
April 2024
- Patch Tuesday – 4/9
- Threat Grading Overview
- Deep Dive: CVE-2024-26234 and Digital Signatures – Who Can We Trust?
- Vendor Patch Advisories
- Emerging Threat: Telegram Zero-Click Compromise
- Follow Up: Second Roku Account Breach Impacts Additional 576k Users
- LastPass Employee Targeted Through Deepfake CEO Call
As always, Advanced is proud to be here for all your security needs. Reach out now ([email protected]) to determine how you can improve your security posture and keep your business running!
– The Advanced Security Task Force
| Patch Tuesday – 4/9 |
The 2nd Tuesday of every month is Patch Tuesday! Every Patch Tuesday, Microsoft addresses security vulnerabilities in their products via a large deployment of software updates. This month’s Patch Tuesday addressed 60 security vulnerabilities. The full list can be seen here.
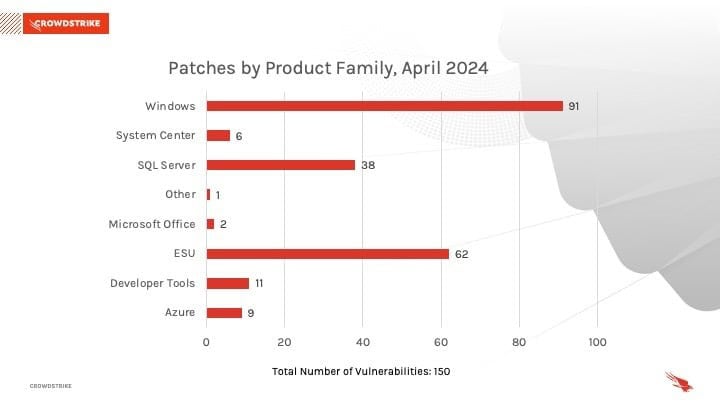
Windows products received the most patches this month with 91, followed by Extended Security Updates (ESU) with 62 and Azure with 9.
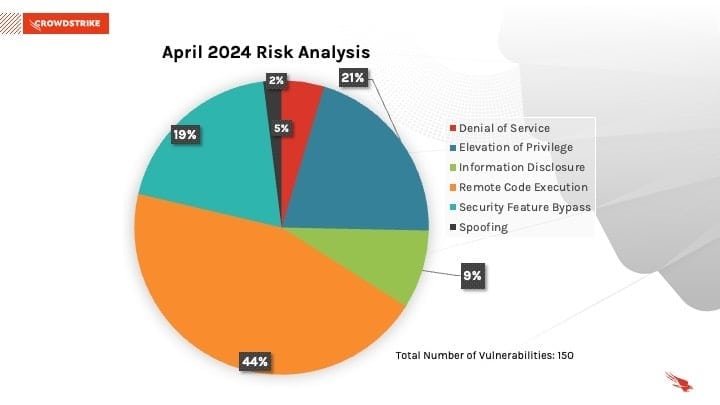
Of the 150 vulnerabilities addressed, 44% addressed Remote Code Execution Vulnerabilities, 21% addressed Elevation Of Privileges, followed by 19% for Security Feature Bypass.
| Threat Grading Overview |
Microsoft assesses threats based on the theoretical worst possible outcome were a vulnerability to be exploited. The assessment factors in how easily a vulnerability can be exploited, and what damage could be done.

Microsoft also references the Common Vulnerability Scoring System (CVSS), which assesses the severity of a vulnerability on a scale of 0 (Non-Issue) to 10 (Severe Issue) based on 5 key factors:
- Attack Vector: Describes how an attacker can exploit the vulnerability (e.g., local, adjacent network, or network).
- Attack Complexity: Reflects how difficult it is to exploit the vulnerability (e.g., low, medium, or high).
- Privileges Required: Indicates the level of privileges an attacker needs to exploit the vulnerability (e.g., none, low, or high).
- User Interaction: Specifies whether user interaction is required to exploit the vulnerability (e.g., none, required).
- Scope: Determines whether exploitation of the vulnerability impacts components beyond the vulnerable component.
