May 2024
- Patch Tuesday – 5/14
- Threat Grading Overview
- Vendor Patch Advisories
- Threat Breakdown: The Return of Revenge Remote Access Trojan
- Looking Back: WannaCry – The Anniversary of the World’s Largest Ransomware Attack
- BreachForums: The Downfall of the World’s Most Prolific Stolen Data Marketplace
- Hypercharger EV Chargers Default Credentials Vulnerability
- Default Password Risks
As always, Advanced is proud to be here for all your security needs. Reach out now ([email protected]) to determine how you can improve your security posture and keep your business running!
– The Advanced Security Task Force
| Patch Tuesday – 5/14 |
The 2nd Tuesday of every month is Patch Tuesday! Every Patch Tuesday, Microsoft addresses security vulnerabilities in their products via a large deployment of software updates. This month’s Patch Tuesday addressed 61 security vulnerabilities. The full list can be seen here.
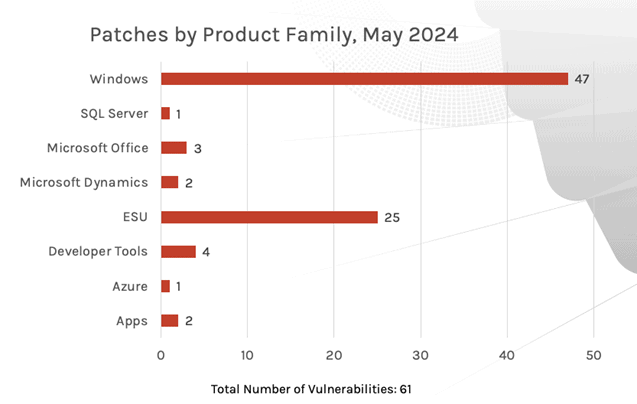
Windows products received the most patches this month with 47, followed by Extended Security Updates (ESU) with 25 and Developer Tools with 4.
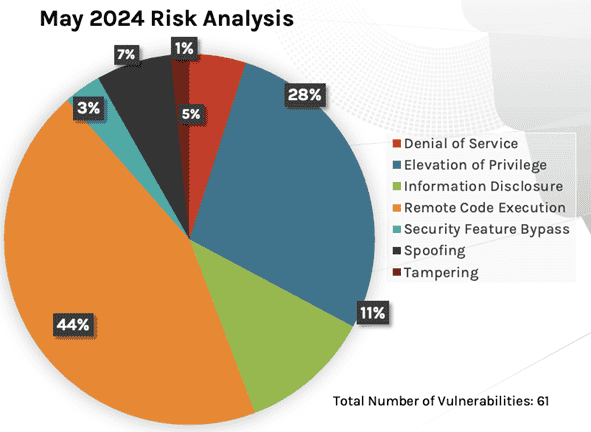
Of the 61 vulnerabilities addressed, 44% addressed Remote Code Execution Vulnerabilities, 28% addressed Elevation Of Privileges, followed by 11% for information disclosure.
| Threat Grading Overview |
Microsoft assesses threats based on the theoretical worst possible outcome were a vulnerability to be exploited. The assessment factors in how easily a vulnerability can be exploited, and what damage could be done.

Microsoft also references the Common Vulnerability Scoring System (CVSS), which assesses the severity of a vulnerability on a scale of 0 (Non-Issue) to 10 (Severe Issue) based on 5 key factors:
- Attack Vector: Describes how an attacker can exploit the vulnerability (e.g., local, adjacent network, or network).
- Attack Complexity: Reflects how difficult it is to exploit the vulnerability (e.g., low, medium, or high).
- Privileges Required: Indicates the level of privileges an attacker needs to exploit the vulnerability (e.g., none, low, or high).
- User Interaction: Specifies whether user interaction is required to exploit the vulnerability (e.g., none, required).
- Scope: Determines whether exploitation of the vulnerability impacts components beyond the vulnerable component.
Of these 61 vulnerabilities, 1 is considered Critical. Details on this vulnerability can be seen below:
- CVE-2024-30044: Microsoft SharePoint Server Remote Code Execution Vulnerability
This month’s patches also address two Zero Day Vulnerabilities. These are vulnerabilities being exploited in the wild that did not yet have a patch available
- CVE-2024-30040: Windows MSHTML Platform Security Feature Bypass Vulnerability
- CVE-2024-30051: Windows DWM Core Library Elevation of Privilege Vulnerability
| Vendor Patch Advisories |
Various companies have recommended critical patches for common software this month. Some of the most notable can be seen below:
- Adobe has released security updates for After Effects, Photoshop, Commerce, InDesign, and more.
