
November 2023
- Patch Tuesday – 11/14
- Windows Server 2012 Officially End Of Support
- ICBC Hack Disrupts Wall Street
- Citrix Bleed Exposes Tens of Thousands Of Businesses To Attack
- Targeted Casino Attacks Continue
- Boeing Holds Firm Against Lockbit
- Australian Ports Reeling Following Ransomware Attack
- Legality and Morality of Paying Ransomware Called Into Question
As always, Advanced is proud to be here for all your security needs. Reach out now ([email protected]) to determine how you can improve your security posture and keep your business running smoothly.
– The Advanced Security Task Force
| Patch Tuesday – 11/14 |
The 2nd Tuesday of every month is Patch Tuesday! Every Patch Tuesday, Microsoft addresses security vulnerabilities in their products via a large deployment of software updates. This month’s Patch Tuesday addressed 67 security vulnerabilities. This round of updates also addresses 5 “Zero-Day Vulnerabilities” Zero-Day Vulnerabilities are publicly disclosed vulnerabilities that had no prior fix available.
Of the 58 vulnerabilities addressed, one was regarded as critical. This is in stark contrast to October’s Patch Tuesday, which addressed 104 Vulnerabilities, 12 of which were considered critical.
The Zero Day Vulnerabilities addressed can be seen below:
- CVE-2023-36036: Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
- CVE-2023-36033: Windows DWM Core Library Elevation of Privilege Vulnerability
- CVE-2023-36025: Windows SmartScreen Security Feature Bypass Vulnerability
- CVE-2023-36413: Microsoft Office Security Feature Bypass Vulnerability
- CVE-2023-36038: ASP.NET Core Denial of Service Vulnerability
The critical vulnerability addressed can also be seen below:
- CVE-2023-36397: Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability
Advanced deploys patches to all environments as a priority following a testing phase. The criticality of security updates is determined by several factors, primarily the ease of exploitability by threat actors and if the vulnerability has been seen exploited in the wild.
| Windows Server 2012 Officially End Of Support |
- On October 10th, Windows Server 2012 and Windows Server 2012 R2 officially reached end of support. This means the operating system will no longer receive critical security patches.
- Windows Server 2012 is considered one of the most popular server operating systems in the world. The retirement is expected to usher in a new wave of threat actors looking to take advantage of deprecated security features.
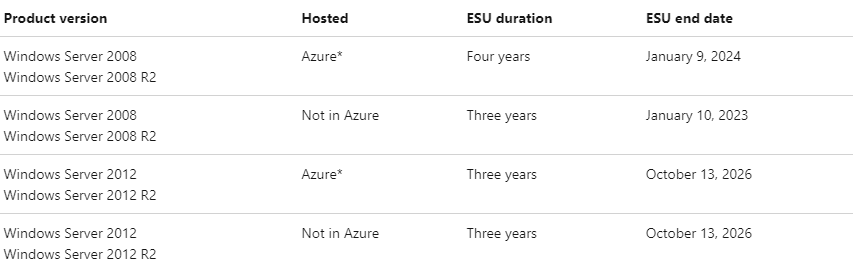
- Those looking to extend coverage to receive critical patches can subscribe to Extended Security Updates (ESUs). ESUs provide up to 3 years of additional coverage for patches deemed ‘Critical’ and ‘Important’ by Microsoft.
- Servers hosted in Azure are eligible for free ESUs until October 13th, 2026. Servers not hosted in Azure are eligible for ESUs until October 13th, 2026 through purchase of an ESU subscription.
- Advanced recommends clients take immediate action on any out-of-date operating systems. For more information on how these changes can affect your environment, reach out to [email protected].
| ICBC Hack Disrupts Wall Street |
- China’s biggest lender, the Industrial and Commercial Bank of China, experienced a severe cyber hack in their U.S. based office on November 9th. This caused extensive disruptions including email failure, leading employees to temporarily switch to Google mail.
- The blackout temporarily left the brokerage owing BNY Mellon $9 billion, far exceeding its net capital, creating concerns about its ability to meet claims promptly.
- ICBC’s New York unit received a cash injection from its Chinese parent to repay BNY and manually processed trades with BNY’s assistance.