Of these 150 vulnerabilities, 3 are considered Critical. Details on these can be seen below:
- CVE-2024-21323: Microsoft Defender for IoT Remote Code Execution Vulnerability
- CVE-2024-29053: Microsoft Defender for IoT Remote Code Execution Vulnerability
- CVE-2024-21322: Microsoft Defender for IoT Remote Code Execution Vulnerability
This month’s patches also address two Zero Day Vulnerabilities. These are vulnerabilities being exploited in the wild that did not yet have a patch available.
- CVE-2024-26234: Proxy Driver Spoofing Vulnerability
- CVE-2024-29988: SmartScreen Prompt Security Feature Bypass Vulnerability
| Deep Dive: CVE-2024-26234 and Digital Signatures – Who Can We Trust |
- CVE-2024-26234 details what was once interpreted as a false positive detection (a detection of a vulnerability when in fact one does not exist). Upon further review, it has been confirmed that this driver, once trusted by Microsoft, contains a malicious backdoor.
- Microsoft deems driver files as legitimate or illegitimate using Digital Signatures.
- Imagine you’re receiving a package in the mail. You want to make sure it’s from the person or company you trust, and you also want to be sure that nobody has tampered with it along the way. A digital signature on a driver file is like a special seal on that package.
- Authenticity: Just like a seal with the sender’s logo assures you that the package is indeed from them, a digital signature confirms that the driver file comes from a trusted source, like Microsoft. It’s like getting a package from a well-known company rather than from a random stranger.
- Integrity: Now, let’s say someone tries to open the package and mess with its contents. The seal would break, indicating that the package has been tampered with. Similarly, if someone tries to change the driver file after it’s been signed, the digital signature becomes invalid, warning you that something fishy might be going on.
- Trustworthiness: When you see that seal from a trusted sender, you feel more confident about what’s inside. Similarly, when you install a driver file with a valid digital signature from a reputable source, like Microsoft, you can trust that it’s safe to use and won’t harm your computer.
- CVE-2024-26234 is a rare example of dangerous software that was trusted by Microsoft. Let’s dive deeper with Sophos X-Ops to see how this happened:
- Below is the digital signature information for the compromised driver. The file’s metadata indicates that it is a “Catalog Authentication Client Service” by “Catalog Thales ” – possibly an attempt to impersonate the legitimate company Thales Group.
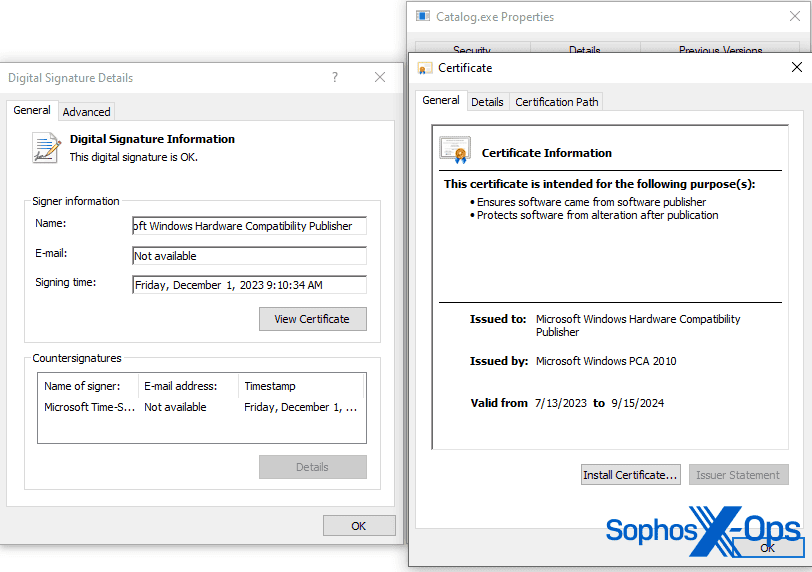
- Authenticode is a Microsoft code-signing security measure, which identifies the publisher of an application and provides verification that the application hasn’t been modified since it was signed and published. Fortunately, Microsoft provides code snippets on how to process these signatures and extract further metadata from them. One of the pieces of information extracted was the original requesting publisher.