- Apple backported an RTKit zero-day to older devices and fixed a Safari WebKit zero-day flaw exploited at Pwn2Own.
- Cisco released security updates for its IP phone products.
- Citrix urged Xencenter admins to manually fix Putty flaw, which can be used to steal an admin’s private SSH key.
- F5 releases security updates for two high-severity BIG-IP Next Central Manager API flaws.
- Google released an emergency update to fix their sixth zero-day of 2024.
- TinyProxy fixes a critical remote code execution flaw that was disclosed by Cisco.
- VMware fixes three zero-day bugs exploited at Pwn2Own 2024.
Apple-Specific Advisories
Apple has released security updates to address vulnerabilities in Safari, iOS, iPadOS, macOS, watchOS, and tvOS. A cyber threat actor could exploit some of these vulnerabilities to take control of an affected system. Users and administrators are encouraged to review the following advisories and apply necessary updates:
- Safari 17.5
- iOS 17.5 and iPadOS 17.5
- iOS 16.7.8 and iPadOS 16.7.8
- macOS Sonoma 14.5
- macOS Ventura 13.6.7
- macOS Monterey 12.7.5
- watchOS 10.5
- tvOS 17.5
Advanced deploys patches to all environments as a priority following a testing phase. The criticality of security updates is determined by several factors, primarily the ease of exploitability by threat actors and if the vulnerability has been exploited in the wild. Please reach out to [email protected] with any questions, comments or concerns on your patch management.
| Threat Breakdown: The Return of Revenge Remote Access Trojan |
- ‘Revenge’ malware belongs to Remote Access Trojans (RATs) malware family, enabling attackers to control infected PCs remotely and spy on users through features like keystroke logging and remote access to webcams and microphones.
- Discovered in 2016, Revenge RAT surged in popularity in 2019 with the “Aggah” campaign, targeting corporations and government structures globally. Its popularity stems from varied distribution methods akin to ransomware, robust features, and solid persistence mechanisms. Additionally, its open-source nature allows easy access for cybercriminals via underground forums.
- Revenge RAT is developed in Visual Basic and has expanded its capabilities over time, allowing cybercriminals to remotely manipulate files, access system memory, and record victim activities. Its evolution included distribution improvements, such as executing scripts in custom Blogspot pages, enhancing its potency in malicious campaigns.
- The malware has seen a resurgence in 2024, pushing security administrators to bolster defenses against the evolving threat. The infection chain can be seen below:
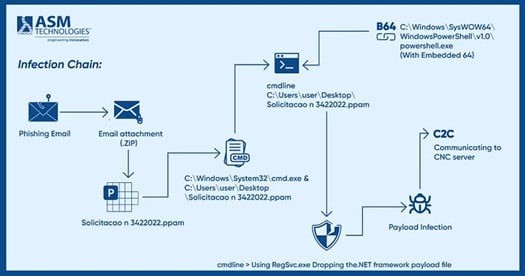
- Currently, malware creators are utilizing evasion strategies within PPAM files, embedding obfuscated content to heighten the complexity of analyzing the sample.
- PPAM (PowerPoint Add-in Macro-Enabled Presentation) files, while less recognized, are increasingly utilized in malware campaigns due to their appealing features such as macro-enabled functionality and obfuscation techniques.
- Typically, when opening .ppam files, a dialog message box prompts users to enable macros to access the file’s content. However, this action restricts navigation to other pages. Malware authors exploit this feature to their advantage by embedding malicious macros. An example of this feature before enabling macros can be seen below.