- ICBC aimed to resume normal business by working with a cybersecurity firm, MoxFive, but this process was expected to take several days. Messages and documents were exchanged manually via USB Flash drives during recovery efforts.
- The attack raised concerns about the resilience of the $26 trillion Treasury market, potentially influencing regulatory discussions about cybersecurity and centralized clearing for trades.
- Hacker group ‘Lockbit’ has claimed responsibility for the attack, even stating ICBC paid a ransom for assistance in recovery. These claims have not been confirmed by ICBC at this time.
| Citrix Bleed Exposes Tens of Thousands Of Businesses To Attack |
- Citrix recently published an advisory of a critical vulnerability on their Netscaler ADC and Gateway Products. These devices, used to broker and authenticate remote sessions through Citrix, could be manipulated to reveal sensitive data.
- Through specially crafted HTTP packets, threat actors could leak system memory, exposing session cookies and enabling access without use of multi-factor authentication. This vulnerability was immediately regarded as critical. An example of this attack can be seen below.
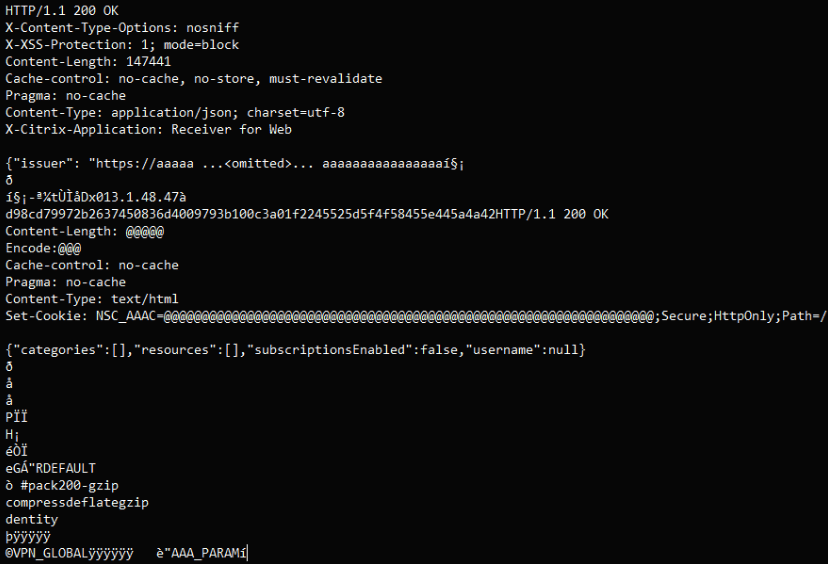
- In this instance, session tokens are replaced with the character “@”, indicating a patch has been applied to this Netscaler to hide this sensitive information
- Post exploitation, threat actors can deploy malicious software to internal devices and compromise entire networks in a matter of minutes. Forensics have indicated this was used to compromise ICBC.
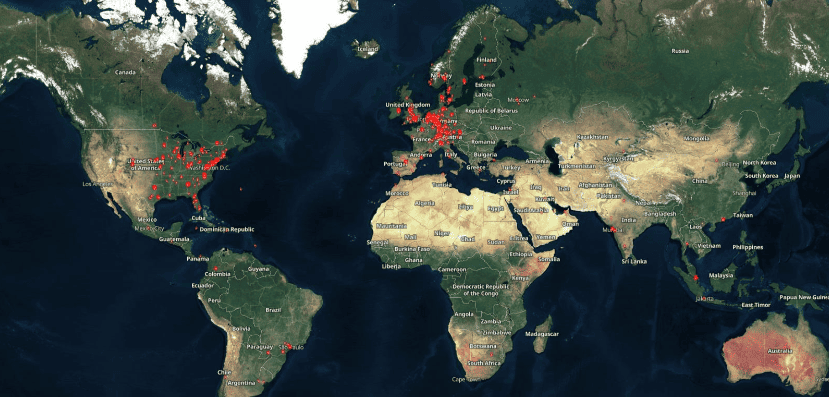
- Citrix recommends administrators apply patches and check for malicious activity immediately. Reports indicate more than 10,000 devices are still exposed, primarily in the US and Europe. A map of vulnerable servers can be seen below.