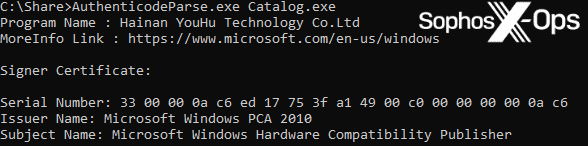
- In this case, the original requesting publisher is Hainan YouHu Technology Co. Ltd. After a review of this driver on VirusTotal, it was discovered that the file was previously bundled with a setup file for a product named LaiXi Android Screen Mirroring, “a marketing software…[that] can connect hundreds of mobile phones and control them in batches, and automate tasks like batch following, liking, and commenting.”
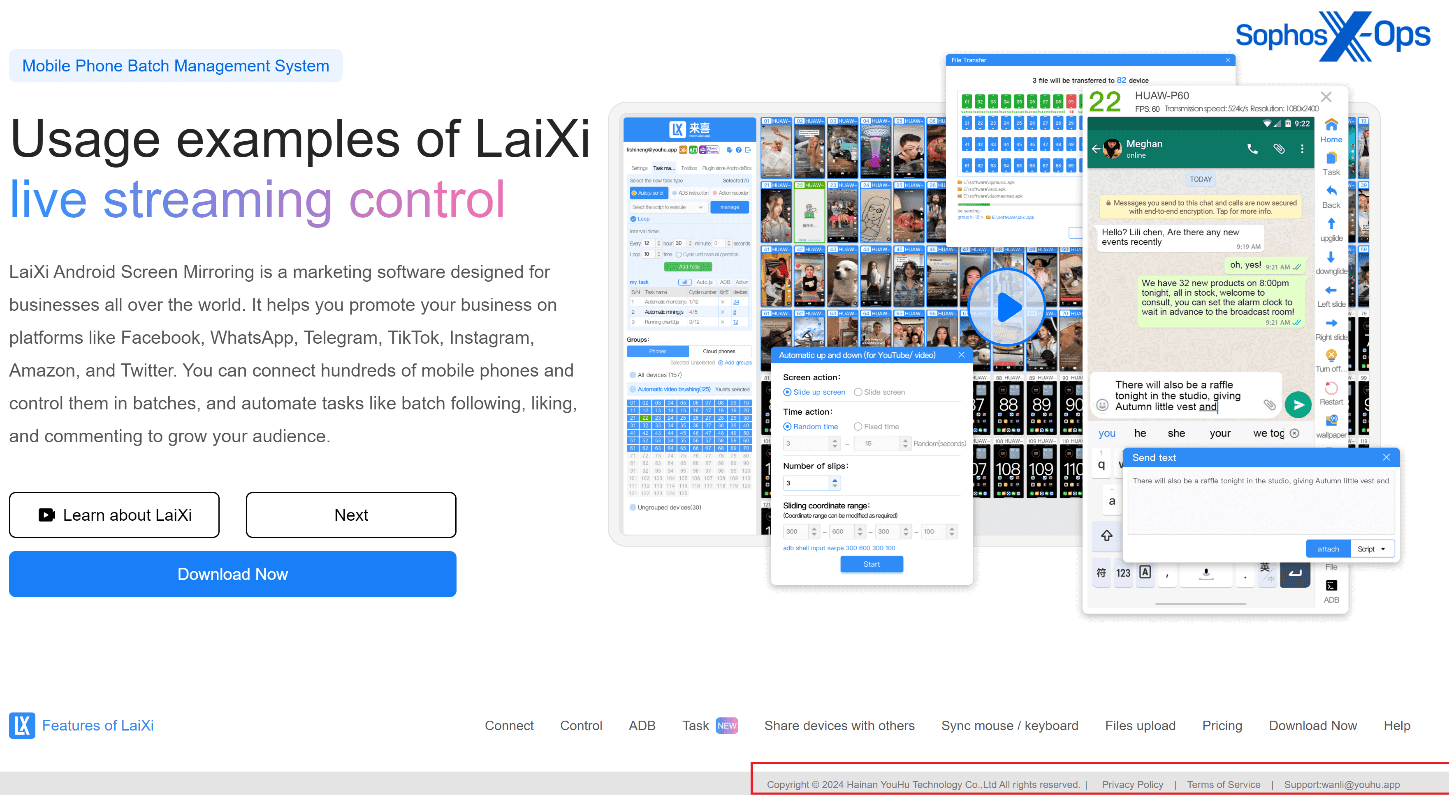
- The suspicious file embeds a tiny freeware proxy server, called 3proxy – a questionable feature for an authentication client. Sophos analysts believe this embedded binary is intended to monitor and intercept network traffic on an infected system.