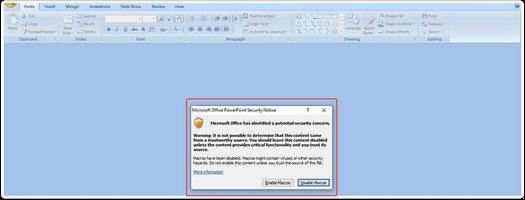
- The following output can be seen after enabling macros:
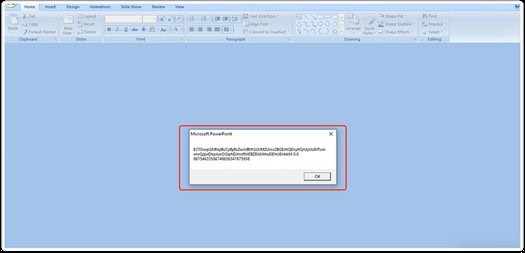
- This text is intentionally obfuscated to shroud the actions taking place. Upon opening the dialog box, the macro functions are activated, executing PowerShell commands in the background. These commands, encoded in base64, retrieve the payload file from the Firebase storage center and proceed to carry out malicious actions. The de-obfuscated powershell commands can be seen below:

- This command will attempt to retrieve and install a payload file from Firebase storage, a public repository. The installation token can also be seen in clear text to correlate the installation with the threat actor’s Command & Control (C&C) server.
- Once connected to the C&C server, the victim’s PC is under complete control of the threat actor. Threat actors can then engage in various activities, including:
- Unauthorized Remote Access: RevengeRAT grants attackers remote control over compromised systems, enabling them to execute commands and alter settings without user authorization.
- Information Theft: The malware pilfers sensitive data like credentials, keystrokes, and personal details, facilitating malicious activities such as identity theft and financial fraud.
- Surveillance Capabilities: RevengeRAT surveils user actions by capturing screenshots, recording audio/video, and logging keystrokes, furnishing attackers with insights into victim behavior.
- Persistence Mechanisms: The malware employs methods to sustain prolonged access to infected systems, ensuring continued operation and evasion of detection even after system restarts.
- Propagation and Potential Destructive Actions: Certain iterations of RevengeRAT may propagate to other networked systems and carry out destructive maneuvers such as file deletion or system manipulation, presenting a substantial threat to individuals and organizations alike.
| How do I protect myself from becoming a victim of Remote Access Trojans? |
- Keep Your Software Updated: Regularly update your operating system, software applications, and antivirus/antimalware programs. Security patches often address vulnerabilities that could be exploited by RATs.
- Use Strong Passwords and Multi-Factor Authentication (MFA): Create strong, unique passwords for your accounts and enable multi-factor authentication wherever possible. This adds an extra layer of security by requiring a second form of verification in addition to your password.
- Exercise Caution with Email Attachments and Links: Be wary of unsolicited emails, especially those containing attachments or links. Avoid opening attachments or clicking on links from unknown or suspicious sources, as they could be vectors for RATs. Verify unsolicited emails from trusted sources over the phone, as compromised email accounts may attempt to send malicious emails en masse.
- Install and Maintain Antivirus / Antimalware Software: Use reputable antivirus and antimalware software and keep it up to date. Regularly scan your system for malware and remove any detected threats promptly.
| Looking Back: WannaCry – The Anniversary of the World’s Largest Ransomware Attack |
- May 12, 2017 is a day that lives in infamy in the minds of System Administrators across the world. An estimated 300,000 PCs across 150 countries fell victim to WannaCry, a simultaneous ransomware attack that disrupted global health, banking, and food industries. Victims were met with the screen below on their PCs:
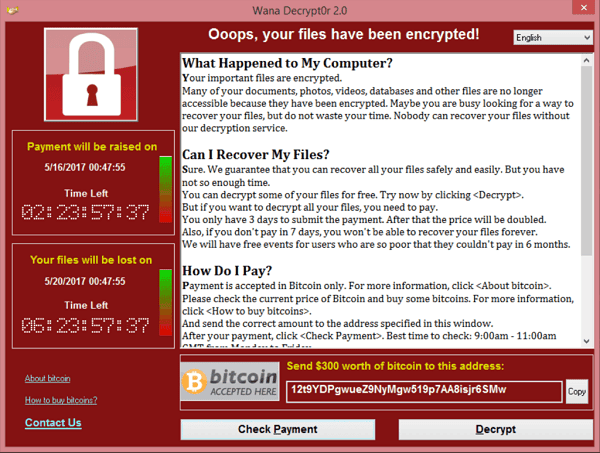
- The ransomware targeted vulnerable Windows devices Server Message Block (SMB) file-sharing protocol. In a cruel twist of fate, the exploited vulnerability (MS17-010) had actually been addressed in a Microsoft patch a month earlier.
- The ransom started at $300 if the victim paid within 6 hours, then it doubled to $600 for up to 3 days later. The ransomware threatened to delete the files completely if the ransom was unpaid within a week and included an ominous countdown timer to files being deleted.
