
August 2023
- Patch Tuesday – 8/8
- When In Doubt, Talk It Out! The Importance Of Asking
- Password Management – The Convenience You’ve Been Looking For
- Annual Phishing By Industry Threat Report
- LinkedIn Compromise Emphasizes The Importance of MFA
- Dallas Pays Out For Ransomware Recovery
As always, Advanced is proud to be here for all your security needs. Reach out now ([email protected]) to determine how you can improve your security posture and keep your business running smoothly.
| Patch Tuesday – 8/8 |
The 2nd Tuesday of every month is Patch Tuesday! Every Patch Tuesday, Microsoft addresses security vulnerabilities in their products via a large deployment of software updates. This month’s Patch Tuesday addressed 76 security vulnerabilities, 6 of which were considered critical.
Advanced deploys patches to all environments as a priority following a testing phase. The criticality of security updates is determined by several factors, primarily the ease of exploitability by threat actors and if the vulnerability has been exploited in the wild. The critical vulnerabilities, and their details, can be seen below:
- CVE-2023-35385 – Microsoft Message Queuing Remote Code Execution Vulnerability
- CVE-2023-36910 – Microsoft Message Queuing Remote Code Execution Vulnerability
- CVE-2023-36911 – Microsoft Message Queuing Remote Code Execution Vulnerability
- CVE-2023-29328 – Microsoft Teams Remote Code Execution Vulnerability
- CVE-2023-29330 – Microsoft Teams Remote Code Execution Vulnerability
- CVE-2023-36895 – Microsoft Outlook Remote Code Execution Vulnerability
| When In Doubt, Talk It Out! The Importance Of Asking |
In an era dominated by digital communication, email has revolutionized the way we connect, work, and share information. Yet, this convenience comes with a catch: the proliferation of cyber threats, including phishing, spoofing, and scams, puts our sensitive data and personal security at risk. To navigate this perilous landscape, use a simple yet powerful approach: “When in Doubt, Talk it Out!”
If something feels ‘off’ about an email, don’t be afraid to involve your coworkers, supervisors, or IT team to verify legitimacy. Security is everyone’s responsibility!
Consider the following common scenarios:
- Scenario 1: I’ve received a suspicious email from someone claiming they have executive approval for confidential information. I don’t want to get in trouble for insubordination!
- This is a very common tactic for scammers, in which they will emphasize they have approval from a superior to gain access to restricted information. You should always confirm this approval with a supervisor via email, over the phone or in person before providing any information.
- Scenario 2: I’ve received a strange email from a coworker, requesting to update their banking information. I want to help them!
- One of the most-seen scams today revolves around targeting HR staff to redirect paychecks to a new account. This can be prevented by reaching out to that employee over the phone, or in person if possible, and confirming the changes to be made. Banking changes should never be made without verbal approval.
- Scenario 3: I don’t recognize this sender, but the subject says the email attachment is critical. I don’t want to neglect a potential emergency!
- Scammers will frequently try to impose a sense of urgency to discourage end users from thinking things through. If something seems off, it usually is! Call up your IT department to receive a second set of eyes and verify legitimacy before opening any attachments from unknown sources.
| Password Management – The Convenience You’ve Been Looking For |
- In the modern age, safely keeping track of passwords can be an impossible task. Based on a report from NordPass, the average user has 100 passwords to remember for various accounts. This is unsustainable without practicing unsafe password hygiene, such as re-using passwords or only changing a numerical value on multiple iterations. This is unadvisable, as any one account compromise or data breach will quickly cascade into the compromise of other accounts.
- Advanced strongly recommends the use of password management software to keep accounts as safe as possible.
- Password Managers encourage strong, randomized passwords. These passwords are documented behind one multi-factor protected password. This prevents password re-use and minimizes the impact of vendor data breaches.
- Most password managers integrate directly into your web browser, allowing easy access for all cloud applications.