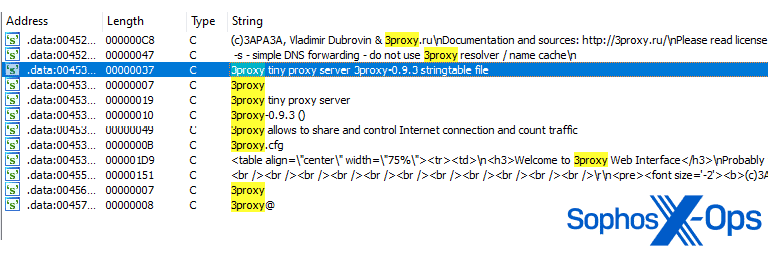
- When the file executes, it installs itself as a service called ‘CatalogWatcher’, with a service description of ‘Google ADB LoaclSocket [sic] Multi-threading Graphics API’ – a complete mismatch for the file version information shown in Figure 1. While researchers can’t confirm it, it is believed that this is connected to link to a setup file for the LaiXi Android software, and an attempt to trick infected users into believing that the service is legitimate. The code snippet can be seen below.
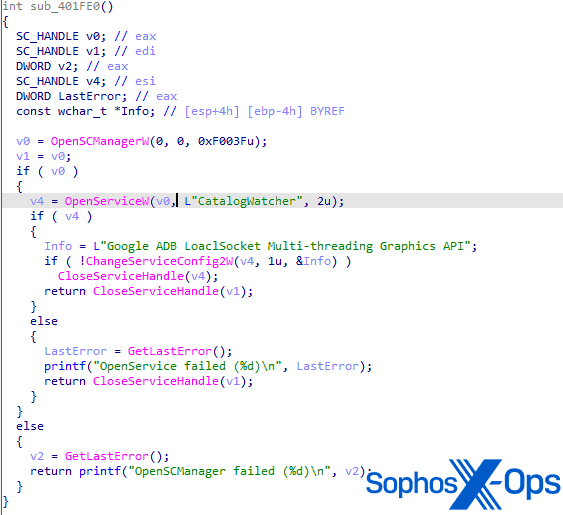
- Once the service runs, the malware queues a new work item/thread via QueueUserWorkItem to the threadpool. Once the process has enough resources available, the malicious thread starts. This thread embeds the core functionality of the backdoor itself. Interestingly, this function starts with an attempt to call the function VmProtectBeginVirtualization(), which is an export of the VMProtectSDK32.DLL by VMProtect.
- The Command & Control server string “catalog[.]micrisoftdrivers[.]com” – a lookalike domain of microsoftdrivers[.]com – is decrypted via XOR operation. A Python reimplementation of the decryption routine is below:
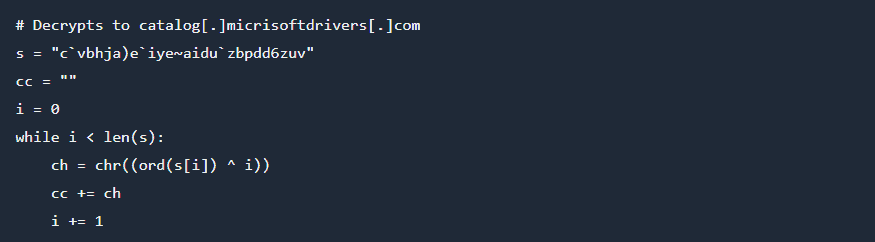
- So, we now have a driver available for download that runs a malicious backdoor to allow remote code execution at a large scale. This file is also trusted by Microsoft, meaning the end user will not be notified of any potential dangers when downloading the file. Following the publication of this backdoor by Sophos, Microsoft immediately revoked their trust of this driver and updated their patch list. It is still being investigated how this file was trusted despite flagging from threat analysts.
Patches are released to devices covered by Advanced following a testing process. If you have any questions, comments or concerns, please reach out to [email protected].
| Vendor Patch Advisories |
Various companies have recommended critical patches for common software this month. Some of the most notable can be seen below:
- Cisco released security updates for multiple products.
- D-Link disclosed new vulnerabilities in end-of-life NAS devices that have now been confirmed to be actively exploited. These vulnerabilities will not be fixed.
- Google fixed two Google Pixel zero-day’s and a zero-day in Google Chrome.
- New CONTINUATION Flood flaws can cause denial of service (DoS) attacks over HTTP/2.
- Ivanti released security updates to fix three VPN Gateway vulnerabilities.
- Linux distro maintainers revert to earlier versions of XZ Utils after backdoor found in supply chain attack.
- New LG WebOS flaws were disclosed that may impact over 90,000 exposed Smart TVs.
- SAP has released its April 2024 Patch Day updates.
Advanced deploys patches to all environments as a priority following a testing phase. The criticality of security updates is determined by several factors, primarily the ease of exploitability by threat actors and if the vulnerability has been exploited in the wild.
| Emerging Threat: Telegram Zero-Click Compromise |
- Telegram fixed a zero-day vulnerability in its Windows desktop application that could be used to bypass security warnings and automatically launch Python scripts.
- Over the past few days, rumors had been circulating on X and hacking forums about an alleged remote code execution vulnerability in Telegram for Windows.
- Telegram disputed these claims, posting publicly that the videos and rumors were unfounded.
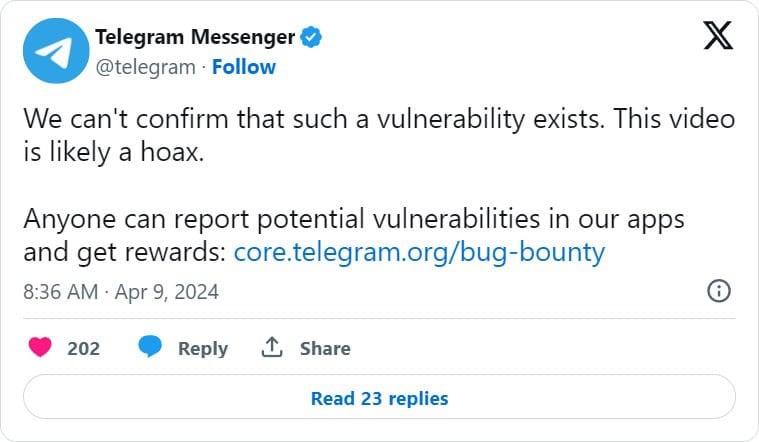
- However, the next day, a proof of concept exploit was shared on the XSS hacking forum explaining that a typo in the source code for Telegram for Windows could be exploited to send Python .pyzw files that bypass security warnings when clicked.
- The Telegram Desktop client keeps track of a list of file extensions associated with risky files, such as executable files. When someone sends one of these file types in Telegram, and a user clicks on the file, instead of automatically launching in the associated program in Windows, Telegram first displays the following security warning:
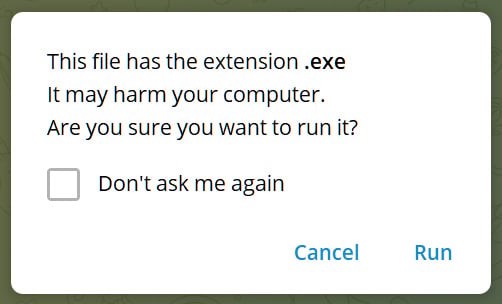
- However, unknown file types shared in Telegram will automatically be launched in Windows, letting the operating system decide what program to use. When Python for Windows is installed, it will associate the .pyzw file extension with the Python executable, causing Python to execute the scripts automatically when the file is double-clicked.
- The .pyzw extension is for Python zipapps, which are self-contained Python programs contained within ZIP archives. The Telegram developers were aware that these types of executables should be considered risky and added it to the list of executable file extensions. Unfortunately, when they added the extension, they made a typo, entering the extension as ‘pywz’ rather than the correct spelling of ‘pyzw’.
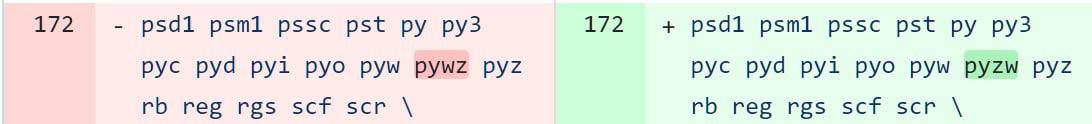
- Therefore, when those files were sent over Telegram and clicked on, they were automatically launched by Python if it was installed in Windows. This effectively allows attackers to bypass security warnings and remotely execute code on a target’s Windows device if they can trick them into opening the file. To masquerade the file, researchers devised using a Telegram bot to send the file with a mime type of ‘video/mp4,’ causing Telegram to display the file as a shared video. If a user clicks on the video to watch it, the script will automatically be launched through Python for Windows.
- Using an older version of Telegram, researchers at BleepingComputer received ‘video.pywz’ file from the threat analysts disguised as a mp4 video. This file simply contains Python code to open a command prompt, as shown below:
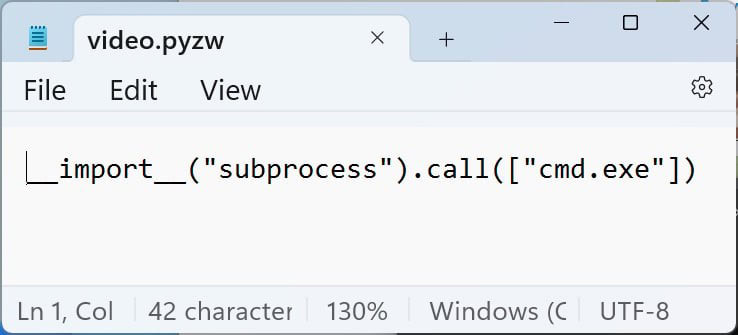
- After receiving word from threat researchers that this was still exploitable, Telegram utilized a server-side fix that appends the .untrusted extension to pyzw files, which, when clicked, will cause Windows to ask what program you wish to use to open them rather than automatically launching in Python.
| Follow Up: Second Roku Account Breach Impacts Additional 576k Users |
- Roku has warned that 576,000 accounts were hacked in new credential stuffing attacks after disclosing another incident that compromised 15,000 accounts in early March.
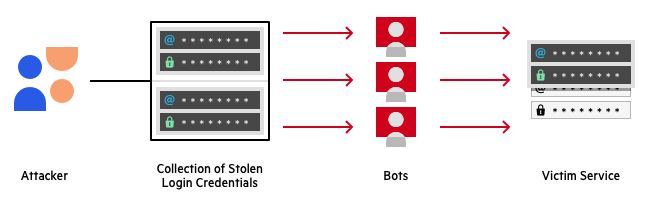
- The company said the attackers used login information stolen from other online platforms to breach as many active Roku accounts as possible in credential stuffing attacks.
- In such attacks, the threat actors leverage automated tools to attempt millions of logins using a list of user/password pairs, with this technique being particularly effective against accounts whose owners have reused the same login information across multiple platforms.
- An important distinction is that Roku has found no evidence of internal compromise, as credential stuffing attacks rely on the victim’s re-use of already compromised passwords, often from large leaks.