- The WannaCry ransomware spread by searching affected networks for devices that accept traffic on TCP port 445, which indicates SMB is configured to run on the system. This is done by performing a port scan. After confirming the presence of SMB, the infected PC initiates an SMBv1 connection to the device. A buffer overflow is then used to take control of the system and install the ransomware.
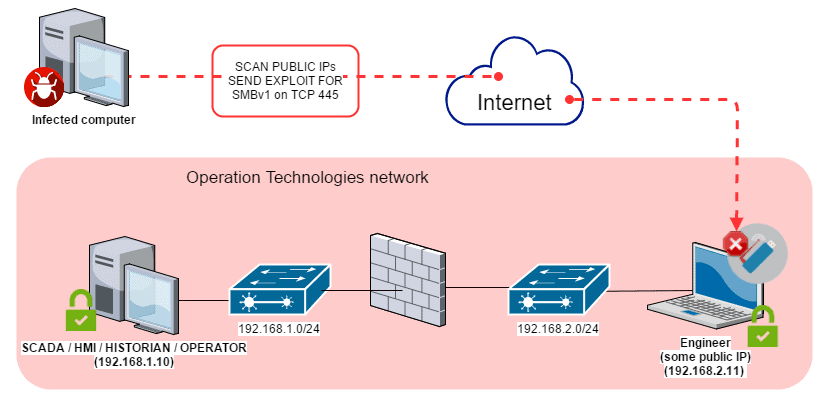
Encryption Timeline:
- May 12, 7:44 AM UTC: First detections of WannaCry are reported in Asia.
- May 12, 3:03 PM UTC: Reverse engineering of the software found a peculiar ‘kill switch’ embedded in the encryptor software: a callout to an unregistered domain name. When executed, the WannaCry malware first checks the internet for the presence of a specific URL: ( iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com); if it is not found, then the ransomware encrypts the computer’s data. If it is found, the worm will delete itself. A quick-thinking engineer purchased and registered this domain for $10.69. This effectively halted the spread of WannaCry across the globe.
- May 14: A first variant of WannaCry appeared with a new and second kill switch. This kill switch URL was registered and activated by another technician on the same day.
- May 15: A second variant of WannaCry is reported in the wild. This kill switch URL is quickly discovered and registered by Check Point threat intelligence analysts.
- May 19: It is reported that hackers were trying to use a Mirai botnet variant to initiate a distributed denial-of-service (DDoS) attack on WannaCry’s kill switch domain with the intention of knocking it offline, initiating encryption on infected devices.
- May 22: Engineers protect the kill switch domain by implementing a cached version of the site to withstand DDoS attacks.
Damage and Unclear Origins:
- Records of ransomware payments through Bitcoin transactions total roughly $130,000 USD. Estimated damages exceed $8 Billion USD.
- WannaCry used what was originally the National Security Agency 0-day ETERNALBLUE and DOUBLEPULSAR exploits.
- EternalBlue was created by the NSA, which had spent years searching for potential vulnerabilities in Microsoft software. When the organization finally found a weakness in the SMBv1 protocol, the NSA developed EternalBlue to take advantage of that vulnerability.
- Instead of alerting Microsoft to the risks its users faced, the NSA used EternalBlue to aid in antiterrorism and counterintelligence operations for half a decade.
- In the summer of 2017, a malware group calling themselves the ShadowBrokers were able to infiltrate the NSA and steal EternalBlue.
- It is unclear how the ShadowBrokers may have gotten their hands on these NSA tools – conspiracy theories range from a contractor leak to Russian counter-espionage.
- More than half a decade later, WannaCry remains a constant reminder of the importance of patching and the potential dangers of withholding dangerous software exploits
| BreachForums – The Downfall of the World’s Most Prolific Stolen Data Marketplace |
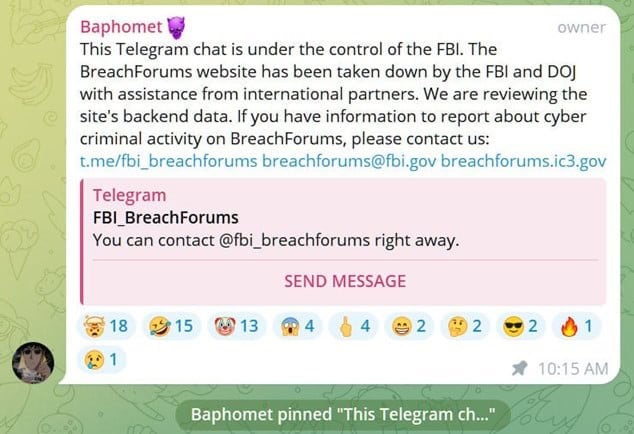
- The FBI has seized the notorious BreachForums hacking forum. The popular hacker site was used for the sale of stolen corporate data and malicious software since March 2022, following the takedown of Raidforums.
