
| Patch Tuesday – 3/11/2025 |
The 2nd Tuesday of every month is Patch Tuesday! Every Patch Tuesday, Microsoft addresses security vulnerabilities in their products via a large deployment of software updates. This month’s Patch Tuesday addressed 64 security vulnerabilities. The full list can be seen here. 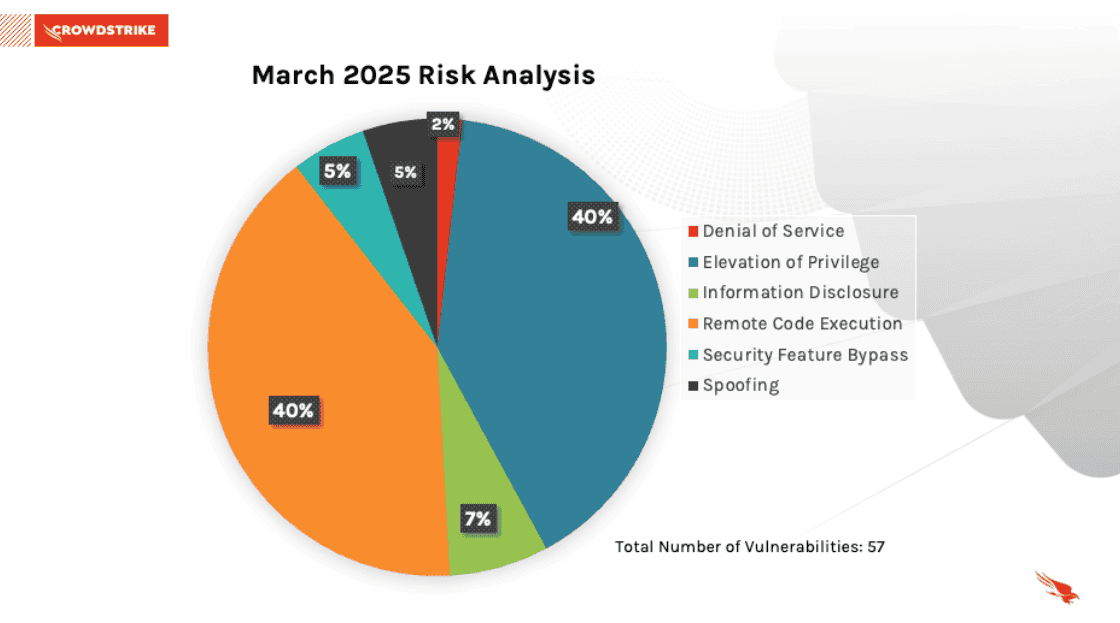
This month’s leading risk types are Remote Code Execution and Elevation Of Privilege (40%) followed by Information Disclosure (7%) and Spoofing (5%).
Threat Grading Overview
Microsoft assesses threats based on the theoretical worst possible outcome were a vulnerability to be exploited. The assessment factors in how easily a vulnerability can be exploited, and what damage could be done.
These patches included remediation for seven “Zero-Day” vulnerabilities, meaning no patch was previously available. All of these vulnerabilities are being actively exploited in the wild.
CVE-2025-24983 – Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability
Microsoft says this vulnerability will allow local attackers to gain SYSTEM privileges on the device after winning a race condition.
Microsoft has not shared how the flaw was exploited in attacks.
CVE-2025-24984 – Windows NTFS Information Disclosure Vulnerability
Microsoft says that this flaw can be exploited by attackers who have physical access to the device and insert a malicious USB drive.
Exploiting the flaw allows the attackers to read portions of heap memory and steal information.
Microsoft says that this vulnerability was disclosed anonymously.
CVE-2025-24985 – Windows Fast FAT File System Driver Remote Code Execution Vulnerability
Microsoft says that this remote code execution vulnerability is caused by an integer overflow or wraparound in Windows Fast FAT Driver that, when exploited, allows an attacker to execute code.
“An attacker can trick a local user on a vulnerable system into mounting a specially crafted VHD that would then trigger the vulnerability,” explains Microsoft.
While Microsoft has not shared details about how it was exploited but malicious VHD images were previously distributed in phishing attacks and through pirated software sites.
Microsoft says that this vulnerability was disclosed anonymously.
CVE-2025-24991 – Windows NTFS Information Disclosure Vulnerability
Microsoft says that attackers can exploit this flaw to read small portions heap memory and steal information.
Attackers can exploit the flaw by tricking a user into mounting a malicious VHD file.
Microsoft says that this vulnerability was disclosed anonymously.
CVE-2025-24993 – Windows NTFS Remote Code Execution Vulnerability
Microsoft says that this remote code execution vulnerability is caused by a heap-based buffer overflow bug in Windows NTFS that allows an attacker to execute code.
“An attacker can trick a local user on a vulnerable system into mounting a specially crafted VHD that would then trigger the vulnerability,” explains Microsoft
Microsoft says that this vulnerability was disclosed anonymously.
CVE-2025-26633 – Microsoft Management Console Security Feature Bypass Vulnerability
While Microsoft has not shared any details about this flaw, based on its description, it may involve a bug that allows malicious Microsoft Management Console (.msc) files to bypass Windows security features and execute code.
“In an email or instant message attack scenario, the attacker could send the targeted user a specially crafted file that is designed to exploit the vulnerability,” explains Microsoft.
“In any case an attacker would have no way to force a user to view attacker-controlled content. Instead, an attacker would have to convince a user to take action. For example, an attacker could entice a user to either click a link that directs the user to the attacker’s site or send a malicious attachment.”
One zero day is publicly exposed, meaning steps are available to reproduce the vulnerability. Details on this vulnerability can be seen below:
CVE-2025-26630 – Microsoft Access Remote Code Execution Vulnerability
Microsoft says this remote code execution flaw is caused by a use after free memory bug in Microsoft Office Access.