- Advanced clients had updates applied as soon as they became available on October 10th. Additional mitigations were then applied October 23rd per vendor recommendations.
| Targeted Casino Attacks Continue |
- Singapore-based luxury resort Marina Bay Sands reported they have uncovered evidence of a cybersecurity incident in late October.
- Per the report, the incident exposed personally identifiable information (PII) of roughly 665,000 customers.
- Exposed PII included customer names, email addresses, phone numbers, country of residence, and membership numbers.
- While no credit card or social security information was stolen, consultants believe the PII may be sold in bunches for use by social engineers for phishing scams. Those who have been impacted will be contacted and advised to be particularly alert.
- This incident comes less than a month after reported incidents at USA based casinos MGM and Caesars, both of which resulted in losses estimated to be in the hundreds of millions of dollars. Investigators have advised those in the casino and hospitality industry to be vigilant as these attacks continue.
| Boeing Holds Firm Against Lockbit |
- Boeing was recently listed on Ransomware Gang LockBit’s public website, claiming that a tremendous amount of data had been stolen, and payment was needed to prevent release.
- Lockbit will post companies under siege on its forum. The group also provides a countdown timer until data is released if the ransom is not paid.
- Boeing was then delisted, with the forum moderator reporting ‘negotiations were underway for payment’. Several days later, Boeing was relisted on the site.
- At 8:30 AM UTC on November 10th, roughly 40 GB worth of proprietary data became available for download. The forum post can be seen below.
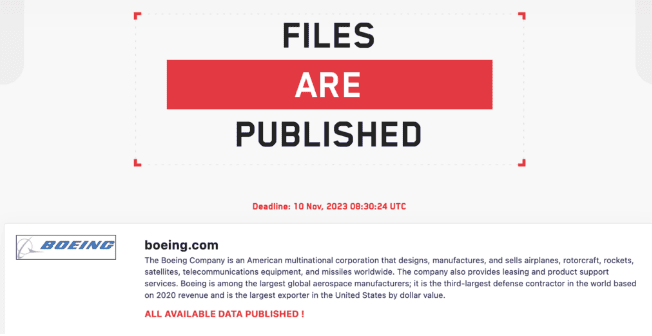
- Boeing has confirmed they are aware of the breach and have reassured the public flight safety is not at risk. They have not disclosed how the information was leaked at this time.
- This is the latest in a long series of attacks over by the LockBit ransomware gang. They have been attributed to over 1700 attacks since January 2020, accumulating approximately $91 Million dollars in ransomware payments.
| Australian Ports Reeling Following Ransomware Attack |
- Australia’s top container terminal operator, DP World, suffered a cyberattack causing major disruptions at key Australian ports.
- DP World handles 40% of the nation’s container trade and was brought to a standstill following an attack on Friday, November 10th.
- An estimated 30,000 shipping containers remain unmoved at the time of writing. Estimated damages exceed several million dollars due to the containment of time sensitive goods.
- DP World hasn’t disclosed specifics about the cyberattack itself, although it was initially reported as not being a ransomware attack. Citrix Bleed has been believed to be the root cause, but these reports have not been confirmed.
- Supply chain attacks can dramatically disrupt businesses at a global scale and are thus very lucrative targets for attackers. Japan’s largest maritime port, in Nagoya, was disrupted by a ransomware attack in July.
- BBC reported in 2022 that ransomware attack attempts on shipping ports have nearly doubled since the beginning of COVID. Regulatory changes have been proposed for mandatory auditing for cyber resilience to protect the worldwide flow of trade.
- Remediation is expected to continue for some time, and initial estimates gauge full recovery to be complete within a month.
| Legality and Morality of Paying Ransomware Called Into Question |
- An on-demand moving platform, Dolly.com, fell victim to a cyber attack in September and was contacted by the threat actor to pay a ransom.
- Dolly paid this ransom as requested but the threat actors exposed the information on public forums anyway. Dumped information can be seen below.
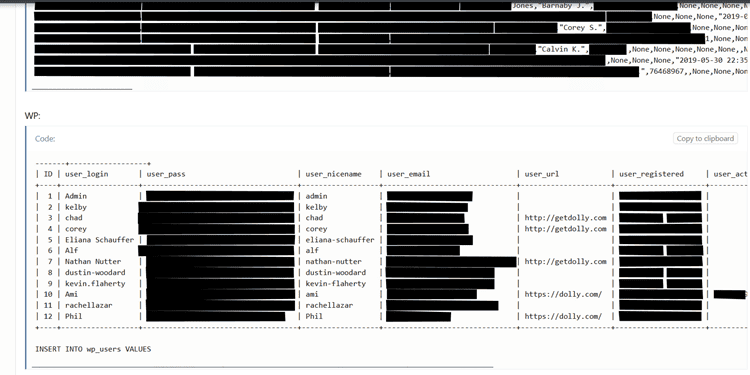
- This raises difficult questions on the morality and legality of paying ransoms to known international threats, as even when paid, there is no guarantee a criminal organization will adhere to their side of the agreement.
- For this reason, the U.S. Department of Treasury’s Office of Foreign Assets Control (OFAC) and the Financial Crimes Enforcement Network (FinCEN) declare it illegal to pay a ransom in most cases.
- OFAC explains, “Ransomware payments made to sanctioned persons or to comprehensively sanctioned jurisdictions could be used to fund activities adverse to the national security and foreign policy objectives of the United States.”
- This is a groundbreaking statement for cybercrime response, as paying established international threat actors can carry civil penalties and even prosecution. This is classified as funding cyber terrorism and possibly financially aiding other countries’ malicious efforts.
- This controversy came into question November 7th, when digital solutions company MeridianLink fell victim to a cyber-attack. After failing to disclose this breach to the SEC, the threat actors ‘ALPHV’ reported the breach to the SEC directly. The post can be seen below.
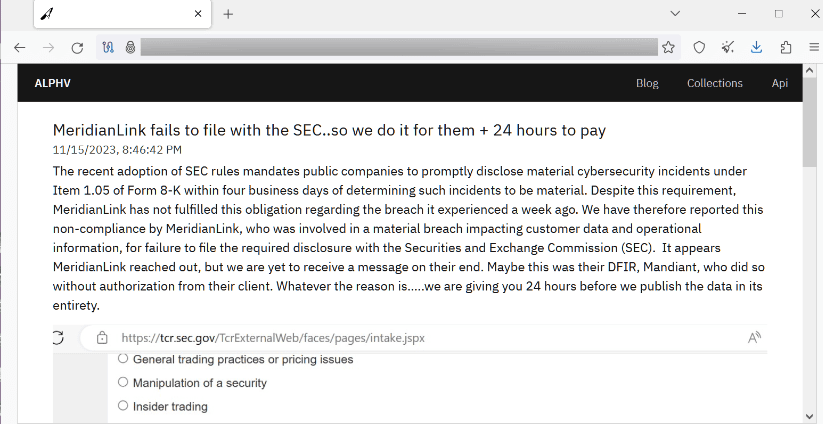
- Filing a K-8 form following a breach is mandatory for a publicly traded company. This further incentivizes victims to involve the government as fast as possible and discourage cover ups.
- Private companies should follow suit and never pay a ransom, as there is no guarantee of recovery once payment is made. Trusting anonymous threat actors already engaged in illegal activities is ill-advised, per the SEC.
- Cyber Insurance is recommend to mitigate the damage of a cyber-attack and cover potential cost for remediation. In rare circumstances, the government can approve paying a ransom on a case-by-case basis.
Sources:
- Microsoft Security Update Guide
- Windows Server 2012
- World’s Biggest Bank Has to Trade Via USB Stick After Hack
- Thousands of Servers Exposed by Citrix Bleed Vulnerability
- Singapore’s Marina Bay Sands says 665,000 customers had data stolen during cyberattack
- LockBit hackers publish 43GB of stolen Boeing data following cyber attack
- DP World hack: port operator gradually restarting operations around Australia after cyber-attack
- Dolly.com pays ransom, attackers release data anyway
- MeridianLink confirms cyberattack after ransomware gang claims to report company to SEC
- Paying Ransom On a Ransomware Attack Is Illegal