- The seizure occurred on Wednesday morning, soon after the site was used last week to leak data stolen from a Europol law enforcement portal.
- The website is now displaying a message stating that the FBI has taken control over it and the backend data, indicating that law enforcement seized both the site’s servers and domains.

- The FBI has also seized the site’s Telegram channel, with law enforcement sending messages stating it is under their control.
- One of the messages posted to the seized Telegram channel by law enforcement came directly from the site administrator account, possibly indicating that the threat actor was arrested, and his devices are now in the hands of law enforcement.
| Hypercharger EV Chargers Default Credentials Vulnerability |
- Alpitronic Electric Vehicle Chargers across the globe are susceptible to a vulnerability that exposes an administrative access portal to the internet. This portal is protected with publicly available default credentials unless manually reconfigured.
- When informed of these vulnerabilities, Alpitronic, in conjunction with and/or on behalf of affected clients, disabled the interface on any exposed devices. All clients were contacted directly and reminded that the interface is not intended to be visible on the public Internet and that default passwords should be changed. The public interface and credentials can be seen below:
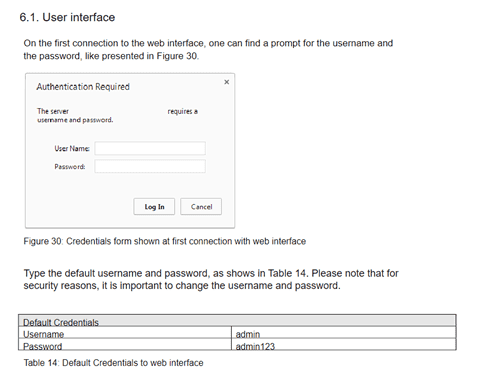
- Initial reports estimate roughly 1/3rd of internet facing Hyperchargers were accessible with these default passwords. The interface allowed reconfiguration of the chargers, including options related to the power supply and payment. In some cases, payment data was accessible. (Alpitronic pointed out that the data did not contain personal data and only the last four digits of credit cards.)
-Within a day, most devices were no longer accessible from the Internet. “In the future, individual passwords will be assigned to each charging station at the factory,” said Alpitronic spokesperson Daniela Halbwidl. Furthermore, Alpitronic plans to implement changes so the configuration interface will no longer be accessible from the public Internet by default.
| Default Password Risks |
- In an increasingly connected world, the use of default credentials on internet facing devices is more serious than ever. Home/Business Security Cameras are believed to be the biggest and most dangerous offender, with an estimated 380,000 publicly accessible streams running 24 hours a day.
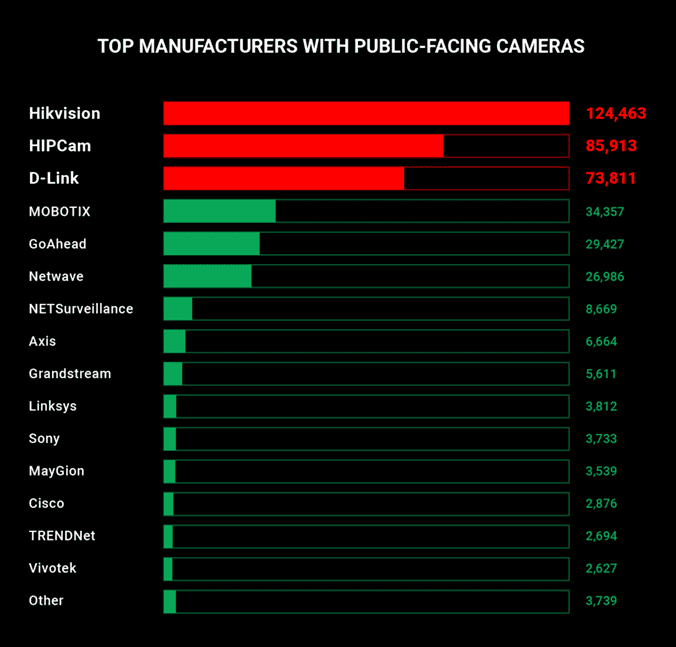
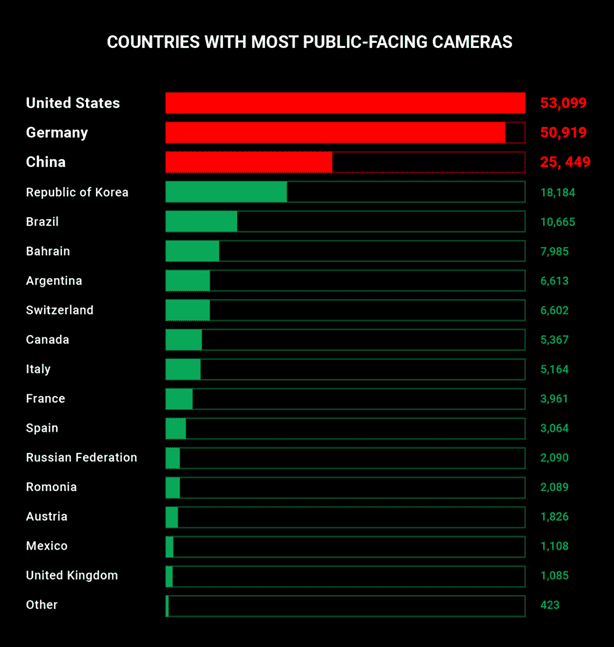
- Ease of setup is a major contributor to this lack of security, as most vendors do not require password resets or secure networks for functionality.
- The U.K. National Cyber Security Centre (NCSC) is tackling this issue head-on, forcing manufacturers of smart devices to comply with new legislation that prohibits them from using default passwords, effective April 29, 2024.