- Advanced offers large scale password management for enterprises. Reach out to [email protected] for more details to keep your team secure!
| Annual Phishing By Industry Threat Report |
- Each year, a Phishing By Industry Benchmark Report is released. This is used by IT teams for data analysis on the effectiveness of security awareness training.
- 2023’s report analyzes data from 35,000 organizations, 12.5 million users, and 32.1 million individual phishing tests. The report breaks data down between 3 sizes of companies (<250 users, 250-999 users, and >1000 users), and three levels of training (No training, within 90 days of training, and 12 months of continuous training). Susceptibility to phishing attacks was measured based on how many end users engaged with simulated phishing emails.
- Small organizations saw Healthcare & Pharmaceuticals as the most prone industry to phishing attacks, with 33% of users engaging with phishing emails, followed by 31.6% for Retail/Wholesale, and 31.2% for Education. Legal was the least prone small sized industry, with only 25.6% engagement.
- Mid-sized organizations also saw Healthcare & Pharmaceuticals being the most susceptible to phishing attacks, with 35.8% engagement, followed by Energy & Utilities at 33.6%, and 31.2% for Construction. Government was the least prone industry across mid-sized organizations, with 26.3% engagement.
- Large organizations saw a staggering 53.2% engagement for Insurance industries, followed by 51.4% for Energy & Utilities, and 48.2% for Consulting. Government was the least prone industry across large organizations, with 25.7% engagement.
- Overall, companies with no security awareness training saw 33.2% of users engage with malicious emails. Companies within 90 days of training saw engagement of 18.5%, and companies with one year or more of continuous training saw engagement of only 5.4%.
- 74% of all breaches include the human element, and threat actors continue to target end users with phishing campaigns for the vast majority of intrusion attempts. Security awareness training was shown to improve phishing simulation scores by an average of 82%.
- The report breaks down individual performances by region and sector, as long as best practices for engagement. The full report can be downloaded here.
- Advanced strongly recommends enrolling in security awareness training to empower employees as the first line of defense against threats to your organization. For more information, reach out to [email protected].
| LinkedIn Compromise Emphasizes The Importance of MFA |
- Over the last 90 days, security analysts have observed a significant rise in reports of compromised LinkedIn accounts.
- While LinkedIn is yet to make an official comment on the coordinated attacks, Google trends paint a grim picture:
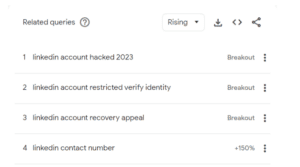
- The above image shows Google search trends compared from July 2023 to August 2023. The percentage indicates how frequently a term was Googled relative to the previous month. The term “Breakout” in place of a percentage indicates the search term grew by more than 5000%.
- Compromised users have vented frustrations with account recovery publicly. Users reported receiving an email that a new recovery email was added to their account. This helps the threat actor maintain persistent access to the compromised account and makes recovery efforts almost impossible. The recovery email is always a pseudo-randomized rambler.ru domain. The Russian email domain is well known for use by threat actors.

- Targeted accounts without MFA enabled report very frequent compromises. Targeted accounts with Multi-Factor Authentication enabled have not been compromised but have reported continuous prompts for sign on.
- Multi-Factor Authentication enforces verifying at least 2 of 3 authentication methods when accessing an account: Something you know (like a password), something you have (like a mobile device) or something you are (via biometrics). As the threat actors are believed to be gaining access via compromised passwords, enforcing authentication through other means, such as a prompt on your mobile device, will prevent unauthorized access.
- LinkedIn users are strongly advised to enable MFA for account protection in the wake of these ongoing attacks. Details on how this can be done can be seen here.
| Dallas Pays Out For Ransomware Recovery |
- Dallas, TX reported paying out $8.6 Million following a ransomware attack between April and May of this year.
- The funds will primarily go to vendors for emergency recovery and monitoring services.
- The attack led to the exposure of personal data of more than 26,000 individuals, and fines may follow as the investigation continues.
- Advanced strongly advises reviewing services for Cyber Liability Insurance and determining if it is the right answer for your organization. For guidance, please reach out to [email protected].
Sources:



