July 2024
- Patch Tuesday – 6/11
- Deep Dive: CVSS Breakdown On Critical Vulnerability
- Vendor Patch Advisories
- Apple Updates
- TeamViewer Compromise
- Snowflake Breach Snowballs
As always, Advanced is proud to be here for all your security needs. Reach out now ([email protected]) to determine how you can improve your security posture and keep your business running!
– The Advanced Security Task Force
| Patch Tuesday – 6/11 |
The 2nd Tuesday of every month is Patch Tuesday! Every Patch Tuesday, Microsoft addresses security vulnerabilities in their products via a large deployment of software updates. This month’s Patch Tuesday addressed 51 security vulnerabilities. The full list can be seen here.
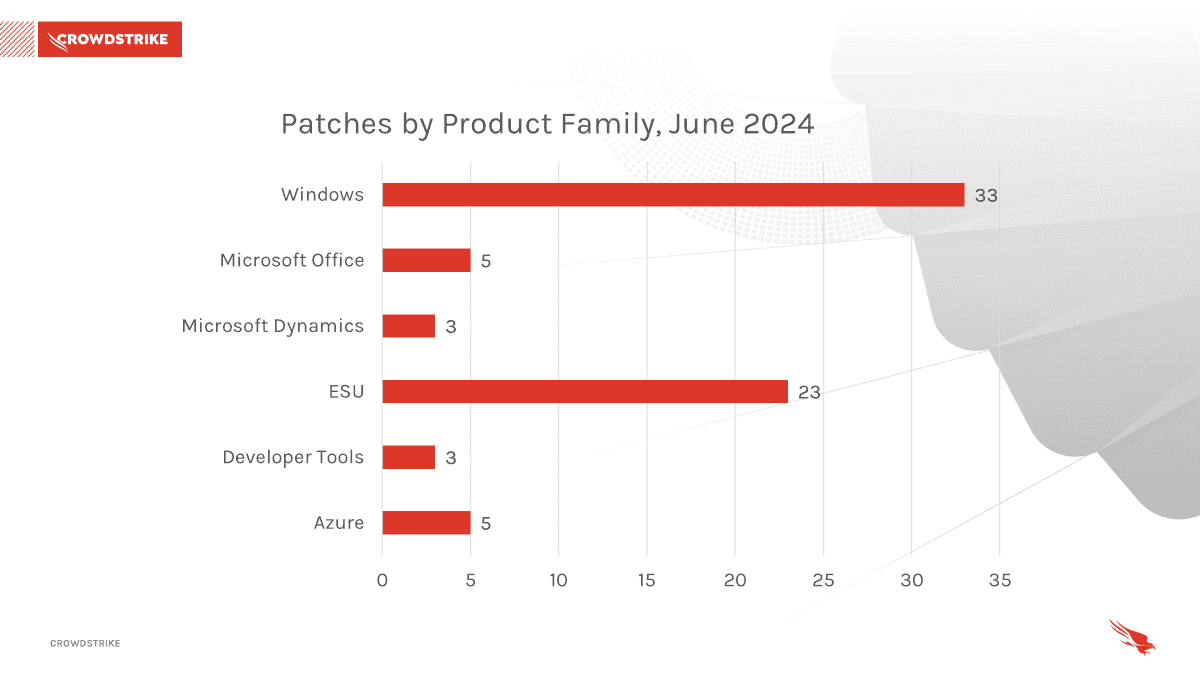
Windows products received the most patches this month with 33, followed by Extended Security Updates (ESU) with 23, and Azure/Microsoft Office with 5.

Of the 61 vulnerabilities addressed, 49% addressed Elevation of Privilege, 35% represented Remote Code Execution, and 10% represented denial of service.
| Deep Dive: CVSS Breakdown On Critical Vulnerability |
Microsoft assesses threats based on the theoretical worst possible outcome were a vulnerability to be exploited. The assessment factors in how easily a vulnerability can be exploited, and what damage could be done.

Of these 51 vulnerabilities, 1 is considered Critical. Details on this vulnerability can be seen below:
- CVE-2024-30080: Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability
Microsoft Message Queuing, or MSMQ, is a messaging protocol that allows applications running on separate servers/processes to communicate in a failsafe manner. A queue is a temporary storage location from which messages can be sent and received reliably, as and when conditions permit. This enables communication across networks and between computers, running Windows, which may not always be connected. Delivery will occur when the process on the other end ‘wakes up’ and receives notification of the message’s arrival. As this is a communication service, Windows PCs and servers are often in a state of waiting for MSMQ messages (or, ‘Listening’), leaving them particularly vulnerable to attackers.
CVE-2024-30080 involves targeting a vulnerable device with a series of specially crafted MSMQ packets in a rapid sequence over HTTP to a MSMQ server. This could result in remote code execution on the server side.
It is of note that this vulnerability is regarded as a 9.8/10. Let’s look at the Common Vulnerabilities Scoring System to determine how this number is generated. Below, you’ll see the official designation of this vulnerability from the National Institute of Standards and Technology (or NIST).

Using the above scoring system, we can start to translate the string of values and calculate our total risk score. Note the string below:
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
While this may appear to be nonsense, each letter denotes a specific value and provides information on the vulnerability. The acronyms are as follows:
- CVSS 3.1 designates the scoring system in use
- AV (Attack Vector): Describes how an attacker can exploit the vulnerability (e.g., local, adjacent network, or network)
- AC (Attack Complexity): Reflects how difficult it is to exploit the vulnerability (e.g., low, medium, or high)
- PR (Privileges Required): Indicates the level of privileges an attacker needs to exploit the vulnerability (e.g., none, low, or high)
- UI (User Interaction): Specifies whether user interaction is required to exploit the vulnerability (e.g., none, required)
- S (Scope): Determines whether exploitation of the vulnerability impacts components beyond the vulnerable component
The final three letters make up what is known as the ‘Security Triad’ or ‘CIA’ (Confidentiality, Integrity, Availability).
- C (Confidentiality): A measure of how this vulnerability potentially impacts the privacy of end user data (Asks ‘Can a threat actor access data for which they are not authorized?’)
- I (Integrity): A measure of how this vulnerability potentially impacts the reliability of data in the victim’s environment (Asks ‘Can a threat actor change or tamper any data?)
- A (Availability): A measure of how this vulnerability potentially impacts the ability to access data and services (Asks ‘Can a threat actor destroy data or take down services?)
These are known as the Base Metrics. The base metrics are then scored based on the vulnerability, as seen below:
Attack Vector (AV): This metric reflects how the vulnerability is exploited
- N (Network): The vulnerability is exploitable from remote locations
- A (Adjacent Network): The vulnerability is exploitable from an adjacent network
- L (Local): The vulnerability is exploitable locally
- P (Physical): The vulnerability requires physical access to exploit
Attack Complexity (AC): This metric describes the conditions that must be met by the attacker to exploit the vulnerability
- L (Low): The attack is straightforward without special conditions
- H (High): The attack requires specific conditions that are beyond the attacker’s control
Privileges Required (PR): This metric describes the level of privileges an attacker must possess before successfully exploiting the vulnerability.
- N (None): No privileges are required
- L (Low): The attacker needs basic user privileges
- H (High): The attacker needs high privileges, such as administrative or root access
User Interaction (UI): This metric captures whether the vulnerability requires user interaction to be exploited.
- N (None): No user interaction is required
- R (Required): Exploitation requires user interaction
Scope (S): This metric describes whether a vulnerability in one vulnerable component impacts resources in components beyond its security scope.
- U (Unchanged): The impact is limited to the vulnerable component
- C (Changed): The impact can extend beyond the vulnerable component
Confidentiality (C): This metric measures the impact on the confidentiality of the information resources managed by a software component due to a successfully exploited vulnerability.
- H (High): A total loss of confidentiality
- L (Low): Some loss of confidentiality
- N (None): No impact on confidentiality
Integrity (I): This metric measures the impact on the integrity of a successfully exploited vulnerability.
- H (High): A total loss of integrity
- L (Low): Some loss of integrity
- N (None): No impact on integrity
Availability (A): This metric measures the impact on the availability of the impacted component resulting from a successfully exploited vulnerability.
- H (High): A total loss of availability
- L (Low): Some loss of availability
- N (None): No impact on availability
By analyzing our original CVSS string, we can get a clear picture of exactly what makes this vulnerability so dangerous:
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
AV (Attack Vector): N (Network)
- AV: Indicates how the vulnerability is exploited
- N (Network): The vulnerability can be exploited remotely over a network (from any location)
AC (Attack Complexity): L (Low)
- AC: Describes the conditions beyond the attacker’s control that must exist to exploit the vulnerability
- L (Low): The attack does not require any special conditions, meaning it is straightforward to execute
PR (Privileges Required): N (None)
- PR: Describes the level of privileges an attacker must possess before successfully exploiting the vulnerability
- N (None): The attacker does not require any privileges to exploit the vulnerability
UI (User Interaction): N (None)
- UI: Captures whether the vulnerability requires user interaction to be exploited
- N (None): The vulnerability can be exploited without any user interaction
S (Scope): U (Unchanged)
- S: Indicates whether a successful exploit of the vulnerability can affect resources beyond the security scope of the vulnerable component
- U (Unchanged): A successful attack only impacts resources that are within the same security scope
C (Confidentiality): H (High)
- C: Measures the impact on the confidentiality of the information resources managed by a software component due to a successfully exploited vulnerability
- H (High): There is a total loss of confidentiality, resulting in all resources within the impacted component being compromised
I (Integrity): H (High)
- I: Measures the impact on the integrity of a successfully exploited vulnerability
- H (High): There is a total loss of integrity, or a complete compromise of the system integrity
A (Availability): H (High)
- A: Measures the impact on the availability of the impacted component resulting from a successfully exploited vulnerability
- H (High): There is a total loss of availability, rendering the component completely unavailable
| Vendor Patch Advisories |
Various companies have recommended critical patches for common software this month. Some of the most notable can be seen below:
- ARM fixes an actively exploited bug in Mali GPU kernel drivers
- Cisco released security updates for its Cisco Finesse and Webex
- Cox fixed an API auth bypass bug that impacted million of modems
- F5 releases security updates for two high-severity BIG-IP Next Central Manager API flaws
- PHP fixed a critical RCE flaw that is now actively exploited in ransomware attacks
- TikTok fixes an exploited zero-day, zero-click flaw in their direct messages feature
- VMware fixes three zero-day bugs exploited at Pwn2Own 2024
- Zyxel releases an emergency RCE patch for end-of-life NAS devices
Advanced deploys patches to all environments as a priority following a testing phase. The criticality of security updates is determined by several factors, primarily the ease of exploitability by threat actors and if the vulnerability has been exploited in the wild. Please reach out to [email protected] with any questions, comments or concerns on your patch management.
| Apple Updates |
- The latest version of macOS is 14.5. Learn how to update the software on your Mac and how to allow important background updates
- The latest version of tvOS is 17.5.1. Learn how to update the software on your Apple TV
- The latest version of watchOS is 10.5. Learn how to update the software on your Apple Watch
- The latest version of visionOS is 1.2. Learn how to update the software on your Apple Vision Pro
- The latest version of iOS and iPadOS is 17.5.1. Learn how to update the software on your iPhone, iPad, or iPod touch
| TeamViewer Reports Breach by Advanced Persistent Threat Actors |