- Successfully hacked accounts are then sold on stolen account marketplaces for as little as 50 cents, as seen below where 439 accounts are being sold:
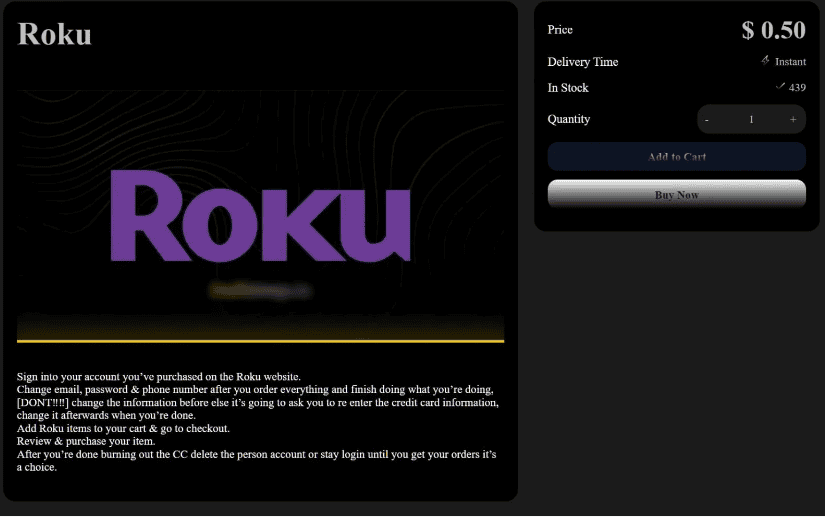
- Those who purchase the stolen accounts hijack them with their own information and use stored credit cards to purchase cameras, remotes, soundbars, light strips, and streaming boxes. After making their purchases, it is common for them to share screenshots of redacted order confirmation emails on Telegram channels associated with the stolen account marketplaces.
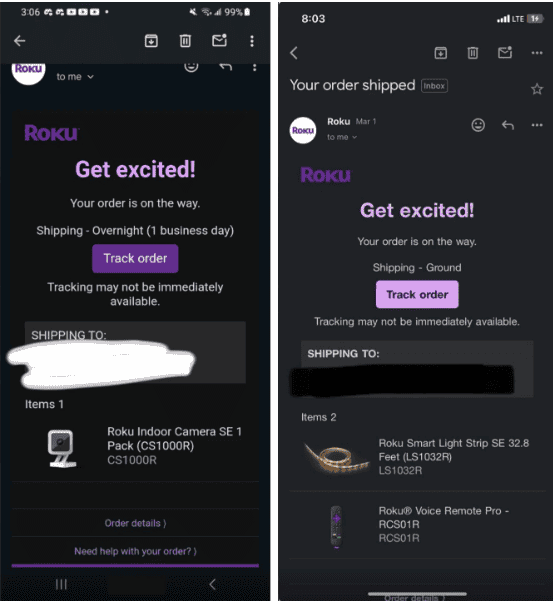
- After discovering this second wave of credential stuffing attacks, Roku has reset the passwords for all impacted accounts and is notifying affected customers directly about the incident.
- The company will also refund and reverse charges for accounts where the attackers used the linked payment information to pay for Roku hardware products and streaming service subscriptions.
- Since the last incident, Roku has also added support for two-factor authentication (2FA) and has now enabled it by default for all customer accounts, even for those that these recent attacks have not impacted.
| How do I protect myself from becoming a victim of Credential Stuffing? |
A successful credential stuffing attack hinges upon a victim using the same credentials for multiple accounts. Since threat actors know end users are likely to re-use passwords, a breach of any service has potentially devastating consequences across all of a users accounts if precautions are not taken. Details on this process can be seen below:
- Use Multi-Factor Authentication: Multi-Factor Authentication (MFA) uses various sign on methods to verify identity. This requires a combination of something you know (like a password) with something you have (like your phone) or something you are (a biometric factor, like your face or a fingerprint). Learn more about Multi-Factor Authentication here.)