- The law also aims to enforce a set of minimum-security standards across the board to prevent vulnerable devices from being corralled into a Distributed Denial Of Service (DDoS) botnet like Mirai. The law targets the following products that can be connected to the internet:
- Smart doorbells, baby monitors, and security cameras
- Cellular tablets, smartphones, and game consoles
- Wearable fitness trackers (including smart watches)
- Smart domestic appliances (such as light bulbs, plugs, kettles, thermostats, ovens, fridges, cleaners, and washing machines)
| How can I prevent unauthorized access to my Internet Of Things (IoT) Devices? |
- Change Default Passwords: Always change default passwords to unique, strong ones. Default passwords are often easy for hackers to guess.
- Keep Firmware Updated: Regularly update the firmware of your IoT devices. Manufacturers release updates to fix vulnerabilities and improve security.
- Use Encryption: Ensure that your IoT devices use encryption protocols like WPA2 for Wi-Fi connections and HTTPS for communication with servers. Encryption helps protect data in transit.
- Segment Your Network: Create a separate network for your IoT devices, isolating them from your main network. This prevents attackers from gaining access to sensitive data if one device is compromised.
- Disable Unused Features: Disable any unnecessary features or services on your IoT devices. This reduces the attack surface and minimizes the risk of exploitation.
- Implement Network Security: Use firewalls and intrusion detection systems to monitor and control network traffic. This helps detect and block suspicious activity.
- Enable Two-Factor Authentication: If available, enable two-factor authentication for accessing IoT device accounts. This adds an extra layer of security beyond passwords.
- Regularly Monitor Devices: Monitor the activity of your IoT devices for any unusual behavior. This can help detect potential security breaches early.
- Secure Physical Access: Keep physical access to IoT devices restricted to authorized individuals. Physically securing devices prevents tampering and unauthorized access.
- Read Privacy Policies: Before purchasing IoT devices, review their privacy policies to understand how your data will be collected, stored, and shared. Choose devices from reputable manufacturers with transparent privacy practices.
Sources:
- May 2024 Security Updates
- May 2024 Patch Tuesday: Two Zero-Days Among 61 Vulnerabilities Addressed
- Deep Diving into RevengeRAT
- How to analyze Revenge with ANY.RUN
- How Does WannaCry Ransomware Work?
- How did the WannaCry ransomworm spread?
- FBI seizes BreachForums after arresting its owner Pompompurin in March
- EternalBlue: What it is and how it works
- The Security of IP-Based Video Surveillance Systems
- New U.K. Law Bans Default Passwords on Smart Devices Starting April 2024