, the HHS Office for Civil Rights (OCR) published two sets of healthcare-specific cybersecurity performance goals (CPGs), offering best practices to enhance security against internal and external threats.
The CPGs are voluntary but are expected to significantly improve cybersecurity and reduce data breaches in healthcare organizations.
December 2024 saw the release of a proposed update to the HIPAA Security Rule, which would mandate the adoption of key cybersecurity measures.
The proposed HIPAA update includes multifactor authentication, data encryption (at rest and in transit), mitigating known vulnerabilities, network segmentation, asset inventory maintenance, and cybersecurity testing.
If enacted, the updated HIPAA Security Rule is expected to reduce healthcare data breaches and improve accountability for security failings in healthcare organizations.
The fate of the HIPAA Security Rule update now depends on the incoming Trump administration and their stance on cybersecurity.
As always, Advanced is proud to be here for all your security needs. Reach out now to determine how you can improve your security posture and keep your business running!
Regards,
The ACT Security Task Force
Sources:
https://msrc.microsoft.com/update-guide/releaseNote/2025-Jan
https://www.crowdstrike.com/blog/patch-tuesday-analysis-january-2025
https://www.bleepingcomputer.com/news/microsoft/microsoft-january-2025-patch-tuesday-fixes-8-zero-days-159-flaws/
https://vuldb.com/?id.291756
https://trustedsec.com/blog/practical-attacks-against-ntlmv1
https://www.crowe.com/cybersecurity-watch/ntlm-relay-attacks
https://answers.microsoft.com/en-us/msoffice/forum/all/ntlm-vs-kerberos/d8b139bf-6b5a-4a53-9a00-bb75d4e219eb
https://www.cvedetails.com/cve/CVE-2025-21311/
https://www.securityweek.com/2024-us-healthcare-data-breaches-585-incidents-180-million-compromised-user-records/
https://www.hipaajournal.com/biggest-healthcare-data-breaches-2024/