- Use a Password Manager: Password managers keep all your passwords stored in one place and protects access to that place through MFA. This prevents end users from re-using passwords and ensures passwords are not easily guessable. Check out these Tips for Evaluating a Password Manager.
- Use Security Questions: Where applicable, you can configure security questions whenever a logon is detected from an unfamiliar device. Make sure your security questions do not contain easily accessible information (such as the high school you attended or your birthday), but instead focus on personal information (like your favorite food or the place of your first date).
| LastPass Employee Targeted Through Deepfake CEO Call |
- LastPass revealed this week that threat actors targeted one of its employees in a voice phishing attack, using deepfake audio to impersonate Karim Toubba, the company’s Chief Executive Officer.
- However, while 25% of people have been on the receiving end of an AI voice impersonation scam or know someone who has, according to a recent global study, the LastPass employee didn’t fall for it because the attacker used WhatsApp, which is a very uncommon business channel.
- “In our case, an employee received a series of calls, texts, and at least one voicemail featuring an audio deepfake from a threat actor impersonating our CEO via WhatsApp,” LastPass intelligence analyst Mike Kosak said. The call record can be seen below:
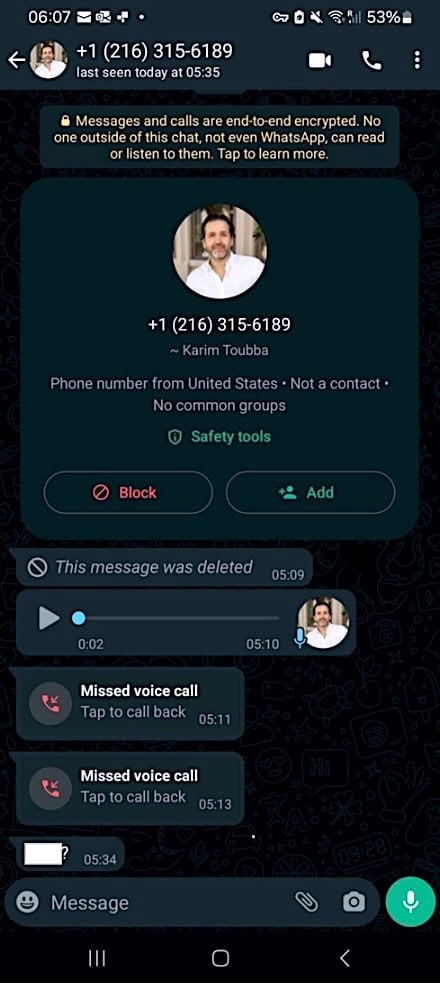
- LastPass’ warning follows a U.S. Department of Health and Human Services (HHS) alert issued last week regarding cybercriminals targeting IT help desks using social engineering tactics and AI voice cloning tools to deceive their targets.-The use of audio deepfakes also allows threat actors to make it much harder to verify the caller’s identity remotely, rendering attacks where they impersonate executives and company employees very hard to detect.
- While the HHS shared advice specific to attacks targeting IT help desks of organizations in the health sector, the following also very much applies to CEO impersonation fraud attempts:
- Require callbacks to verify employees requesting password resets and new MFA devices.
- Monitor for suspicious ACH changes.
- Revalidate all users with access to payer websites.
- Consider in-person requests for sensitive matters.
- Require supervisors to verify requests.
- Train help desk staff to identify and report social engineering techniques and verify callers’ identities.
As always, Advanced is proud to be here for all your security needs. Reach out now to determine how you can improve your security posture and keep your business running!
- April 2024 Security Updates
- April 2024 Patch Tuesday: Three Critical RCE Vulnerabilities in Microsoft Defender for IoT
- Windows Security Surprise As Microsoft Confirms 90 New Vulnerabilities
- Telegram fixes Windows app zero-day used to launch Python scripts
- Roku warns 576,000 accounts hacked in new credential stuffing attacks
- LastPass: Hackers targeted employee in failed deepfake CEO call
- Over 15,000 hacked Roku accounts sold for 50¢ each to buy hardware