- TeamViewer reported a breach in its corporate environment detected on June 26, 2024
- A cybersecurity firm claims the breach was conducted by an APT (Advanced Persistent Threat) hacking group
- The company activated its response team, initiated investigations with cybersecurity experts, and implemented remediation measures
- TeamViewer clarified that its internal corporate IT environment is separate from its product environment
- There is no evidence suggesting the product environment or customer data was affected
- Investigations are ongoing, and TeamViewer’s primary focus is maintaining the integrity of their systems
- TeamViewer plans to be transparent about the breach and will update the investigation status as more information becomes available
- Despite claims of transparency, the “TeamViewer IT security update” page has a “noindex” tag, making it hard to find via search engines
- TeamViewer’s software is widely used, with over 640,000 customers and installations on over 2.5 billion devices
- The 2016 breach linked to Chinese threat actors was not disclosed at the time as no data was stolen
- News of the recent breach was reported by IT security professional Jeffrey on Mastodon, referencing alerts from the Dutch Digital Trust Center and NCC Group
- NCC Group alerted customers about the compromise of TeamViewer by an APT group due to its widespread usage
- Health-ISAC also warned of active targeting of TeamViewer services by the Russian hacking group APT29
- APT29, linked to Russia’s Foreign Intelligence Service, is known for cyberespionage and recent attacks on Western diplomats and Microsoft
- It is unclear if the alerts from NCC Group and Health-ISAC are linked, as they address different aspects of the breach
| Snowflake Breach Sends Ripples Through Various Markets |
- A hack against customers of the cloud storage company Snowflake looks like it may turn into one of the biggest-ever data breaches
- A joint investigation by SnowFlake, Mandiant, and CrowdStrike revealed that a threat actor, tracked as UNC5537, used stolen customer credentials to target at least 165 organizations that had not configured multi-factor authentication protection on their accounts
- Companies such as Ticketmaster, Santander, Advance Auto Parts, and Neiman Marcus have filed 8-K forms with the Securities and Exchange Commission, reporting the exposure of customer data
- According to cybersecurity firm Hudson Rock, the threat actor claimed they also gained access to data from other high-profile companies using Snowflake’s cloud storage services, including Anheuser-Busch, State Farm, Mitsubishi, Progressive, and Allstate
- Hudson Rock added that a Snowflake employee was infected by a Lumma-type Infostealer in October. The malware stole their corporate credentials to Snowflake infrastructure, as seen in a screenshot shared by the threat actor and embedded below

- A timeline of the intrusion generated by Mandiant shows persistent threat actor access as far back as April 14th

- The threat actor, identified by username Sp1d3r, also put leaked data for sale on hacker forums following Neiman Marcus’ refusal to pay the requested bounty
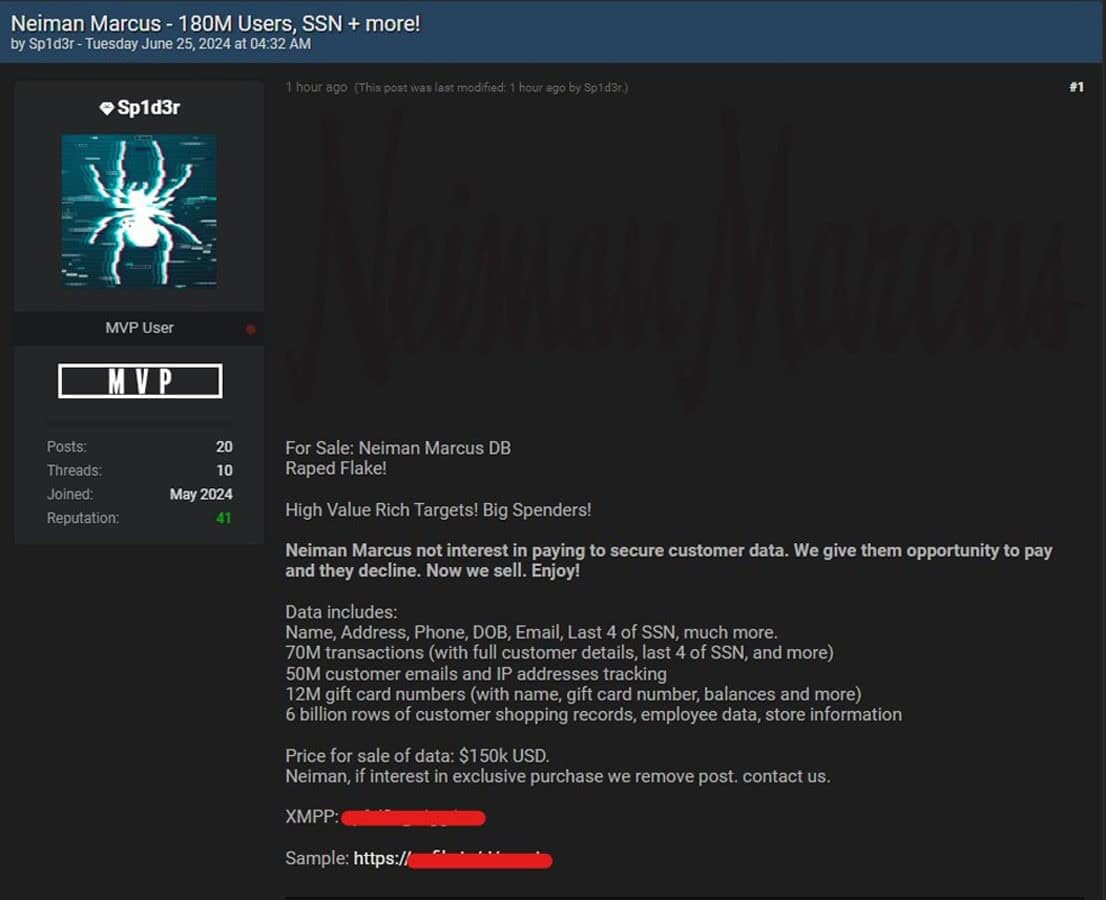
- Snowflake reports that the compromise is not due to faults or misconfigurations within their infrastructure, but with end user account security. ACT encourages all clients with cloud based accounts to enforce Multi-Factor Authentication to protect themselves from a breach.
Sources:
- June 2024 Security Updates
- June 2024 Patch Tuesday: 51 Vulnerabilities Addressed Including One Critical and One Zero-Day
- Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability
- CVE-2024-30080 Detail
- Apple Security Releases
- TeamViewer’s corporate network was breached in alleged APT hack
- Snowflake account hacks linked to Santander, Ticketmaster breaches
- Snowflake Attack Update: Victim List Continues to Grow