To exploit the flaw, a user must be tricked into opening a specially crafted Access file. This can be done through phishing or social engineering attacks.
However, the flaw cannot be exploited through the preview pane. Microsoft reports the flaw was discovered by Unpatched.ai.
| Vendor Patch Review |
Various companies have recommended critical patches for common software this month. Some of the most notable can be seen below:
- Broadcom fixed three zero-day flaws in VMware ESXi that were exploited in attacks.
- Cisco fixes WebEx flaw that could expose credentials, as well as critical vulnerabilities in Cisco Small Business routers.
- An unpatched Edimax IC-7100 IP camera flaw is being exploited by botnet malware to infect devices.
- Google fixed an exploited zero-day flaw in an Android’s Linux kernel driver that was used to unlock devices.
- Ivanti released security updates for Secure Access Client (SAC) and Neurons for MDM.
- Fortinet released security updates for numerous products, including FortiManager, FortiOS, FortiAnalyzer, and FortiSandbox.
- Paragon disclosed a flaw in its BioNTdrv.sys driver that was exploited by ransomware gangs in BYOVD attacks.
- SAP releases security updates for multiple products.
| Apple Updates |
Keeping your software up to date is one of the most important things you can do to maintain your Apple product’s security. The latest build numbers for various products can be seen below.
- The latest version of iOS and iPadOS is 18.4.1. Learn how to update the software on your iPhone or iPad.
- The latest version of macOS is 15.4.1. Learn how to update the software on your Mac and how to allow important background updates.
- The latest version of tvOS is 18.4.1. Learn how to update the software on your Apple TV.
- The latest version of watchOS is 11.4. Learn how to update the software on your Apple Watch.
- The latest version of visionOS is 2.4.1. Learn how to update the software on your Apple Vision Pro.
Note that after a software update is installed for iOS, iPadOS, tvOS, watchOS, and visionOS, it cannot be downgraded to the previous version.
| Case Study: Browser Sandboxing |
What is Browser Sandboxing?
Browser sandboxing is a simple but important safety feature in web browsers like Google Chrome and Mozilla Firefox, designed to keep your computer safe while you browse the internet.
Imagine a sandbox as a special play area at a park, with a fence around it to keep kids from wandering off. When you visit a website, your browser puts that website in this fenced-off area so it can’t reach the rest of your computer. This means the website can’t touch your personal files, passwords, or other programs if it’s trying to cause trouble. It’s a great way to stay safe online, but if a website finds a way to jump over the fence—like what happened with the Chrome and Firefox below—it might be able to cause harm, such as stealing your information or taking over your computer. That’s why you should always update your browser—it helps fix those gaps in the fence and keeps you protected.
Zero-Day Vulnerabilities in Chrome and Firefox Exploited in Espionage Campaign.
On March 25, Google issued an urgent security update for Chrome to address a zero-day vulnerability, identified as CVE-2025-2783, which was actively exploited in the wild. Discovered by Kaspersky’s Global Research and Analysis Team (GReAT), this vulnerability enabled attackers to bypass Chrome’s sandbox—a vital security layer designed to isolate web content—and execute arbitrary code on the victim’s system. Named “Operation ForumTroll,” the campaign targeted Russian media outlets, educational institutions, and government organizations through phishing emails disguised as invitations to the “Primakov Readings” forum. Victims were compromised upon clicking a malicious link, which initiated an attack chain that also leveraged an undisclosed secondary vulnerability to achieve remote code execution (RCE). Kaspersky’s analysis suggests that the operation was likely conducted by a state-sponsored threat actor, given its complexity and focus on espionage objectives.
Subsequently, on March 27, 2025, Mozilla released Firefox version 136.0.4, along with ESR versions 115.21.1 and 128.8.1, to address a related vulnerability, CVE-2025-2857. Identified during the investigation of the Chrome exploit, this flaw similarly allowed for a sandbox escape on Windows systems. Although no evidence of active exploitation was reported for the Firefox vulnerability, its similarity to the Chrome flaw prompted immediate action. The issue originated from an incorrect handle within Firefox’s inter-process communication (IPC) framework, enabling a compromised child process to gain unauthorized privileges. Mozilla strongly recommended that Windows users update their browsers promptly to mitigate potential risks.

Recommended Mitigation Strategies
To protect against these vulnerabilities, security researchers advise the following measures:
- Prompt Browser Updates: Ensure that Google Chrome is updated to the latest version released after March 25, 2025, and Mozilla Firefox is updated to version 136.0.4 or ESR versions 115.21.1 and 128.8.1. These updates address the vulnerabilities and prevent exploitation.
- Phishing Awareness Training: Educate users to identify phishing attempts, particularly those involving urgent or official-looking invitations. Verify the legitimacy of links by contacting the sender through official channels before interacting with them.
- Network Monitoring: Deploy endpoint detection and response (EDR) solutions to monitor for anomalous browser activity, which may indicate exploitation attempts, such as unexpected process creation or network connections.
As always, Advanced is proud to be here for all your security needs. Reach out now to determine how you can improve your security posture and keep your business running!
Regards,
The ACT Security Task Force
Sources:
https://msrc.microsoft.com/update-guide/releaseNote/2025-Mar
https://www.bleepingcomputer.com/news/microsoft/microsoft-march-2025-patch-tuesday-fixes-7-zero-days-57-flaws/
https://support.apple.com/en-us/100100
https://www.bleepingcomputer.com/news/security/google-fixes-chrome-zero-day-exploited-in-espionage-campaign/
https://www.bleepingcomputer.com/news/security/mozilla-warns-windows-users-of-critical-firefox-sandbox-escape-flaw/





